Other Parts Discussed in Thread: CC3220SF, UNIFLASH, CC3235SF
Tool/software:
Hi Ti,
I am posting in the forums regardging errors I am facing while building a custom catalog as my current requirentments require the use of ISRG root X1 to connect Hive mq tls but the current TI playground is too outdated and as such With the old Playground catalog we hit -468 (SL_ERROR_BSD_ESEC_UNKNOWN_ROOT_CA) to our MQTT broker.
based on some previous forums and having a spare launch pad with mcuCC3220SF as such decided to use that with uniflash 6.0.
Setup
-
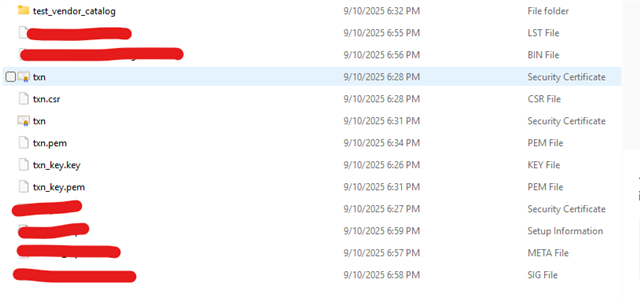
Device: CC3220SF LaunchPad (Secure), HW rev 49, MAC
e4:15:f6:66:e1:8c. -
OS/Tools: Windows 10, UniFlash v6.x (Advanced View)
-
SDK: SimpleLink CC32xx SDK 7.10.00.13
-
Service Pack loaded in UniFlash project:
sp_3.22.0.1_2.7.0.0_2.2.0.7.bin -
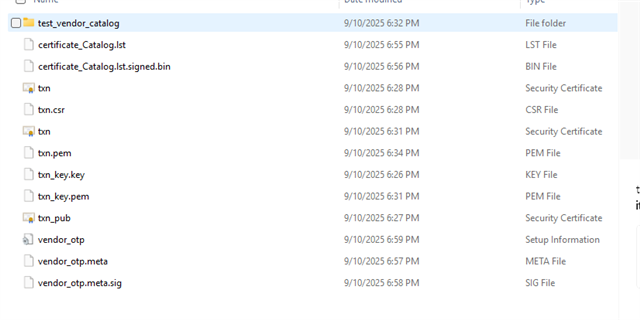
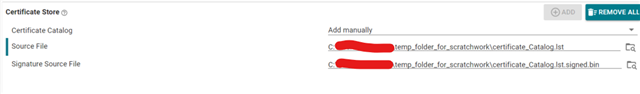
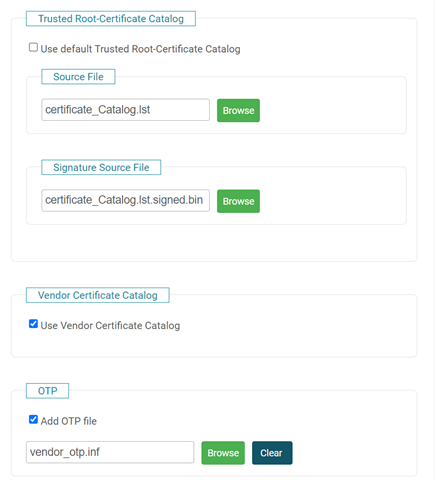
Goal: Update the Vendor Certificate Catalog to trust ISRG Root X1 (for MQTT/TLS to HiveMQ Cloud), and bind device(s) to our root.

What I followed (docs & forum references)
-
SWRU547A – Vendor Device Authentication With SimpleLink Wi-Fi
Exact steps (commands used)
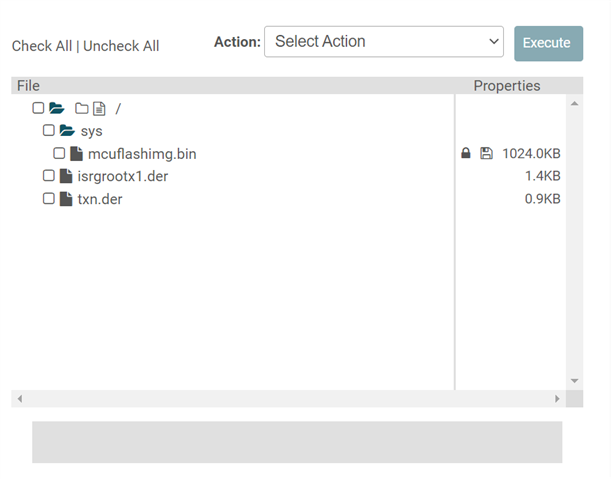
1) ISRG Root X1 in DER