Other Parts Discussed in Thread: SYSCONFIG
Tool/software:
Hi TI-Team,
I have the exact same problem as described in the linked issue (https://e2e.ti.com/support/microcontrollers/arm-based-microcontrollers-group/arm-based-microcontrollers/f/arm-based-microcontrollers-forum/1349306/mcu-plus-sdk-am243x-cannot-sbl_ospi-boot-the-hs_fs-application-image-on-my-custom-board-am2431alv/5148133?tisearch=e2e-sitesearch&keymatch=%25252520user%2525253A572738#5148133)
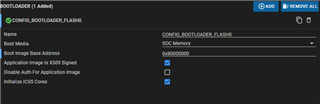
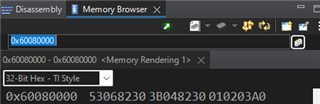
I use SBL_OSPI, which is adjusted to my custom board (custom flash, custom DDR etc.) this works fine if the option "Disable Auth For Application Image" is unchecked. I can then load firmware files successfully. As soon as this Authentication option is checked the SBL_OSPI cannot start the flashed .appimage.hs_fs at 0x80000. If I debug I see that it fails at the same position as mentioned in the linked thread. The content of 0x60080000 is also equal
Yes, I also integrated the suggested workaround shown in various other threads, the following code fraction is inserted just before the Bootloader_parseMultiCoreAppImage(...).
/* WORKAROUND: Enable the DAC mode */
OSPI_Handle ospi_handle = OSPI_getHandle(CONFIG_OSPI0);
OSPI_enableDacMode(ospi_handle);
I am currently using the MCU+ SDK delivered with the latest www.ti.com/.../09.02.00.08
I also tried to replicate on AM64x-EVM but there everything worked fine, I could start/authenticate any image given. Even my custom images using all R5-cores and now beeing bigger than 1,6 MB
Help would be highly appreciated. What is the problem? Is there a bigger bug in somewhere in MCU+ SDK and I currently need to disable authentication at all?
Kind regards,
Dominik