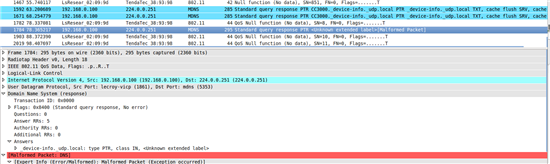
Hi,
i do a call like this
mdnsAdvertiser(1, "Martin", 6);
but get a return value of -67. What does the error mean? Does it need more than a connected AP to be successful?
(BTW: Using SP 1.24, but same with older SP)
mdnsAdvertiser is described here:
http://software-dl.ti.com/ecs/simplelink/cc3000/public/doxygen_API/v1.11/html/d2/d21/group__socket__api.html
Why is it described in socket API part, even when it seems not to be socket related? Why not in general WLAN api?
> "Return: On success, zero is returned, return SOC_ERROR if socket was not opened successfully, or if an error occurred."
Again here is a socket mentioned, but no socket as input nor as return parameter. Error in description?
Best regards,
Martin