2 Jan 2018, 9:30AM (CT)
FWs for WL6/7/8 were applied to linux-firmware mainline.
Please note that new Wilink6/7 service pack has been released.
The version is: R5SP9 and can be downloaded from the following link: https://git.ti.com/wl12xx/
It was pushed to the Linux main line, however this will take several days until it will be accepted.
You can either build the whole setup or get the changes only in the ti-utils repository for the FW and the hostap for the hostap changes.
To build the whole setup, download the Build utilities repository: tag ol_R5.SP9.01
You do not need to change the build script. Only change the setup-env to point to the latest SP:
export BUILD_VERSION="ol_R5.SP9.01"
08 Dec 2017, 5:00 PM (CT)
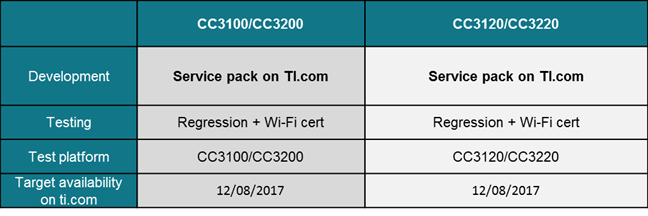
Key Reinstallation Attack patched Service Packs have been released for CC3100, CC3200, CC3120 and CC3220
They can be found here, respectively:
Thanks -
SimpleLink Wi-Fi Applications and Development Teams
===========================================
30 Nov 2017, 8:00AM (CT)
Please note that new Wilink8 NLCP service pack was posted to ti.com last night. This service pack includes the KRACK fixes for Hostapd and FW. Please find the location at:
http://www.ti.com/tool/WILINK8-WIFI-NLCP
29 Nov 2017, 1:50PM (CT)
We wanted to highlight the direct link for the Wilink8 MCP release that was made on 11/27.
17th Nov 2017, 4:30PM (CT)
Update for WiLink™ 8 products:
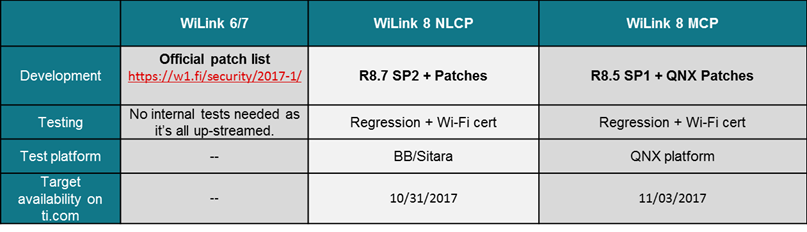
The NLCP package that was posted to the link below contains the WPA Supplicant patches as well as a required FW update. TI highly recommends that customers apply these patches and FW updates on top of the latest release R8.7SP2. This release is required for compliance to the latest RED certification for example and this is the release which TI tested against for the KRACK fixes. For completeness, the FW patch released for the KRACK fix is compatible with the only following releases:
-
- R8.6
- R8.6SP1
- R8.7
- R8.7SP1
- R8.7SP2
The MCP release package is now in final regression testing. The expectation is that this package will be posted to ti.com no later than 11/27. It will be released as a new service pack version: MCP8.5SP2. The FW released as part of this package is only compatible with MCP8.5SP1 and above. Again, older releases will have to be updated for both RED compliance and KRACK fix.
7th Nov 2017, 6:00PM (CT)
Update for WiLink™ 8 products:
A package for WL18xx devices will be on ti.com by tomorrow and will be accessible via this page:

6th Nov 2017, 4:30PM (CT)
Update for WiLink™ 8 products:
Vulnerability testing for the fixes is complete and final regression testing is wrapping up. Apologies for the delay, we fully expect to be releasing a package for WL18xx devices within the next few days.
Update for SimpleLink™ Wi-Fi products:
We expect no change in the schedule previously posted below.
24th Oct 2017, 4 PM (CT)
Description of the Issue:
-
- As previously noted, TI is aware of the recently discovered WPA2 issue and has confirmed that WPA2 supplicants used with TI WiLink™ 8, WiLink™7 , WiLink™ 6 and CC31xx/CC32xx products contain a vulnerability.
- The WPA2 supplicant (wpa_supplicant) is the portion of the code for the Network Processor (NWP) which implements key negotiation with the WPA Authenticator.
- Products that could be vulnerable to the attack allow the attacker to trick the target Wi-Fi product to re-install its security key.
- To exploit the vulnerability the attacker must be within Wi-Fi range of the target product. The attack cannot be performed remotely over the internet and is thus not easily scalable.
- Applications that use TLS protocols in addition to WPA2 encryption can prevent attackers from decoding or modifying traffic even if WPA2 security is broken. CC3xxx family of products offer built-in TLS security in addition to WPA2 support. WiLink™ can also take advantage of TLS protocols from the upper layer OS.
WilinkTM based Products:
-
- WiLink™ 8 : TI has identified a potential fix in the form of a supplicant software update for TI’s WiLink™ 8 (WL18xx). In lab tests TI has verified the vulnerability of the supplicant on WiLink™ 8 and that the proposed code fix resolves the problem. TI plans to perform regression tests on the proposed code fix and then publish instructions describing how to download and apply the fix. In addition TI plans to release a revised service pack with the code fixes already applied. The schedule for distribution of the instructions and revised service pack is shown below.
- WiLink™ 7 and WiLink™ 6 : The up-streamed code fix for the WPA2 supplicant is published and downloadable from the link shared below. Either apply patchesto your existing code base, or pull the latest from upstream.
- All generations of WiLink product from WiLink™6 to WiLink™ 8 use the same open-source hostap package.
- All hostap released patches can be applied with some minor adjustments to all projects.
(https://w1.fi/security/2017-1/)
SimpleLink CC31xx/CC32xx based Products:
-
- TI has identified a potential fix in the form of a supplicant software update for TI’s CC31xx/CC32xx products.
- In lab tests TI has verified the vulnerability of the supplicant on CC31xx/CC32xx and that the proposed code fix resolves the problem.
- TI is creating revised service packs based on the proposed code fix and will perform regression tests on the service packs.
- TI plans to release these service packs for CC3100/CC3200 and CC3120/CC3220 products.
- The schedule for development, testing and distribution of the service packs is available below.
18th Oct 2017, 4 PM (CT)
TI is aware of the recently discovered WPA2 issue and has confirmed that WPA2 supplicants used with TI WiLink™ 8 (WL18xx), WiLink™6 and CC31xx/CC32xx products are vulnerable.
WiLink™ 8 : TI has identified a potential fix in the form of a supplicant software update for TI’s WiLink™ 8 (WL18xx). In lab tests TI has verified the vulnerability of the supplicant on WiLink™ 8 and that the proposed code fix resolves the problem. TI plans to perform regression tests on the proposed code fix and then publish instructions describing how to download and apply the fix. In addition TI plans to release a revised service pack with the code fixes already applied. The schedule for distribution of the instructions and revised service pack should become available in the next three working days.
WiLink™ 6 : Same status as WiLink™ 8. TI plans to perform regression tests on the proposed code fix and then publish instructions describing how to download and apply the fix. The schedule for distribution of the instructions should become available in the next three working days.
CC31xx/CC32xx : TI has identified a potential fix in the form of a supplicant software update for TI’s CC31xx/CC32xx products. In lab tests TI has verified the vulnerability of the supplicant on CC31xx/CC32xx and that the proposed code fix resolves the problem. TI plans to create revised service packs based on the proposed code fix and perform regression tests on the service packs. TI plans to release service packs for CC3100/CC3200 and CC3120/CC3220 products. The schedule for distribution of the service packs should become available in the next three working days.
17th Oct 2017, 3 PM (CT)
TI is aware of the recently discovered WPA2 issue and has confirmed that WiLink 8 (WL18xx) and CC31xx/CC32xx devices are impacted.
TI has identified a fix in the form of a supplicant update for the WiLink 8, and TI is working on a service pack update for the CC31xx/CC32xx products.
These updates will be regression tested in TI labs ahead of release. More detail on the release format and schedules for specific parts will be forthcoming later this week.