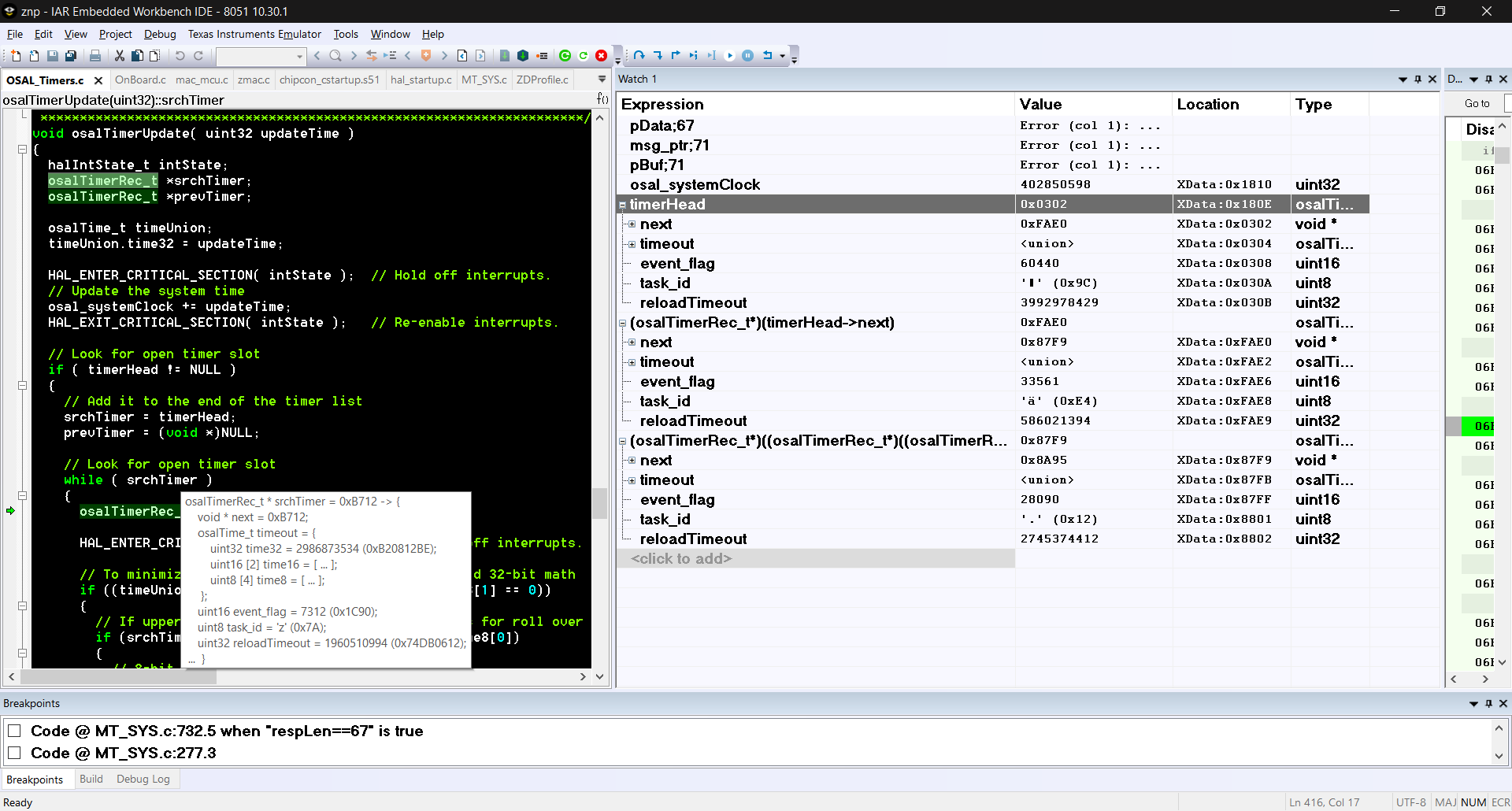
The serial interface of the ZNP was not responding, and as IAR was open in a debug sessin, I have more information.
My interpretation of the timerHead LinkedList is that it is corrupted. A clean linked list has only one bit in the event_flags .
The screenshot should help understand that. I also saved memory from using Debug > Memory > Save . I do not know what is required exactly to be able to reload it.
I join the logs. The last communications of the ZNP are shown here:
[2020-11-22 17:11:58.996636] > [AF/AREQ] **DATA_CONFIRM** ZSuccess EP:01 Seq:6 (SYS:4/TYPE:40/CMD:80) ( 8)::fe 03 44 80 00 01 06 c0 [2020-11-22 17:11:58.987306] 19618 0x0000 → 0xfec7 ZigBee HA 51 ZCL: Discover Attributes, Seq: 6 [2020-11-22 17:11:58.993800] 19621 → IEEE 802.15.4 5 Ack **** Not sure that this was a valid communication from the ZNP, but just in case: [2020-11-22 17:12:04.972770] 19638 → 0xec5c IEEE 802.15.4 52 Reserved, Dst: 0xec5c, Bad FCS
For the future, I am casting the type for "next" so that I do not need to cast it in the debugger.
typedef struct osalTimerRec_s
{
struct osalTimerRec_s *next;
osalTime_t timeout;
uint16 event_flag;
uint8 task_id;
uint32 reloadTimeout;
} osalTimerRec_t;
This is a normal linked list:
I was able to save a bit of RAM as well by changing the storage class of a big variable in MT.c:
Before: 239 887 bytes of CODE memory 32 bytes of DATA memory (+ 70 absolute ) 7 935 bytes of XDATA memory 192 bytes of IDATA memory 8 bits of BIT memory 426 bytes of CONST memory
After:
239 887 bytes of CODE memory 32 bytes of DATA memory (+ 70 absolute ) 7 891 bytes of XDATA memory 192 bytes of IDATA memory 8 bits of BIT memory 470 bytes of CONST memory
Here is the seriallog and gateway log and sniffer log. Hopefully that heps to identify what caused this I can send a download link to the project (with logs, etc) - as it contains the source, I can do it by private mesage.