Other Parts Discussed in Thread: CC3120, TEST2
Hi,
I have questions about PSK in WPA/WPA2.
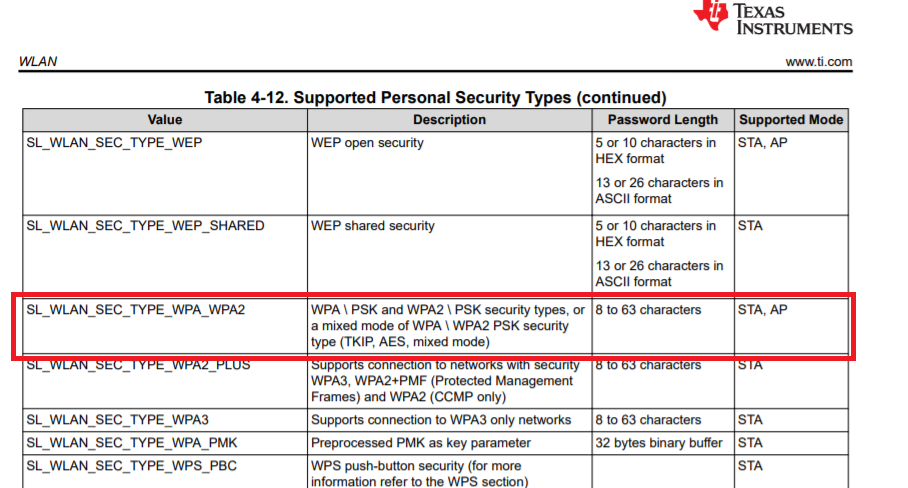
Q1: The user guide described "8 to 63 characters".
Is it possible to set 64 characters in HEX format?
Q2: When I connect the module to the AP as STA mode, I use "Profiles" to configure it. (Configured using the API "sl_WlanProfileAdd")
In order to set a 64-character HEX values (256 bits), should I set the HEX values as 64-characters of ASCII in the "SlWlanSecParams_t" key and set the KeyLen to 64?
Q3: Is there a rule for setting Uppercase/Lowercase for A to F?
In the evaluation of the actual device, it seems that 64-character HEX values can be sent as ASCII, and lower-case characters are not a problem. For example, 0x1234 can be sent as a string of "1234".
However, it differs from the specification in the user guide mentioned above. So, I need TI's opinion on this.
Best Regards,
UNA