Part Number: CC1352P7
Other Parts Discussed in Thread: CC2652R7, UNIFLASH, SYSCONFIG
HI TI!!!
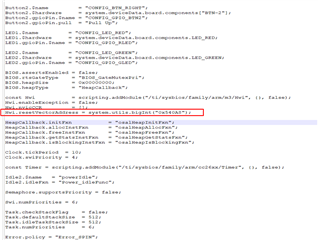
I am testing the OTA in zr_sw_ota_client_onchip_LP_CC1352P7_4 and zr_sw_ota_client_offchip_LP_CC1352P7_4.
I am using LPCC1352P7_4 SDK:6_41_00_17
zr_sw_ota_client_offchip_LP_CC1352P7_4 works perfectly!!! The firmware is downloaded and run the new firmware.
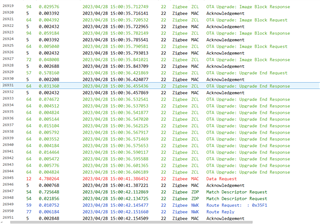
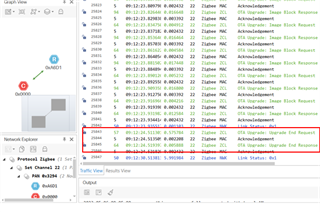
but I have a problem with zr_sw_ota_client_onchip_LP_CC1352P7_4, the firmware is downloaded, but the new firmware are no running, the active firmware on CC1352P7 is the old firmware.
Do you have any idea what I might be doing wrong?
Thank yuo very much!