Hi,
I am trying to Encrypt and Decrypt the large (~250 KB) binary MCU Image which is loaded to the File system.
Example scenario is like Normal Binary ----> Encrypt binary -----> Decrypt Binary (Finally Decrypted binary shall be equal to Normal binary).
Due to memory constraints, I'm trying Encryption and Decryption over chunk by chunk data of the file (256 bytes per chunk).
Encryption Scenario 1: Read 256 KB Normal Binary data Encrypt and store to FS. (Repeat until the Complete Normal binary gets Encrypted).
Decryption Scenario 2: Read 256 KB Encrypted data Decrypt and store to FS.(Repeat until the Complete Encrypted binary gets Decrypted).
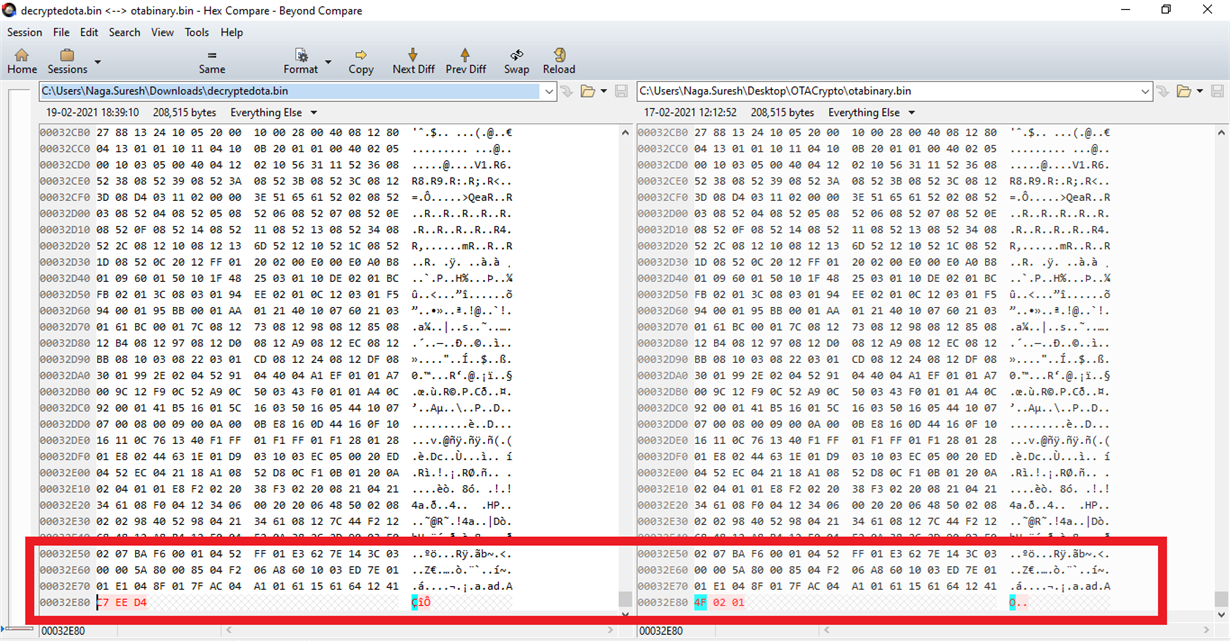
The Issues is Final Decrypted binaries' last chunk is not equal to the Normal binaries'. Last Chunk of binary data is getting corrupted.
Please check the below comparison between Actual binary data and Decrypted binary data.
Is there any standard way I can handle the last chunk of data for AES Encryption/Decryption.
Normal binary file size is 2,08,515 bytes.
Please find the AES configuration:
#define PVT_KEY "abcdefghijklmn12" CryptoCC32XX_Handle crypto_handle; CryptoCC32XX_EncryptMethod method = CryptoCC32XX_AES_ECB; // Not required IV CryptoCC32XX_EncryptParams params; params.aes.keySize = CryptoCC32XX_AES_KEY_SIZE_128BIT; params.aes.pKey = (const uint8_t *)PVT_KEY; // desiredKey length should be as the desiredKeySize //params.aes.pIV = (void *)pointerToInitVector;
Note: I also tried online AES Encryption / Decryption (http://aes.online-domain-tools.com/) with the same binary, still observed the same issue.
Please help me out resolving the issue.