Other Parts Discussed in Thread: UNIFLASH,
Tool/software: TI C/C++ Compiler
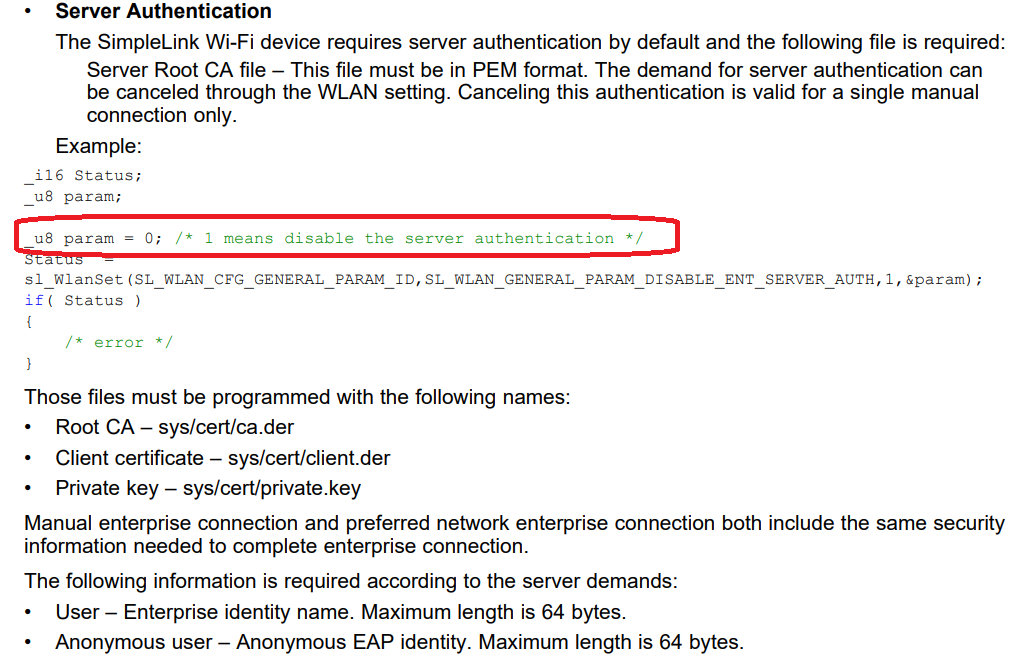
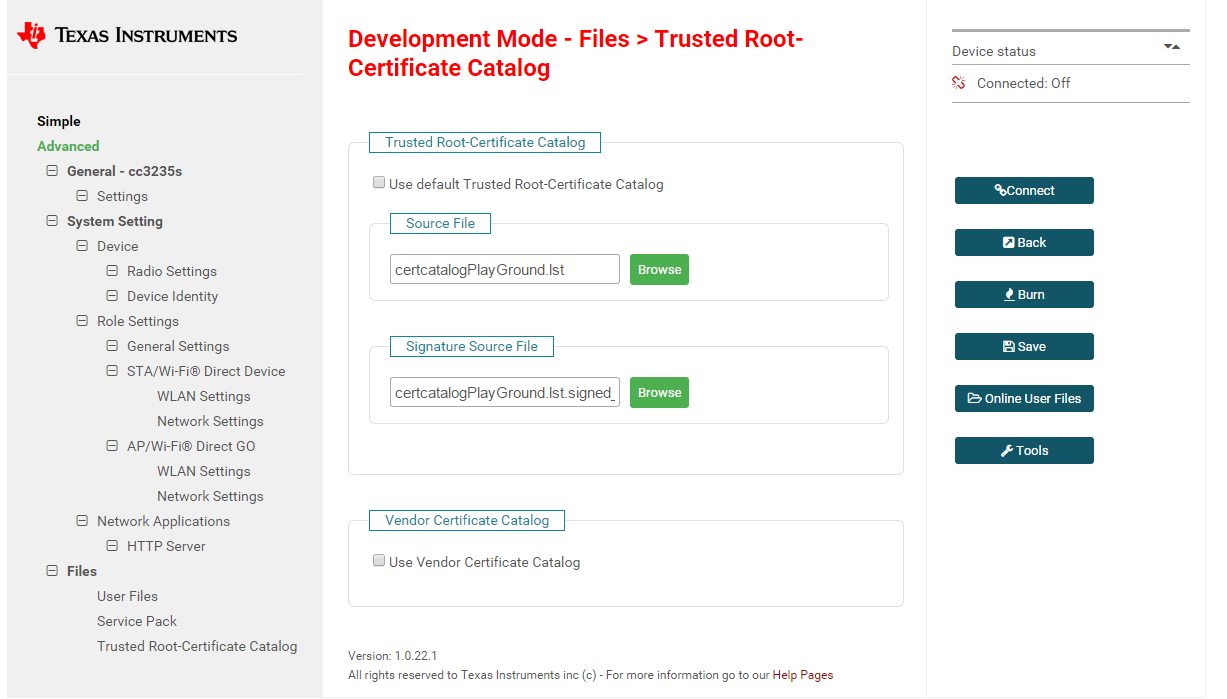
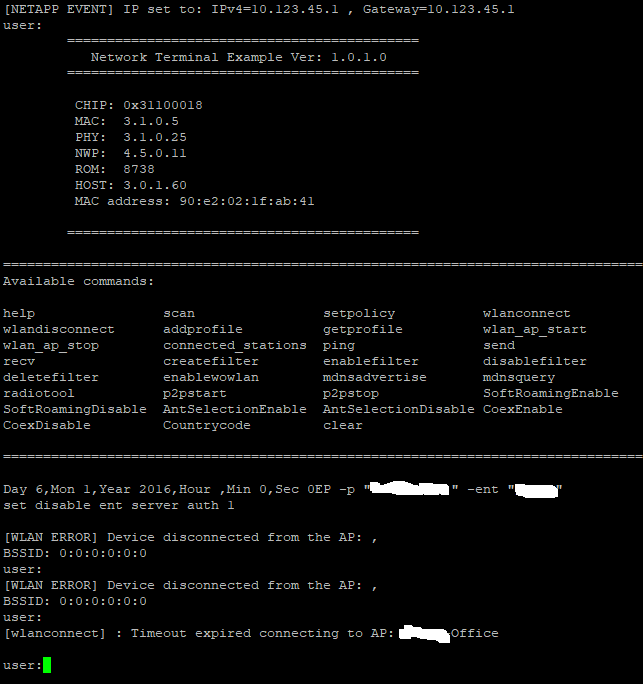
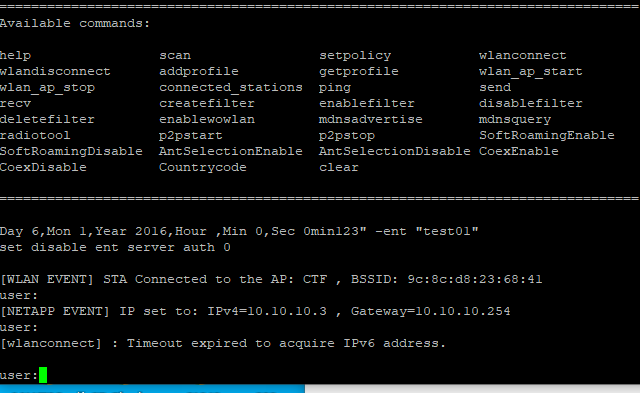
I input WiFi password in simple link web, and connect to WiFi after confirm. But it can't connect to the enterprise WiFi. As shown in the figure, it is the setting reference of enterprise WiFi. CA file is not needed. Set EAP-PEAP0 with MSCHAP under the enterprise menu of the web page, and enter the user name and password. WiFi cannot be connected. The SDK version is 3.40.00.05.
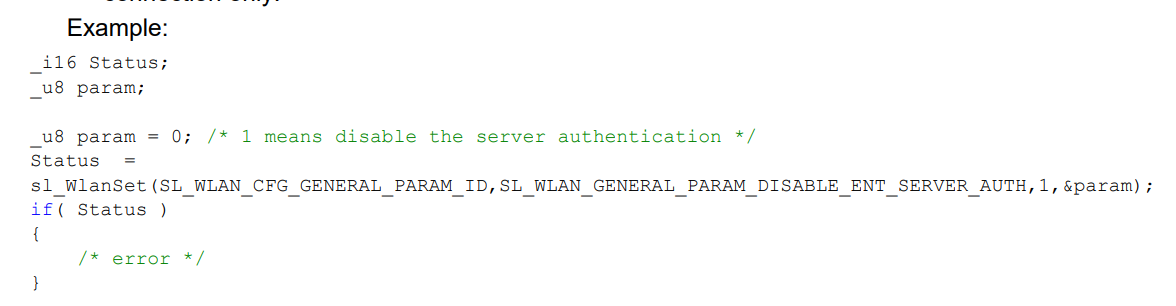
1. If the server does not need CA files, need to set param to 1?
2. Need to add corresponding files in uniflash?