Tool/software: Linux
HI
we update the wl18xx driver to version R8.7_SP3 which contains an update to address the WPA2 vulnerability security issue(KRACK), but the WTS SVD-5.2.3 and SVD-5.3.1 test case still fail, following is detail message:
wl18xx driver:
[17:17:22]wlcore: wl18xx HW: 183x or 180x, PG 2.2 (ROM 0x11)
[17:17:22]wlcore: loaded
[17:17:22]wlcore: driver version: R8.7_SP3-dirty
wpa_supplicant:
wpa_supplicant -v
wpa_supplicant v2.6-devel-R8.7_SP3
Copyright (c) 2003-2016, Jouni Malinen <j@w1.fi> and contributors
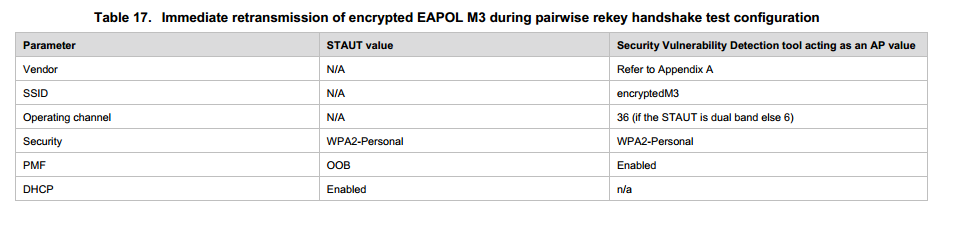
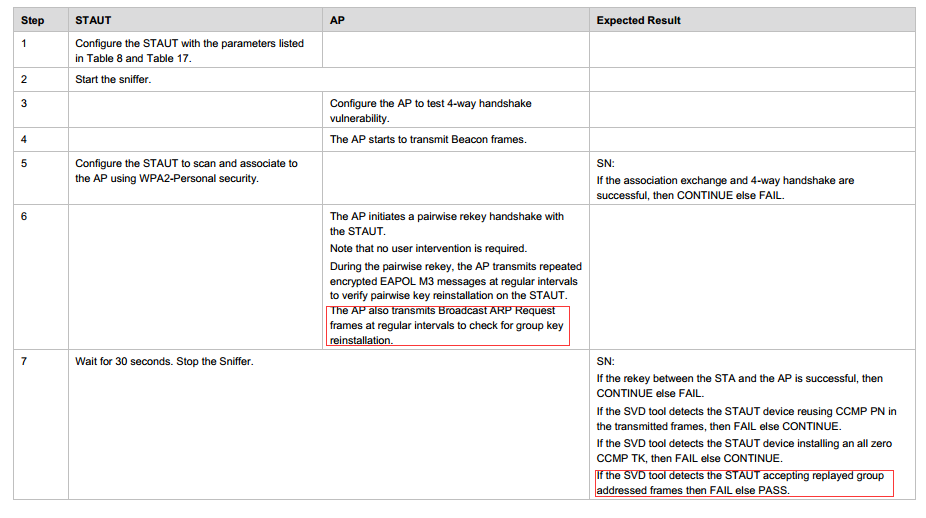
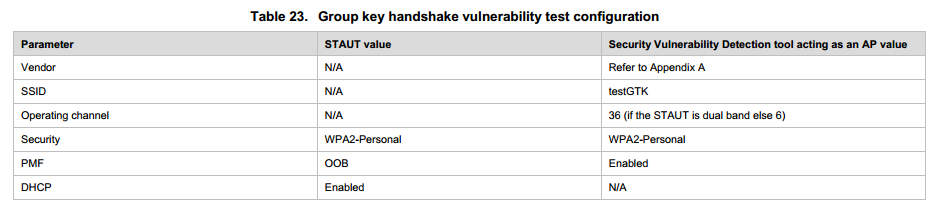
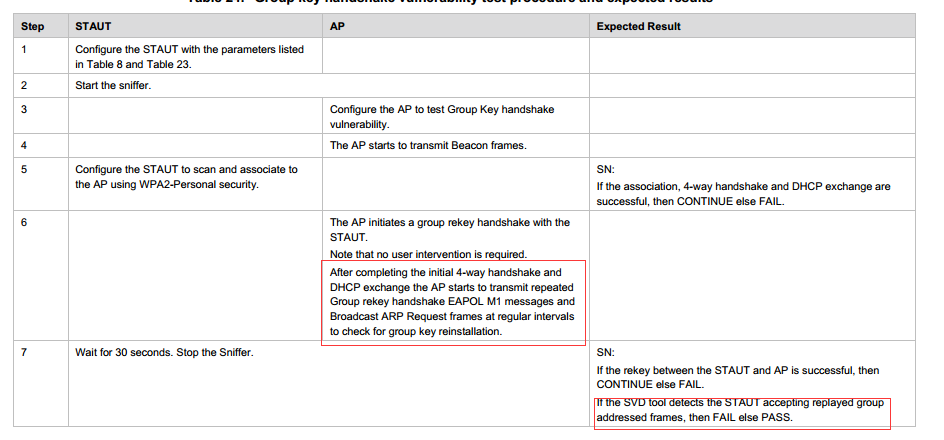
WTS SVD-5.2.3 and SVD 5.3.1 test scenario description:
5.2.3:the SVD shouldn’t detected the STAUT accepting replayed group addressed frames while AP transmited Broadcast ARP Request frames.
Test procedures:
5.3.1:
Test procedures:
Both of them fail at STAUT accepting replayed group addressed frames, the attached contains driver console and sniffer log i think they are useful for you and if you need more information please let me know.