Part Number: TM4C1294NCPDT
FreeRTOS Version: v9.0
Tivaware version: TivaWare_C_Series-2.2.0.295
CCS version: 12.1.0.00007
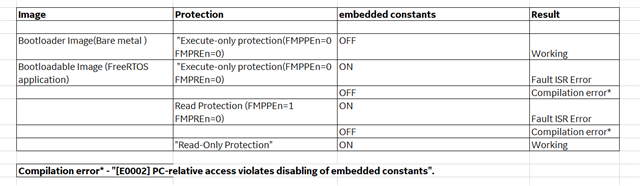
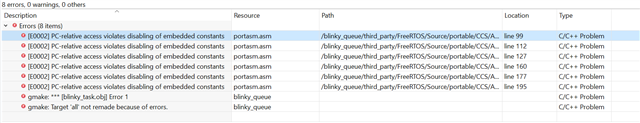
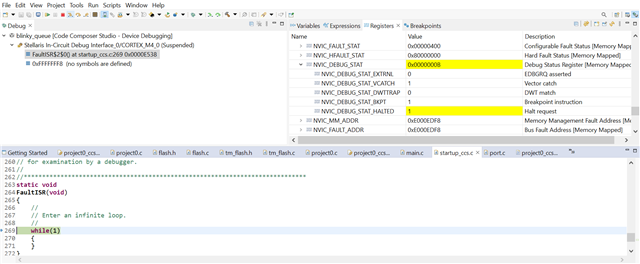
Issue: Compilation error "[E0002] PC-relative access violates disabling of embedded constants".
@ file portasm.asm and
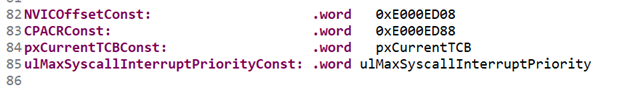
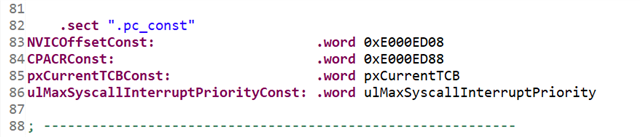
@ line 99: ldr r0, ulMaxSyscallInterruptPriorityConst
@ line 112: ldr r3, pxCurrentTCBConst
@ line 127: ldr r0, ulMaxSyscallInterruptPriorityConst
@ line 160: ldr r3, pxCurrentTCBConst
@ line 177: ldr r0, NVICOffsetConst
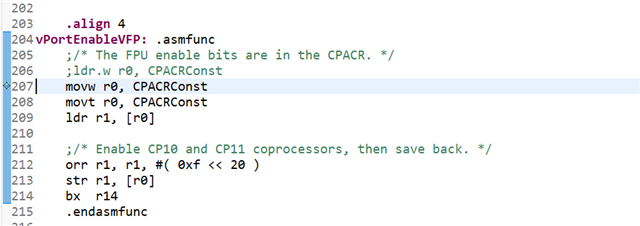
@ line 195: ldr.w r0, CPACRConst
Background:
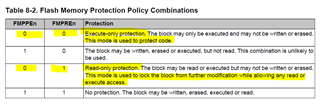
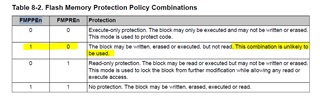
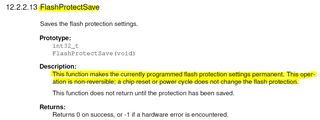
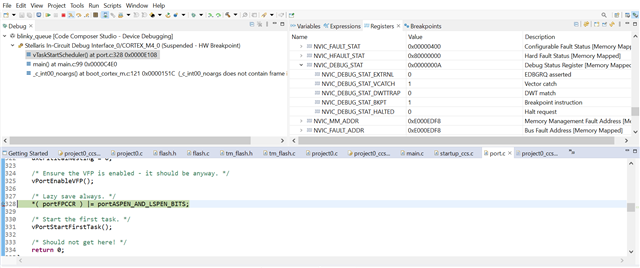
We enabled "execute-only" flash protection for the simple freeRTOS project. But we are getting compilation error as mentioned above.
Infact Memory protection without FreeRTOS is working fine.
As pe the forum suggestion we did following changes:
1. chosen "OFF" for --embedded_constants
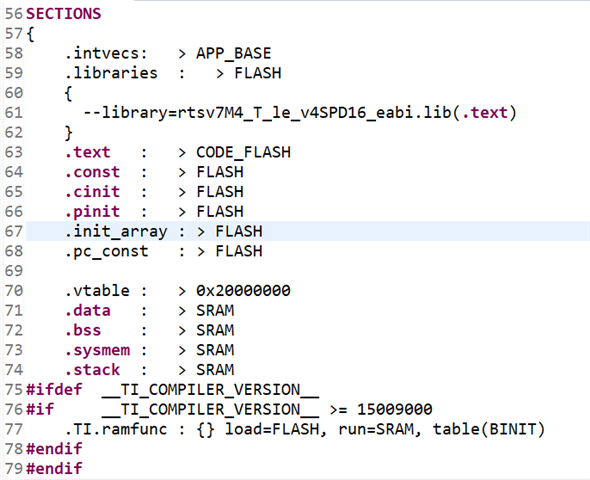
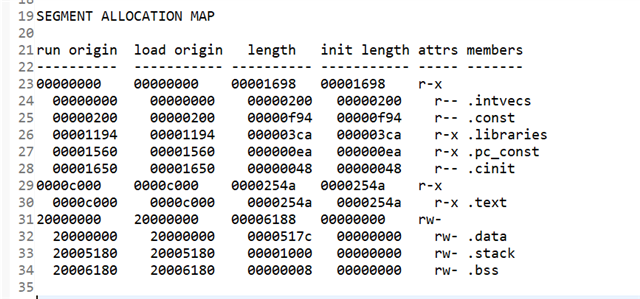
2. Done memory section changes as below.
SECTIONS
{
.intvecs: > 0x00000000
.libraries : > FLASH
{
--library=rtsv7M4_T_le_v4SPD16_eabi.lib(.text)
}
.text : > CODE_FLASH
.const : > FLASH
.cinit : > FLASH
.pinit : > FLASH
.init_array : > FLASH
.vtable : > 0x20000000
.data : > SRAM
.bss : > SRAM
.sysmem : > SRAM
.stack : > SRAM
}
With Regards
Velliyangiri Palanisamy