Part Number: AM2612
Other Parts Discussed in Thread: AM2632, , AM2732
Tool/software:
Hi all:
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
Part Number: AM2612
Other Parts Discussed in Thread: AM2632, , AM2732
Tool/software:
Hi all:
Hi,
The current plan for this implementation of GCM algorithm is planned for SDK 11.0 (planned in the month of August)
The upcoming TIFS SDK 10.2 is already scheduled to be released next week and support for the GCM algorithm is not in the scope for this SDK.
I see that you have asked this for both AM261x and AM263x. May I know which project is this ask for?
Thanks and Regards,
Nikhil Dasan
Hi Nikhil,
There are two projects using AM2612 and AM2632 chips respectively. So, I need both GCM demo of AM261x and AM263x, and AM261x is more urgent.
Hi,
Let me discuss this internally and get back to you early next week
Regards,
Nikhil Dasan
Hi,
As mentioned earlier, the SDK 10.2 release and TIFS 10.2 release is already scheduled to be released by end of this week.
Post that I could provide you the GCM implementation on top of this release as patch by the end of next week.
Hope this works for you.
Thanks and Regards,
Nikhil Dasan
Hi Nikhil,
It's ok, thank you. Also could you please help to another Issue, we encounter trouble in HSM bootup step.
Hi,
The TIFS SDK 10.2 is live for AM261 and AM263 in the below links
AM263x
https://www.ti.com/secureresources/AM263X-RESTRICTED-SECURITY
AM261x
https://www.ti.com/secureresources/AM261X-TIFS-SDK
As mentioned earlier, the GCM implemention and driver that is tested on the above SDK is available below
AM263x
AM261x
To apply and build the above patch into SDK, please follow the below steps
Step 1: Download the TIFS SDK from above link for AM261/AM263
Step 2: Download the above patch for AM261/AM263
Step 3: Do the below to create a git repository on TIFS SDK for AM261/AM263
cd C:\ti\tifs_am26xx_10_02_00_01 git init git add . git commit -asm "master"
Step 4: Apply the patch using the below command
cd C:\ti\tifs_am26xx_10_02_00_01>
git apply ${PATH_TO_THE_PATCH}
Step 5: Build the AES-GCM example using the below command. This will load the HSM binary for AES-GCM application
cd C:\ti\tifs_am263x_10_02_00_01 gmake -s -C examples\dthe\aes\crypto_aes_gcm\am263x\hsm0-0_nortos\ti-arm-clang all
Step 6: Build the SBL to load this HSM binary. This will generate SBL binary dthe_log_sbl.release.hs.tiimage
cd C:\ti\tifs_am263x_10_02_00_01 gmake -s -C examples/sbl/dthe_log_sbl/am263x-cc/r5fss0-0_nortos/ti-arm-clang/ all DEVICE=am263x DEVICE_TYPE=HS
Step 7: Load this generated binary to AM26x board using preferred boot method and observe the below log
INFO Bootloader_socLoadHsmRtFw76 DevType HSSE INFO Bootloader_socLoadHsmRtFw78 HSMRT Size in Bytes 35651 INFO Bootloader_socLoadHsmRtFw98 hsm runtime firmware load complete ... [hsm0-0] 0.001599s Starting DTHE GCM Test Examples! [hsm0-0] 0.002022s [hsm0-0] 0.002216s [CRYPTO] Test 1 GCM with 128-bit key, mode 3 (hash computed) [hsm0-0] 0.002832s [CRYPTO] Initiated DTHE AES GCM Encryption with TAG generation [hsm0-0] 0.003881s [CRYPTO] DTHE AES GCM Encryption and Tag generation Success! [hsm0-0] 0.004487s [CRYPTO] Initiated DTHE AES GCM Decryption with TAG verification [hsm0-0] 0.005393s [CRYPTO] DTHE AES GCM Decryption and Authentication Success! [hsm0-0] 0.005995s [hsm0-0] 0.006200s [CRYPTO] Test 2 GCM with 192-bit key, mode 3 (hash computed) [hsm0-0] 0.006814s [CRYPTO] Initiated DTHE AES GCM Encryption with TAG generation [hsm0-0] 0.007867s [CRYPTO] DTHE AES GCM Encryption and Tag generation Success! [hsm0-0] 0.008473s [CRYPTO] Initiated DTHE AES GCM Decryption with TAG verification [hsm0-0] 0.009383s [CRYPTO] DTHE AES GCM Decryption and Authentication Success! [hsm0-0] 0.009985s [hsm0-0] 0.010190s [CRYPTO] Test 3 GCM with 256-bit key, mode 3 (hash computed) [hsm0-0] 0.010806s [CRYPTO] Initiated DTHE AES GCM Encryption with TAG generation [hsm0-0] 0.011860s [CRYPTO] DTHE AES GCM Encryption and Tag generation Success! [hsm0-0] 0.012467s [CRYPTO] Initiated DTHE AES GCM Decryption with TAG verification [hsm0-0] 0.013377s [CRYPTO] DTHE AES GCM Decryption and Authentication Success! [hsm0-0] 0.013980s [hsm0-0] 0.014186s [CRYPTO] Test 4 GCM with 128-bit key, mode 2 (hash pre-loaded) [hsm0-0] 0.014815s [CRYPTO] Initiated DTHE AES GCM Encryption with TAG generation [hsm0-0] 0.015867s [CRYPTO] DTHE AES GCM Encryption and Tag generation Success! [hsm0-0] 0.016475s [CRYPTO] Initiated DTHE AES GCM Decryption with TAG verification [hsm0-0] 0.017383s [CRYPTO] DTHE AES GCM Decryption and Authentication Success! [hsm0-0] 0.017986s [hsm0-0] 0.018192s [CRYPTO] Test 5 GCM with 192-bit key, mode 2 (hash pre-loaded) [hsm0-0] 0.018821s [CRYPTO] Initiated DTHE AES GCM Encryption with TAG generation [hsm0-0] 0.019876s [CRYPTO] DTHE AES GCM Encryption and Tag generation Success! [hsm0-0] 0.020483s [CRYPTO] Initiated DTHE AES GCM Decryption with TAG verification [hsm0-0] 0.021395s [CRYPTO] DTHE AES GCM Decryption and Authentication Success! [hsm0-0] 0.021998s [hsm0-0] 0.022204s [CRYPTO] Test 6 GCM with 256-bit key, mode 2 (hash pre-loaded) [hsm0-0] 0.022833s [CRYPTO] Initiated DTHE AES GCM Encryption with TAG generation [hsm0-0] 0.023888s [CRYPTO] DTHE AES GCM Encryption and Tag generation Success! [hsm0-0] 0.024496s [CRYPTO] Initiated DTHE AES GCM Decryption with TAG verification [hsm0-0] 0.025408s [CRYPTO] DTHE AES GCM Decryption and Authentication Success! [hsm0-0] 0.026019s All tests have passed!!
Thanks and Regards,
Nikhil Dasan
Hi,
Please find the updated patch here to support the IV for misaligned length (i.e. not 96 bits)
i.e. using the below to calculate Hash and Y0 and then using GCM mode 2 to pass the precalculated H and Y0

You can refer the below testcase as example
static void test_aes_gcm_nist_unaligned_iv(DTHE_Handle aesHandle)
{
DTHE_AES_Return_t status;
DTHE_AES_Params aesParams;
uint32_t aesResultEnc[APP_CRYPTO_AES_GCM_MAX_BUFF_SIZE/4U];
uint32_t aesGcmTagEnc[4U];
uint8_t zero_arr[] = { 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00 };
uint8_t key_unaligned_iv_tc[] = {
0xfe, 0xff, 0xe9, 0x92, 0x86, 0x65, 0x73, 0x1c,
0x6d, 0x6a, 0x8f, 0x94, 0x67, 0x30, 0x83, 0x08
};
uint8_t data_in_unaligned_iv_tc[] = {
0xd9, 0x31, 0x32, 0x25, 0xf8, 0x84, 0x06, 0xe5,
0xa5, 0x59, 0x09, 0xc5, 0xaf, 0xf5, 0x26, 0x9a,
0x86, 0xa7, 0xa9, 0x53, 0x15, 0x34, 0xf7, 0xda,
0x2e, 0x4c, 0x30, 0x3d, 0x8a, 0x31, 0x8a, 0x72,
0x1c, 0x3c, 0x0c, 0x95, 0x95, 0x68, 0x09, 0x53,
0x2f, 0xcf, 0x0e, 0x24, 0x49, 0xa6, 0xb5, 0x25,
0xb1, 0x6a, 0xed, 0xf5, 0xaa, 0x0d, 0xe6, 0x57,
0xba, 0x63, 0x7b, 0x39
};
uint8_t data_out_unaligned_iv_tc[] = {
0x61, 0x35, 0x3b, 0x4c, 0x28, 0x06, 0x93, 0x4a,
0x77, 0x7f, 0xf5, 0x1f, 0xa2, 0x2a, 0x47, 0x55,
0x69, 0x9b, 0x2a, 0x71, 0x4f, 0xcd, 0xc6, 0xf8,
0x37, 0x66, 0xe5, 0xf9, 0x7b, 0x6c, 0x74, 0x23,
0x73, 0x80, 0x69, 0x00, 0xe4, 0x9f, 0x24, 0xb2,
0x2b, 0x09, 0x75, 0x44, 0xd4, 0x89, 0x6b, 0x42,
0x49, 0x89, 0xb5, 0xe1, 0xeb, 0xac, 0x0f, 0x07,
0xc2, 0x3f, 0x45, 0x98
};
uint8_t unaligned_iv[] = {
0xca, 0xfe, 0xba, 0xbe, 0xfa, 0xce, 0xdb, 0xad
};
uint8_t tag_out_unaligned_iv_tc[] = {
0x36, 0x12, 0xd2, 0xe7, 0x9e, 0x3b, 0x07, 0x85,
0x56, 0x1b, 0xe1, 0x4a, 0xac, 0xa2, 0xfc, 0xcb
};
uint8_t aad_in_unaligned_iv_tc[] = {
0xfe, 0xed, 0xfa, 0xce, 0xde, 0xad, 0xbe, 0xef,
0xfe, 0xed, 0xfa, 0xce, 0xde, 0xad, 0xbe, 0xef,
0xab, 0xad, 0xda, 0xd2
};
uint8_t temp_buff[16U] __attribute__((aligned(128)));
uint8_t calculated_H[16U] __attribute__((aligned(128)));
uint8_t calculated_Y0[16U] __attribute__((aligned(128)));
/* Initialize the AES Parameters */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
(void)memset ((void *)zero_arr, 0, 16U);
/* Initialize the encryption parameters */
aesParams.algoType = DTHE_AES_ECB_MODE;
aesParams.opType = DTHE_AES_ENCRYPT;
aesParams.useKEKMode = FALSE;
aesParams.ptrKey = (uint32_t*)&key_unaligned_iv_tc[0];
aesParams.keyLen = DTHE_AES_KEY_128_SIZE;
aesParams.ptrPlainTextData = (uint32_t*)SOC_virtToPhy(zero_arr);
aesParams.dataLenBytes = 16U;
aesParams.ptrEncryptedData = (uint32_t*)SOC_virtToPhy(calculated_H);
/* Encryption */
status = DTHE_AES_execute(aesHandle, &aesParams);
DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
/* Initialize the AES Parameters */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
(void)memset ((void *)zero_arr, 0, 16U);
/* Initialize the encryption parameters */
aesParams.algoType = DTHE_AES_GHASH_ONLY_MODE;
aesParams.gcmModeSelect = DTHE_AES_GCM_MODE_1;
aesParams.opType = DTHE_AES_DECRYPT;
aesParams.useKEKMode = FALSE;
aesParams.ptrKey = (uint32_t*)&key_unaligned_iv_tc[0];
aesParams.ptrKey1 = (uint32_t*)&calculated_H[0];
aesParams.keyLen = DTHE_AES_KEY_128_SIZE;
aesParams.ptrIV = (uint32_t*)NULL;
aesParams.ptrEncryptedData = (uint32_t*)SOC_virtToPhy(unaligned_iv);
aesParams.ptrPlainTextData = (uint32_t*)SOC_virtToPhy(temp_buff);
aesParams.dataLenBytes = sizeof(unaligned_iv);
aesParams.ptrTag = (uint32_t*)&calculated_Y0[0];
aesParams.ptrAAD = (uint32_t*)SOC_virtToPhy(zero_arr);
aesParams.aadLength = 0U;
/* Encryption */
status = DTHE_AES_execute(aesHandle, &aesParams);
DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
/* Initialize the AES Parameters */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
/* Initialize the encryption parameters */
aesParams.algoType = DTHE_AES_GCM_MODE;
aesParams.gcmModeSelect = DTHE_AES_GCM_MODE_2;
aesParams.opType = DTHE_AES_ENCRYPT;
aesParams.useKEKMode = FALSE;
aesParams.ptrKey = (uint32_t*)&key_unaligned_iv_tc[0];
aesParams.ptrKey1 = (uint32_t*)&calculated_H[0];
aesParams.keyLen = DTHE_AES_KEY_128_SIZE;
aesParams.ptrIV = (uint32_t*)&calculated_Y0[0];
aesParams.ptrPlainTextData = (uint32_t*)SOC_virtToPhy(data_in_unaligned_iv_tc);
aesParams.dataLenBytes = sizeof(data_in_unaligned_iv_tc);
aesParams.ptrEncryptedData = (uint32_t*)SOC_virtToPhy(aesResultEnc);
aesParams.ptrTag = (uint32_t*)&aesGcmTagEnc[0];
aesParams.ptrAAD = (uint32_t*)SOC_virtToPhy(aad_in_unaligned_iv_tc);
aesParams.aadLength = sizeof(aad_in_unaligned_iv_tc);
/* Encryption */
status = DTHE_AES_execute(aesHandle, &aesParams);
DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
status = memcmp(aesResultEnc, data_out_unaligned_iv_tc, sizeof(data_in_unaligned_iv_tc));
if(status == SystemP_SUCCESS)
{
DebugP_log("[CRYPTO] DTHE AES GCM Encryption Unaligned Success!\r\n");
}
else
{
DebugP_log("[CRYPTO] DTHE AES GCM Encryption Unaligned Failed!\r\n");
}
/* comparing Tag result for authentication and verification */
status = memcmp(aesGcmTagEnc, tag_out_unaligned_iv_tc, 16U);
if(status == SystemP_SUCCESS)
{
DebugP_log("[CRYPTO] DTHE AES GCM Tag generation Unaligned Success!\r\n");
}
else
{
DebugP_log("[CRYPTO] DTHE AES GCM Tag generation Unaligned Failed!\r\n");
}
}Hi Nikhil,
Thanks for giving the test case. It is very clear and concise!
I still have one last small question: Could you show me the code in DTHE_AES_controlMode() for dealing with the MACRO DTHE_AES_GHASH_ONLY_MODE?
Hi,
For GHASH we don't set any specific mode using the DTHE_AES_controlMode() API as we are not using the encryption block of AES here.
However, we set only the GCM here as shown below to Mode 1 to same CTRL register, meaning, no encryption (only GHASH)
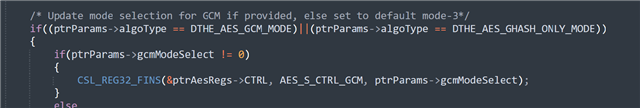
We only use the GHASH block of AES core to calculate the Y0 value.
And from the configuration above, you can see that DTHE_AES_GHASH_ONLY_MODE and DTHE_AES_GCM_MODE_1 and DTHE_AES_DECRYPT, which means, no encryption
Thanks and Regards,
Nikhil Dasan
I noticed the driver implementation for the AES-GCM is missing from the SDK of the AM2732. Could this patch also apply to the AM273x family of MCUs?
Hi,
AM273x SoCs are being handled by a different team. I'm reassigning this thread to the relevant org. for confirmation.
Thanks and Regards,
Nikhil Dasan