Tool/software:
Hi,
customer has found that the symmetric key for decrypting the data from the ROM bootloader is not provided to the HSM Runtime.
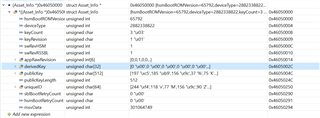
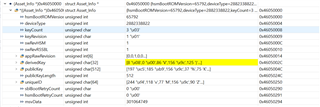
In the generated function KEYRING_Init() in the file TIFs_modules_config.c, the key from the gAssetInfo.derivedKey is copied to the gKeyringSymKey array.
However, the information gAssetInfo.derivedKey is 0. GAssetInfo is described by the ROM loader according to the information from the linker file.
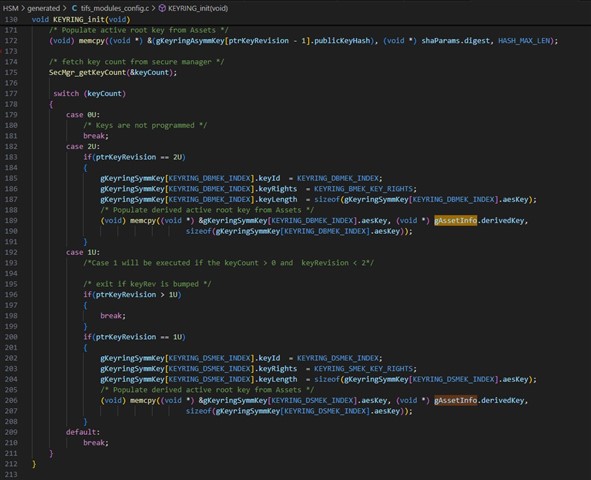
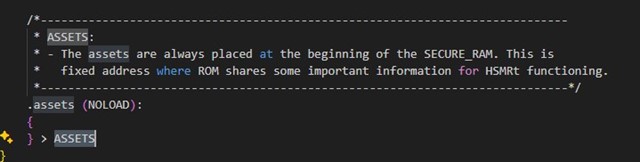
How do they get to the symmetric key? Do they need to access the OTP data directly?
Regards, Holger