Part Number: MSPM0G3107-Q1
Other Parts Discussed in Thread: MSPM0G3107, SYSCONFIG
Tool/software:
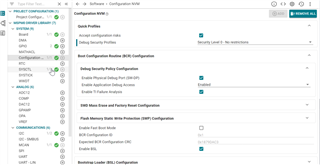
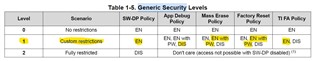
I'd like to configure generic security levels on MSPM0G3107 uC to Protection Level 1 with following customisation as highlighted:
This will be applied by hex modification from external tool.
In the SW I must verify that proper security settings are applied.
Therefore there are few points and questions:
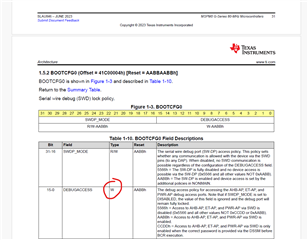
- To check SW-DP policy I will read BOOTCFG0 register field SWDP_MODE and expect AABBh, correct?
- To check App Debug Policy I would read BOOTCFG0 register field DEBUGACCESS but I cannot read this as in technical reference manual (SLAU846 rev.June2023) this bit is write only. How do I verify if correct app Debug Policy is set? Can I somehow read the setting? Or maybe its just a documentation issue and this register is indeed R/W?
- To check Mass Erase Policy I will read BOOTCFG3 register field MASSERASECMDACCESS and expect CCDDh, correct?
- To check Factory Reset Policy I will read BOOTCFG3 register field FACTORYRESETCMDACCESS and expect CCDDh, correct?
- To check TI FA Policy I will read BOOTCFG1 register field TI_FA_MODE and expect AABBh, correct?
- Do I need to verify other registers and settings to achieve Protection Level 1?
- BCRCONFIGID - CONFIG?
- BOOTCFG1 - BSL_PIN_INVOKE?
- BOOTCFG2 - BSLMODE, FASTBOOTMODE?
- FLASHSWP0 - MAINLOW?
- FLASHSWP1 - MAINHIGH?
- BOOTCFG4 - APPCRCMODE, NONMAINSWP?
Note ad.2: screenshot from SLAU846.pdf