Other Parts Discussed in Thread: TMDS243EVM
We have at least two TMDS243EVM PROC101C(005). Both have a Sitara with the printing:
XAM2434B
SFGHIALV
according to the data sheet this should a be a secure processor: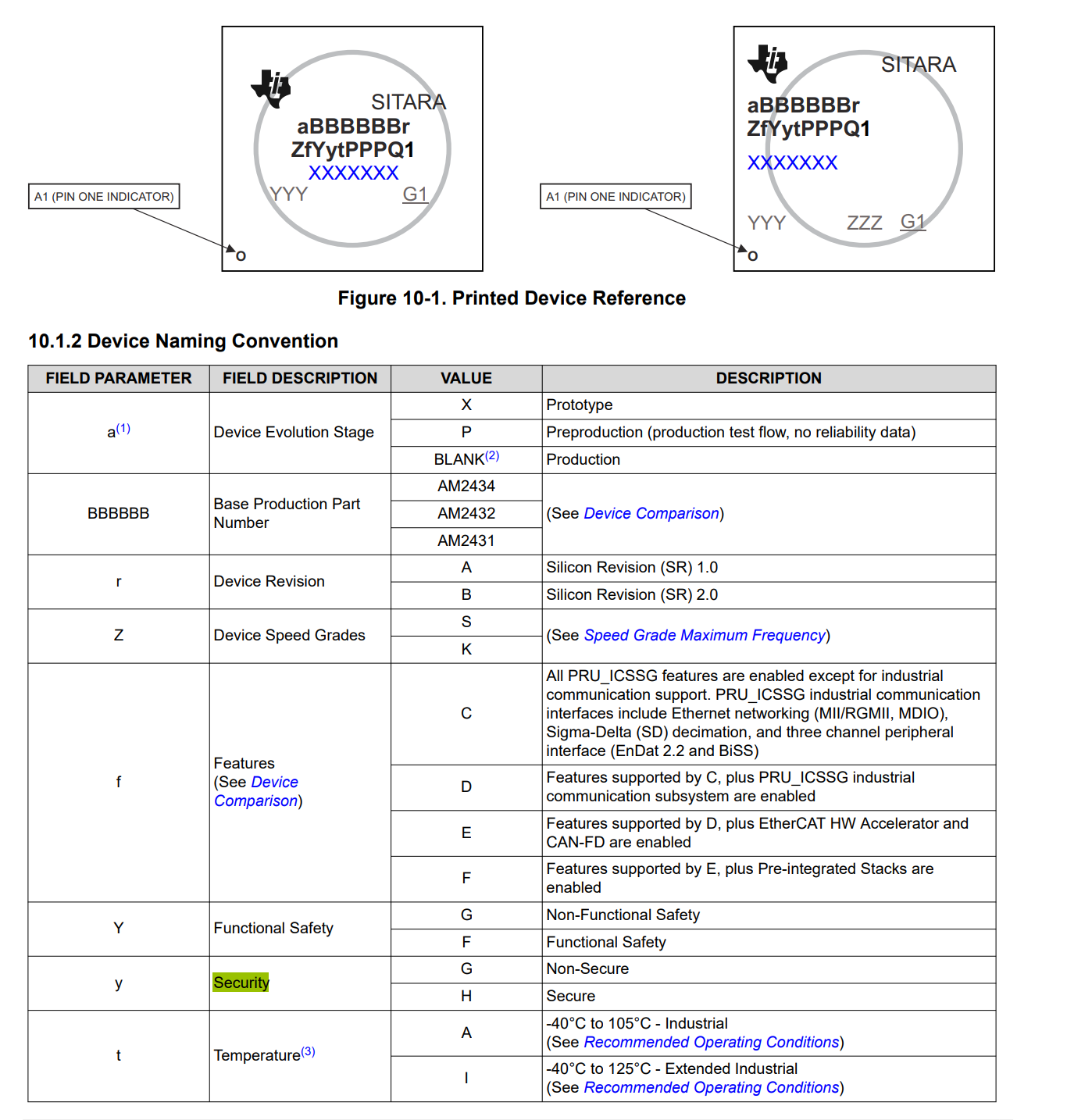
But if we read our the JTAG_UDER_ID-register which should give info ybout the SoC in firmware, we see it's not set as a secure Sitara:

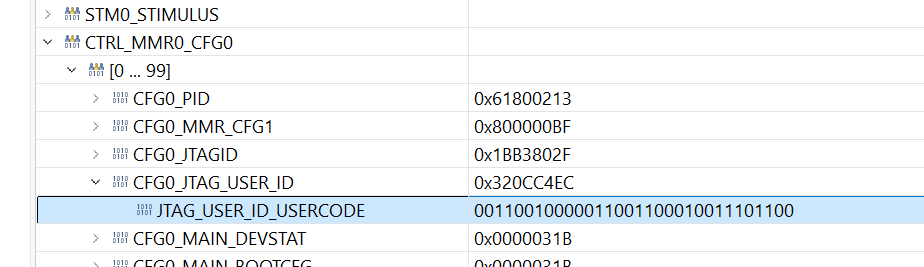
if we check the bits:
JTAG_USER_ID_USERCODE 00110010000011001100010011101100
we have:
PKG: 100: 4 ALV (correct)
TEMP: 101: -40-125°C
SPEED: 10011: 23
SECURITY: 0 (Non-Secure!)
SAFETY: 0 (no safety, ok!)
the JTAG-deviceid is also not the one of the listed possibilitites in the tram: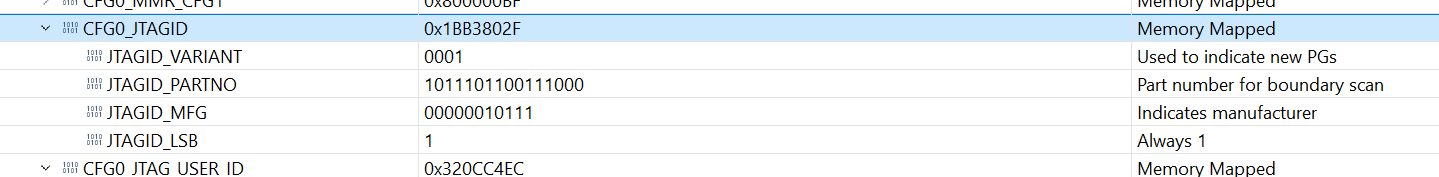
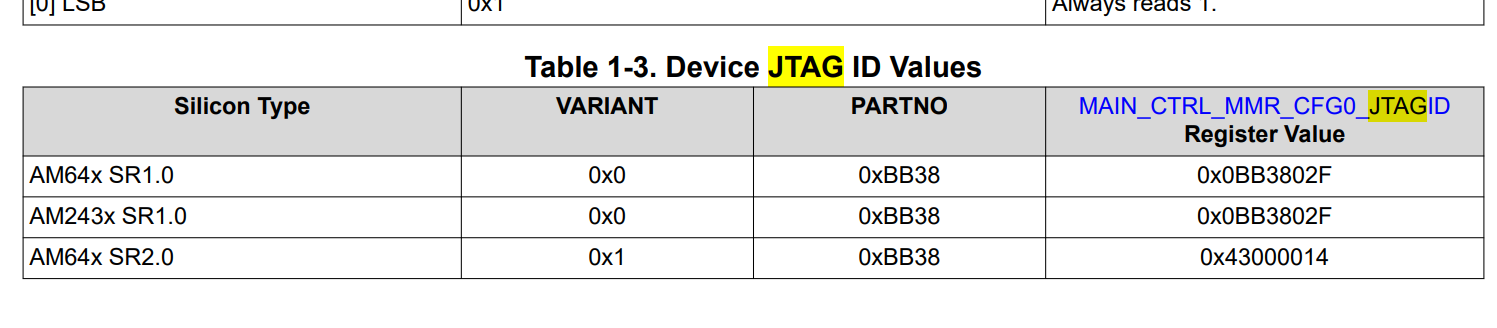
or the list is not complete... (TRM Rev H).
This is now an unfortunate situation, which needs to be clarified.
We have devices out there with GP-Variants of the Sitara and they also need to be updated in the future. We are using the Industrial Comms SDK 11 and the contained mcu-plus-sdk. In the past we just moved out the SysFw.bin of the GP-version and stored it at our side, since it was not available anymore.
So the problem came up, when we tried to install our Bootloader on the evm. Our update process checks the registers and installs according to the security bit the GP- or hs-fs-signed bootloader, each with their matching SysFw.
We then noticed the evm does not boot at all anymore. After some trying around we saw it installs the wrong GP-based bootloader, because the security bit is not set. We then installed the hs-fs-bootloader without the check for the security-flag and it worked properly after that.
We also have other Sitara-devices (without an leading X) and those give the right values via the JTAG_USER_ID-register.
So what is the situation here? Are there other variants of those devices which do give different information in the register than the one printed on the housing?
Or is it just, that the old SysFw.bin from... I dunno mcu-plus-sdk 8? does not work anymore with the latest mcu-plus-sdk-versions?
best regards
Felix

