Part Number: LP-AM263P
Tool/software:
Hi Team,
I had a few doubts after reviewing the keyring document available in the Secure Resources section of the TI website. I’ve listed them below:
1. I didn’t fully understand the purpose of the salt parameter in the Encryption Extension. ?
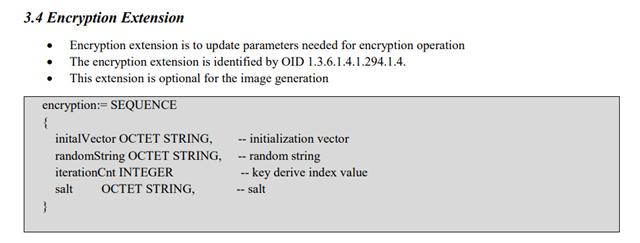
2. Could you explain the purpose of the Key-Derivation Extension? In which scenarios is this extension used?
3.Under Key Writer Extensions, there is an extension called Encrypted AES. It mentions that the key is encrypted using TIFEK. What exactly is TIFEK? Do all AM263Px boards have the same TIFEK?
4.Under Key Writer Extensions, there is an extension called AES Encrypted SMPKH Extension, which contains information about an AES-256 encrypted SMPKH (SHA-512 hashed SMPK public key).
1. With which key is the SMPKH encrypted?
2. At the time of writing to the eFuse OTP memory, is the encrypted SMPKH stored, or the plain SMPKH?
3. What is the purpose of the action_flags field?

5. There is another extension called AES Encrypted SMEK, which contains information about an AES-256 encrypted SMEK key. How is this SMEK key generated?
6. I need more information about the Software Revision App.
7. What is the difference between Version and Key Revision fields under the Key Writer Extension?
Regards,
K.Sravya.


