Other Parts Discussed in Thread: UNIFLASH
We recently re-spun a custom board with the AM2431A microcontroller to now use the AM2431B microcontroller. On the previous board, we successfully converted the sbl_sd example into an eMMC SBL that read and booted a multicore appimage file that was flashed to the eMMC boot partition.
When the new board arrived with AM2431B microcontroller, we updated the SDK to version 09_00_00_30 since we had to support HS_FS operation. We have gone through the migration guides multiple times and were finally able to get the SBL and Application properly built and signed, We have now run into an issue where the SBL appears to validate and load the the multicore image, however, it never seems to get past the Bootloader_runSelfCpu() function once it is ready to start the application.
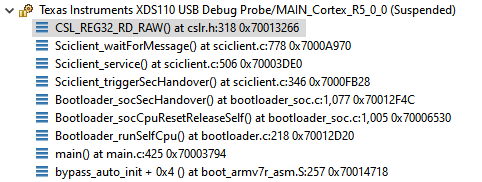
When debugging the SBL in CCS, I paused and looked at the call stack once the SBL appeared to be hung. Here's what it showed:
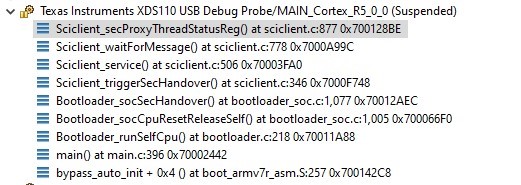
It appears that the Security handover never completes successfully, as a response is never received when the TISCI_MSG_SEC_HANDOVER message is sent.
I have looked through various TI documents (SDK User Guide, TISCI User guide, etc.) and read the Security Board Configuration section of the TISCI User Guide: https://software-dl.ti.com/tisci/esd/latest/3_boardcfg/BOARDCFG_SEC.html
It's unclear what, if anything, I need to add to the SBL to enable the security capabilities of the SYSFW. I have looked through the examples in the SDK and have not found anything related to configuring board security.
Is there documentation somewhere that explains the process from beginning to end on how to setup security or could something else be causing this issue?