Other Parts Discussed in Thread: UNIFLASH, CC3200
Hi All,
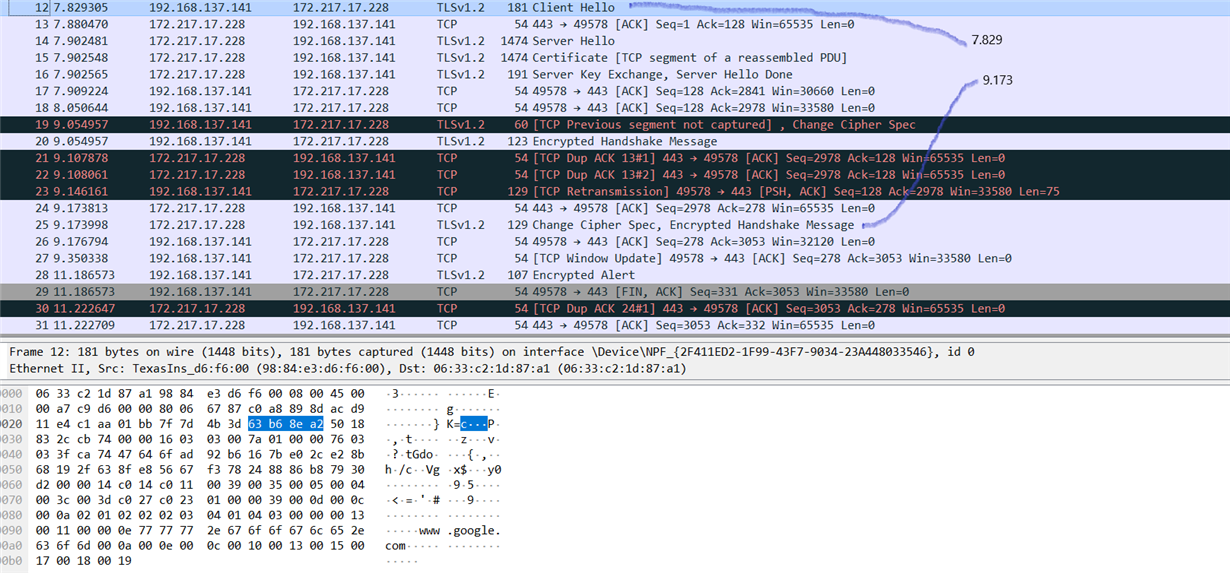
I am having CC3100 (SDK 1.3.0) connected over SPI to the host MCU (Arm M4). When I try to connect to any server over secure socket, it takes between 1 - 2 seconds. Release notes for the SDK 1.3.0 says that minimum tls/ssl connection time is 130 ms (for RSA) and 1.3s (for ECC). However, no matter what cipher is used, I am getting max 2 seconds for establishing tls connections (I have tested it on pure sockets and with httpcli library). Question: is this 1 - 2 seconds expected time for tls/ssl connection establishment or... can you point to some parameter, flag... that can be used for reducing this time?
Thanks,
Aleks