Other Parts Discussed in Thread: UNIFLASH
Tool/software:
Hello.
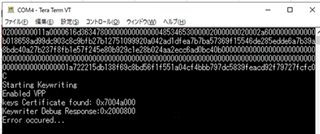
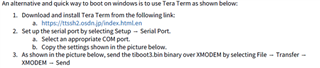
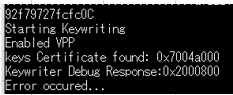
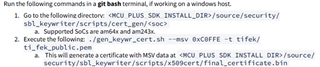
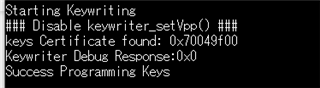
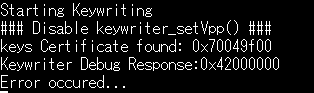
I created tiboot3.bin following the instructions in "AM64X_AM243X OTP Keywriter User Guide".
I have two questions.
Q1: When I run the UART Uniflash command, is the device converted to HS-SE?
python3 ... /... /... /... /... /tools/boot/uart_uniflash.py -p /dev/ttyUSB0 --cfg=<soc>/keywr_sbl_<soc>.cfg
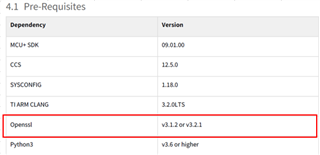
Q2: Which document is "Section 4.2" written here? Which document should I refer to?
Section 4.2" does not exist in "AM64X_AM243X OTP Keywriter User Guide".