Other Parts Discussed in Thread: MSPM0L1306,
Tool/software:
I am writing a host-side (Linux) I2C BSL flasher for the MSPM0L1306. I am able to enter BSL mode via the GPIO invoke sequence, connect, mass erase, and flash data to the device. However, standalone verification is not working as I would expect. I am using the same CRC algorithm that's used to calculate the checksum for the BSL messages to calculate the expected CRC on the data block I am trying to verify. However, the CRC returned from the Standalone Verification command does not match the CRC I am calculating. Below is the function I am using to send the Standalone Verification message to the BSL. bsl_crc32 is the function I have to generate the CRC32 locally.
bool bsl_verify_simple(uint32_t addr, uint32_t len_data) {
uint32_t crc32;
bsl_txbuf[0] = 0x80; //PACKET_HEADER
bsl_txbuf[1] = 9; //CMD_BYTE(1) + ADDRS_BYTES(4) + VERIFY_BYTES(4)
bsl_txbuf[2] = 0;
bsl_txbuf[3] = 0x26; //CMD_VERIFY
*(uint32_t *) &bsl_txbuf[4] = addr; //HDR_LEN_CMD_BYTES(4)
*(uint32_t *) &bsl_txbuf[8] = len_data; //HDR_LEN_CMD_BYTES(4) + ADDRS_BYTES(4)
crc32 = bsl_crc32(&bsl_txbuf[3], 9); //CMD_BYTE(1) + ADDRS_BYTES(4) + VERIFY_BYTES(4)
*(uint32_t *) &bsl_txbuf[12] = crc32; //HDR_LEN_CMD_BYTES(4) + ADDRS_BYTES(4) + VERIFY_BYTES(4)
uint8_t tx_len = 16; //HDR_LEN_CMD_BYTES(4) + ADDRS_BYTES(4) + VERIFY_BYTES(4) + CRC_BYTES(4)
if (!i2c_write(bsl_txbuf, tx_len)) return false;
uint8_t rx_len = 13; // ACK_BYTE(1) + HDR_LEN_CMD_BYTES(4) + VERIFY_BYTES(4) + CRC_BYTES(4)
if (!i2c_read(bsl_rxbuf, rx_len)) return false;
// Check for ack
if (bsl_rxbuf[0] != BSL_ACK_OK) return false;
return true;
}
int main() {
<setup, invoke, connect, etc>
// verifying blank flash to test CRC
if (!bsl_verify(0, 1024)) goto err;
const uint8_t test_data_empty[1024] = {0x00};
bsl_crc32(test_data_empty, ARRAY_LEN(test_data_empty));
}
The BSL is accepting and handling the message (returning both an ACK as well as the correct response to indicate it is a Standalone Verification response) but the result does not match. I also tried comparing to an array of length 1024 of 0xFF and the CRC still does not match. Below is the raw buffer being built from above and sent to the device along with the response.
bsl_verify (sent):
0x80 0x09 0x00 0x26 0x00 0x00 0x00 0x00 0x00 0x04 0x00 0x00 0xa4 0xb8 0x14 0xef
bsl_verify(recv):
0x00 0x08 0x05 0x00 0x32 0x0b 0x00 0xc5 0x47 0x3d 0x93 0x08 0x6b
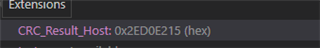
crc_recv: 0x47c5000b
crc_calc: 0x104a50d1
Is the CRC algorithm used for the Standalone Verification different than the one used for the message checksum verification? The datasheet makes no mention of it, and looking at the secondary BSL examples (which state the example implementation should match the ROM BSL) the CRC parameters are the same as the datasheet.
Related, the MSPM0 Bootloader User's Guide (slau887) has several errors in section 4.3.10 Standalone Verification. The command structure shown is the response packet, not the command packet. The example command (Host) specifies address 0x20000000 and length 0x400. The example response (BSL) is not a Standalone Verification response (0x32) but rather a Core Message Response (0x3B), with message content 0x05 (Invalid memory range):
H | LEN |CMD| A A A A | D D D D | CRC |
80 09 00 26 00 00 00 20 00 04 00 00 A0 97 D5 2E
response
BSL: 00 08 02 00 3B 05 B7 F6 FE F2 (MSG: invalid address!)