Part Number: MSP432E401Y
Other Parts Discussed in Thread: UNIFLASH
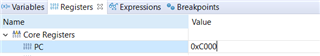
We are using the example UART Bootloader code to jump to the Application which is flashed at 0xC000. We are able to jump to the application at 0xC000, however the concern is that we are unable to debug/walkthrough the BL code at all. Need support regarding the same.
The code is compiled and loaded using CCS and the code doesn't start from ResetISR. Hence, unable to perform a debug operation using breakpoints and traversing through the code. Below is the screenshot of the code after loading the BL code. The .ccxml file selected as "XDS110 Debug Probe", Device "MSP432E401Y"
Note: With the same configuration, code traversing works totally fine in the Application code.
However, when target config file .ccxml uses “XDS 110 USB debugger” & Device set as “TIVA TM4C129XNCPDT”. -> This configuration allows the program execution to enter reset ISR. However it goes to a free run after executing ProcessorInit (i.e can't step over right after ProcessorInit executes)
Details of the setup/project
Controller : MSP432E401Y (custom board)
CCS Version : 10.4.0.00006
Debugger : XDS110
Uniflash : To flash the application.hex file
Note : Also tried in the launchpad, same issue as stated above, not at all able to walk-through the code.
Thanks,
Nikita