Part Number: AM2612
Tool/software:
We have previously implemented the SBL_KeyWriter project and successfully applied it. Now we want to only load hsm_firmware in SBL, and then write the MCU key through the UDS service in the app. We replaced the hsm_firmware loaded in the SBL project with our own generated one.
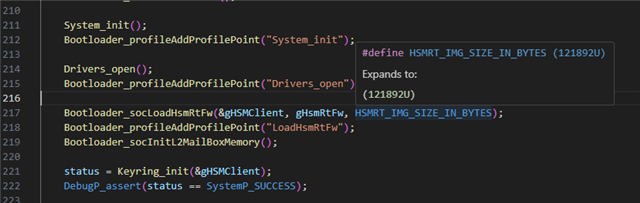
During app initialization, use KeyWriter_Init (without loading hsm_firmware) to init hsm client.
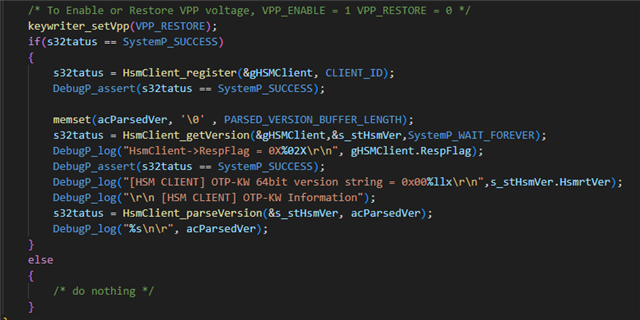
Then write the MCU key to the specified address in the subsequent UDS service received.
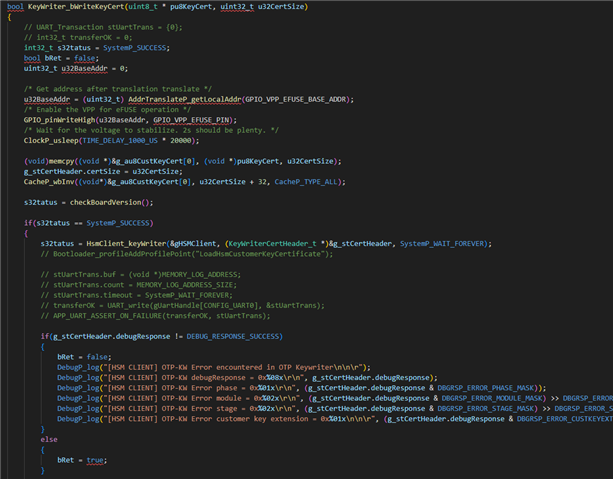
But now we have encountered a problem. After the program executes the write, it returns a successful prompt, but in reality, the write was not successful. We don't know what the reason is.
The memory starting address of the HSM firmware is 0x70038800, with a size of 0x0001dc24, followed by the CertKey address of 0x70056428, with a size of 0x00002004. The Flash allocation is the same as the Sbl_KeyWriter project we have implemented, but the write result is incorrect.

