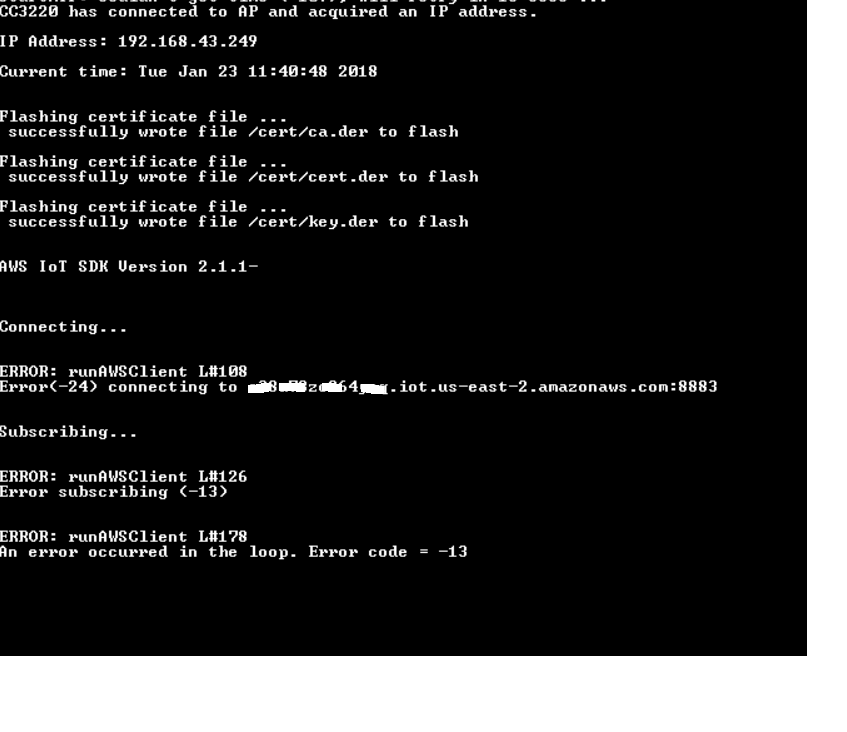
Tool/software: Code Composer Studio
Hello
Currently I am getting the following error.
I have tried solutions given for this issue in E2E community, but none of them really helped.
I don’t have much confidence in the way I have copy pasted the certificates in to CCS. If you have any documents that details the steps/things to take care with certificates, please share.
Basically, I have in total four certificates downloaded from AWS.
I am not sure, which one corresponds to root_ca_pem, client_cert_pem and client_private_key_pem in cert.h in CCS. And, do I need to change the certificates everytime if I make any changes in the AWS side?
Regards,
Reshmi