I have a case with a customer which has exchanged a MR33 for a MR45 (both Merakis) and all devices are working when connecting to a MR33 but can't connect to MR45. This is only valid for WPA2 PSK and WPA2 EAP encryption. If the AP is setup without encryption then the device can connect. The CC3100 FW version during the tests was v2.10.0.0
Customers reply:
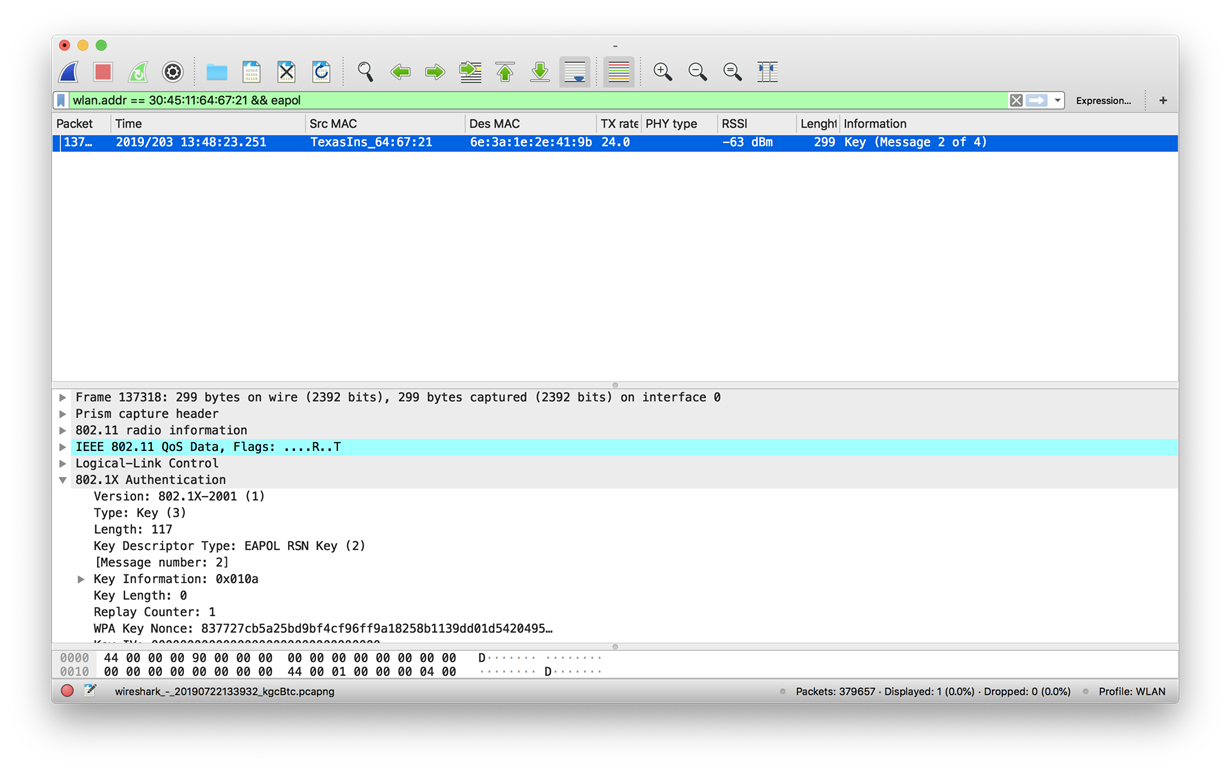
{{ It appears the device (CC3100) is failing during the 4 way handshake, whereby the AP is sending handshake 3, but an acknowledgement isn't being sent back:
received EAPOLKey frame sending 3/4 message of 4-Way Handshake Warning! EAPOLKey timeout sending 3/4 message of 4-Way Handshake Warning! EAPOLKey timeout sending 3/4 message of 4-Way Handshake Warning! EAPOLKey timeout sending 3/4 message of 4-Way Handshake Warning! EAPOLKey timeout
On a packet capture I took (which is one way) we only see a EAPOL second handshake, and not the fourth }}
All test were done with WPA 2 PSK.
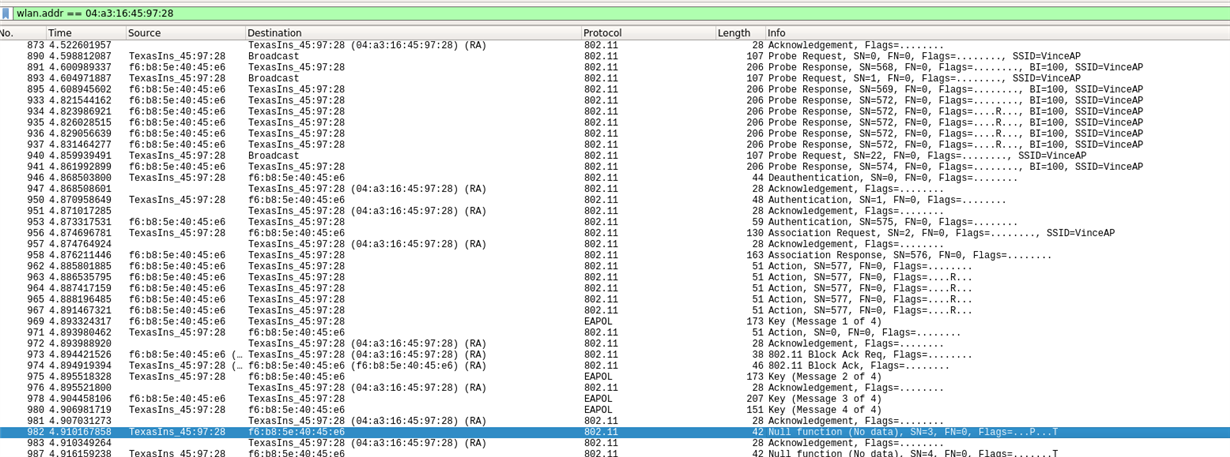
Attaching also a packet capture from my TeamViewer session and a screenshot that was taken from Meraki support.