To implement the CMAC streaming mode functionality, it is necessary to add this feature to the HSM firmware. However, TI does not officially provide this function or a demo running on the HSM side. Therefore, the crypto_aes_stream example from the SDK was adopted (mcu_plus_sdk_am263px_11_00_00_19\examples\security\crypto\dthe_aes\crypto_aes_stream).
This function has been successfully ported to the R5 core and runs correctly. However, when I ported the corresponding program to the M4 core, it failed to operate normally. I have already passed the relevant information such as the original text and CMAC key to the M4 core via SIPC in the form of a service request. Meanwhile, in single‑step mode, the M4 core can run properly (referring to the example: tifs_am263px_11_00_00_01\examples\dthe\aes\crypto_aes_cmac_128).
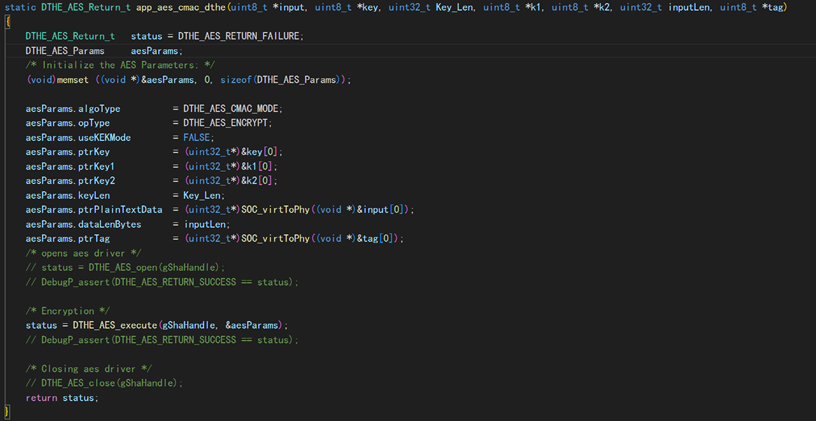
My question is: What modifications are required to successfully port the CMAC streaming mode program—which works on the R5 core—to the M4 core? Especially regarding the following programs, which are the ones I modified to run on the M4 core but are currently experiencing abnormal operation.
static int32_t app_aes_cmac_dthe_stream_start(uint8_t *Key, uint32_t Key_Len, uint8_t *K1, uint8_t *K2)
{
DTHE_AES_Return_t status = DTHE_AES_RETURN_FAILURE;
DTHE_AES_Params aesParams;
/* Initialize the AES Parameters: */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
/* Initialize the encryption parameters: */
aesParams.algoType = DTHE_AES_CMAC_MODE;
aesParams.opType = DTHE_AES_ENCRYPT;
aesParams.useKEKMode = FALSE;
aesParams.ptrKey = (uint32_t*)&Key[0];
aesParams.ptrKey1 = (uint32_t*)&K1[0];
aesParams.ptrKey2 = (uint32_t*)&K2[0];
aesParams.keyLen = Key_Len;
aesParams.ptrPlainTextData = (uint32_t*)NULL;
aesParams.dataLenBytes = 0U;
aesParams.ptrTag = (uint32_t*)NULL;
aesParams.streamState = DTHE_AES_STREAM_INIT;
aesParams.streamSize = 0U;
/* Start Call */
status = DTHE_AES_execute(gShaHandle, &aesParams);
// DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
return (status);
}
static int32_t app_aes_cmac_dthe_stream_update(uint8_t **input, uint32_t ilen)
{
DTHE_AES_Return_t status = DTHE_AES_RETURN_SUCCESS;
DTHE_AES_Params aesParams;
uint32_t n = 0;
if((gCmac_unprocessed_len > 0) &&(ilen > (APP_CRYPTO_AES_BLOCK_LENGTH - gCmac_unprocessed_len )))
{
/* fill the unprocessed buffer */
memcpy(&gCmac_unprocessed_block[gCmac_unprocessed_len], *input, APP_CRYPTO_AES_BLOCK_LENGTH - gCmac_unprocessed_len );
/* Initialize the AES Parameters: */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
/* Initialize the encryption parameters: */
aesParams.algoType = DTHE_AES_CMAC_MODE;
aesParams.opType = DTHE_AES_ENCRYPT;
aesParams.ptrKey = (uint32_t*)NULL;
aesParams.ptrKey1 = (uint32_t*)NULL;
aesParams.ptrKey2 = (uint32_t*)NULL;
aesParams.ptrPlainTextData = (uint32_t*)&gCmac_unprocessed_block[0U];
aesParams.ptrTag = (uint32_t*)NULL;
aesParams.streamState = DTHE_AES_STREAM_UPDATE;
aesParams.streamSize = APP_CRYPTO_AES_BLOCK_LENGTH;
/* Update Call */
status = DTHE_AES_execute(gShaHandle, &aesParams);
// DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
if(status != DTHE_AES_RETURN_SUCCESS)
{
return status;
}
*input += APP_CRYPTO_AES_BLOCK_LENGTH - gCmac_unprocessed_len;
ilen -= APP_CRYPTO_AES_BLOCK_LENGTH - gCmac_unprocessed_len;
gCmac_unprocessed_len = 0;
}
/* n is the number of blocks including any final partial block */
n = ( ilen + APP_CRYPTO_AES_BLOCK_LENGTH - 1 ) / APP_CRYPTO_AES_BLOCK_LENGTH;
if(n>1)
{
/* Initialize the AES Parameters: */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
/* Initialize the encryption parameters: */
aesParams.algoType = DTHE_AES_CMAC_MODE;
aesParams.opType = DTHE_AES_ENCRYPT;
aesParams.ptrKey = (uint32_t*)NULL;
aesParams.ptrKey1 = (uint32_t*)NULL;
aesParams.ptrKey2 = (uint32_t*)NULL;
aesParams.ptrPlainTextData = (uint32_t*)(*input);
aesParams.ptrTag = (uint32_t*)NULL;
aesParams.streamState = DTHE_AES_STREAM_UPDATE;
aesParams.streamSize = (n-1)*APP_CRYPTO_AES_BLOCK_LENGTH;
/* Update Call */
status = DTHE_AES_execute(gShaHandle, &aesParams);
// DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
*input += (n-1)*APP_CRYPTO_AES_BLOCK_LENGTH;
ilen -= (n-1)*APP_CRYPTO_AES_BLOCK_LENGTH;
}
/* If there is data left over that wasn't aligned to a block */
if( ilen > 0 )
{
memcpy( &gCmac_unprocessed_block[gCmac_unprocessed_len], *input, ilen);
gCmac_unprocessed_len += ilen;
}
return (status);
}
static int32_t app_aes_cmac_dthe_stream_finish(uint8_t *tag)
{
DTHE_AES_Return_t status = DTHE_AES_RETURN_FAILURE;
DTHE_AES_Params aesParams;
/* Initialize the AES Parameters: */
(void)memset ((void *)&aesParams, 0, sizeof(DTHE_AES_Params));
/* Initialize the encryption parameters: */
aesParams.algoType = DTHE_AES_CMAC_MODE;
aesParams.opType = DTHE_AES_ENCRYPT;
aesParams.ptrKey = (uint32_t*)NULL;
aesParams.ptrKey1 = (uint32_t*)NULL;
aesParams.ptrKey2 = (uint32_t*)NULL;
aesParams.ptrPlainTextData = (uint32_t*)&gCmac_unprocessed_block[0U];
aesParams.dataLenBytes = 0U;
aesParams.ptrTag = (uint32_t*)SOC_virtToPhy((void *)tag);
aesParams.streamState = DTHE_AES_STREAM_FINISH;
aesParams.streamSize = gCmac_unprocessed_len;
/* Start Call */
status = DTHE_AES_execute(gShaHandle, &aesParams);
// DebugP_assert(DTHE_AES_RETURN_SUCCESS == status);
memset(gCmac_unprocessed_block, 0U, APP_CRYPTO_AES_BLOCK_LENGTH);
gCmac_unprocessed_len = 0;
return (status);
}
Thank you for your responses, experts








