Other Parts Discussed in Thread: SYSCONFIG
Hi,
Do the TI drivers such as C:\ti\simplelink_msp432e4_sdk_4_20_00_12\source\ti\drivers\aesecb use hardware acceleration? I don't see the module initialization as in driverlib.
Regards,
-Mike
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
Hi,
Do the TI drivers such as C:\ti\simplelink_msp432e4_sdk_4_20_00_12\source\ti\drivers\aesecb use hardware acceleration? I don't see the module initialization as in driverlib.
Regards,
-Mike
Hi Mike,
I will investigate and get back. I tend to think it uses the AES modules as stated in sysconfig description. After AESECB is added, the generated file ti_drivers_config.c and ti_drivers_config.h files are updated.
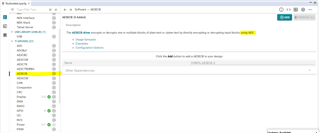
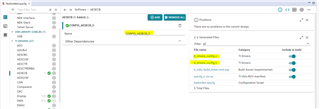
In the meantime, here is the user's guide for AESECB. https://software-dl.ti.com/simplelink/esd/simplelink_msp432e4_sdk/3.40.00.08/docs/tidrivers/doxygen/html/_a_e_s_e_c_b_8h.html#a4f4274c6aa928e8e10d3e516e73f77ea
Hi Mike,
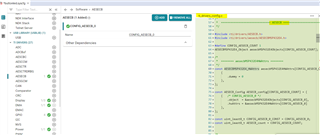
Sorry for the late response. Doing some searching on the SDK, I can find that in several driver files where the AES module is being initialized. Below is a snippet of code for C:\ti\simplelink_msp432e4_sdk_4_20_00_12\source\ti\drivers\aescbc\AESCBCMSP432E4.c where you can find AES module is being reset, initialized and configured.
AESReset(AES_BASE);
AESConfigSet(AES_BASE, AES_CFG_MODE_CBC |
AES_CTRL_SAVE_CONTEXT |
keySizeConfig |
(operationType == AESCBC_OPERATION_TYPE_ENCRYPT ? AES_CFG_DIR_ENCRYPT : AES_CFG_DIR_DECRYPT));
AESIVSet(AES_BASE, (uint32_t*)&operation->iv[0]);
AESKey1Set(AES_BASE, (uint32_t*)key->keyMaterial, keySizeConfig);
AESLengthSet(AES_BASE, operation->inputLength);
if (object->returnBehavior == AESCBC_RETURN_BEHAVIOR_POLLING)
{
object->returnStatus = AESCBC_doPollingMode(operation);
AESIVRead(AES_BASE, (uint32_t *)object->iv);
if (object->threadSafe == true) {
CryptoResourceMSP432E4_AES_SHA2_releaseLock();
}
}
else if (object->returnBehavior == AESCBC_RETURN_BEHAVIOR_CALLBACK)
{
object->returnStatus = AESCBC_STATUS_SUCCESS;
CryptoResourceMSP432E4_setHwiCallback(AESCBC_hwiFxn, handle, hwAttrs->intPriority);
dma = UDMAMSP432E4_open();
DebugP_assert(dma != NULL);
/* Kick the DMA state machine. */
AESCBC_nextState = AESCBC_doSetupState;
HwiP_post(INT_AES0);
}
else if (object->returnBehavior == AESCBC_RETURN_BEHAVIOR_BLOCKING)
{
object->returnStatus = AESCBC_STATUS_SUCCESS;
CryptoResourceMSP432E4_setHwiCallback(AESCBC_hwiFxn, handle, hwAttrs->intPriority);
dma = UDMAMSP432E4_open();
DebugP_assert(dma != NULL);
/* Kick the DMA state machine. */
AESCBC_nextState = AESCBC_doSetupState;
HwiP_post(INT_AES0);
/* Wait for the DMA state machine to complete. */
SemaphoreP_pend(CryptoResourceMSP432E4_AES_SHA2_operationSemaphore, (uint32_t)SemaphoreP_WAIT_FOREVER);
}
return object->returnStatus;
}