Part Number: MSP-EXP432E401Y
Other Parts Discussed in Thread: MSP432E401Y, TM4C129ENCPDT
Hi,
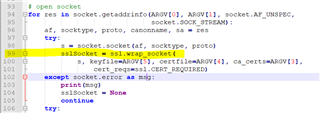
I am using the MSP432E401Y launchpad and I'm implementing a TLS Client socket to connect to a TLS Server.
When I developed this application using the TM4C129ENCPDT, I used something in wolfssl which is the WOLFSSL_VERIFY_NONE to bypass server cert verification. My team came up with our own method to authenticate the server.
I'd like to implement something similar on the MSP432. I understand the MSP432 is using the slnetsock, which, to my understanding, uses mbedTLS under the hood? Is that right? I am having difficulties figuring out the equivalent of WOLFSSL_VERIFY_NONE in the case of the MSP432E401Y.
How do I implement this? Any input is very much appreciated.
Thanks
AJ