Other Parts Discussed in Thread: Z-STACK,
Hi all,
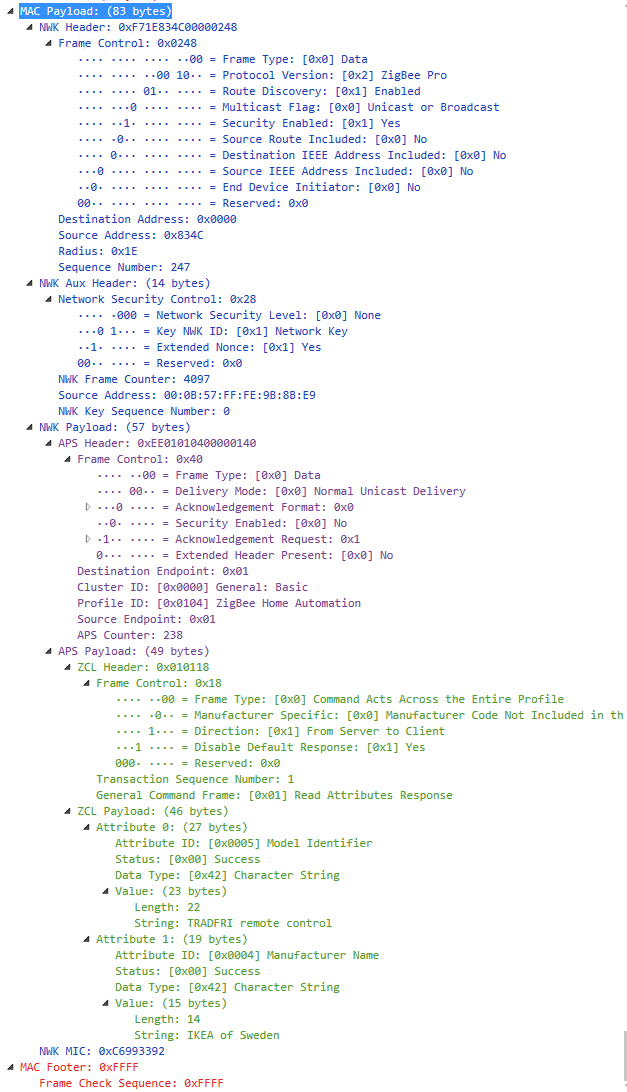
We currently have an issue with out CC2530 running Z-Stack 2.6.3. In some cases we receive a MT CMD from the chip which is not present in the Z-Stack Monitor and Test API. This is the full raw hex buffer:
"fe456564656e0ecf1dcf0101005c0082ce050000311801010500004216545241444652492072656d6f746520636f6e74726f6c040000420e494b4541206f66205377ffffffff0000006f"
SOF: 0xFE
LENGTH: 0x45
CMD0: 0x65 (so a SRSP ZDO)
CMD1: 0x64 (this one seems not to exist in the Z-Stack Monitor and Test API)
The FCS matches.
In this case I would actually expect:
SOF: 0xFE
LENGTH: 0x45
CMD0: 0x44 (so a AREQ AF)
CMD1: 0x81 (AF_INCOMING_MESSAGE)
Anybody an idea what is going on? What is the SRSP command we receive from the chip instead of the expected AF_INCOMING_MESSAGE?
Thanks!