Hi Team WiFi,
I have the following customer issue/question..
“I was wondering if you could provide any insight into an issue with a CC3100.
They have an 802.1X network with PEAP0 MSCHAPv2 and seemingly at random, a client (us) will start rejecting their loaded root CA cert and drop from the network.
If they power cycle our side, it’ll connect back up happily.
According to their IT they’ve seen where we initially trust the cert, connect and authenticate, but after a while it starts rejecting it and only a power cycle can get it to recover. They’ve also seen where the client on and off trusts and rejects the cert without a power cycle.
Same symptoms across multiple boards.
From what I can tell, the CC3100 is not locking up, but also not sending a “disconnected” callback to the host processor.
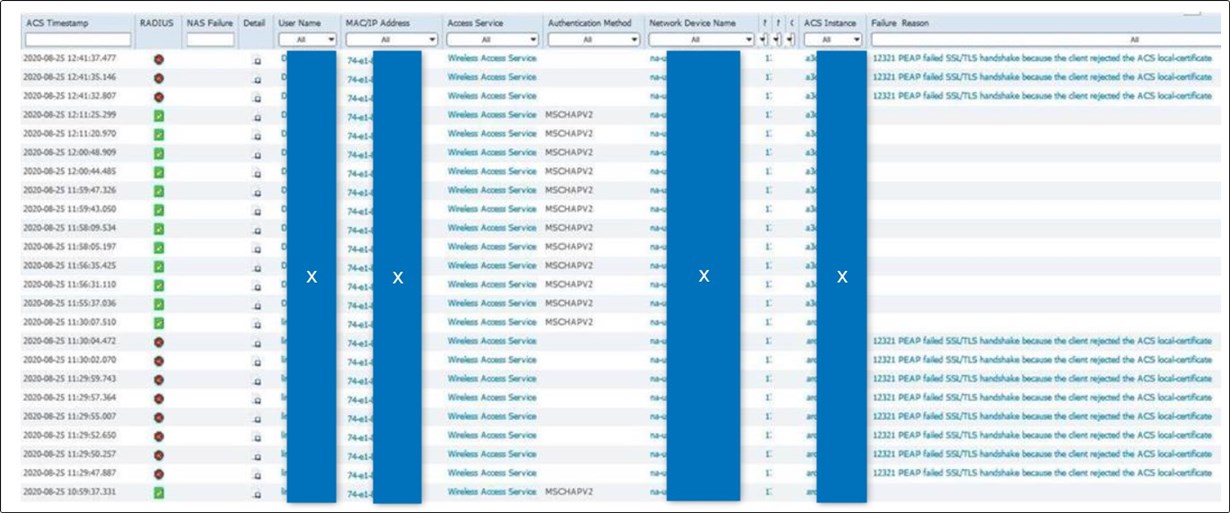
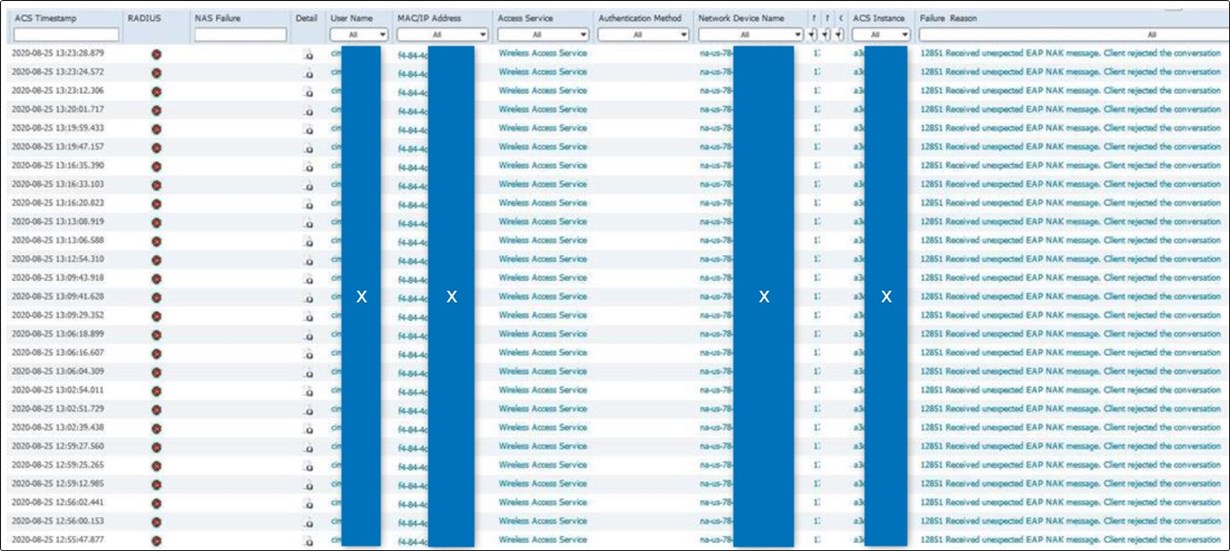
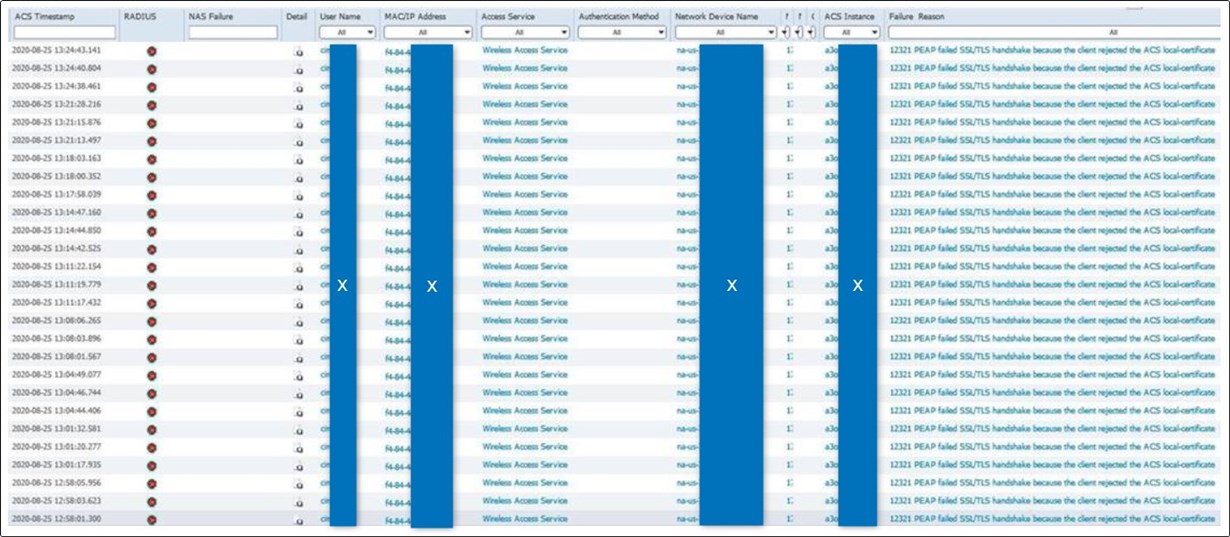
They sent the screenshots below of the AP side errors they’re getting and, after some googling, does seem to be a client side error. They have other plants up and running without this issue, so I’m not ruling out a network config issue, but I was wondering if you’ve heard of anything similar happening elsewhere or have any insight into what might be happening?
74-e1-82-3a-c4-9e : starts rejecting cert
F4-84-4c-3d-99-37 : client rejecting connection
F4-84-4c-65-26-00 : client rejecting cert”
Thanks, Merril