Part Number: AM62P-Q1
Other Parts Discussed in Thread: AM62P
Hi, Ti Expert,
This is from Aumovio security team, We have AM62Px EVM board---SK-AM62P-LP. and try to use it to develop security relevant features for Automotive ECU poduct.
Now for starting, we have some questions:
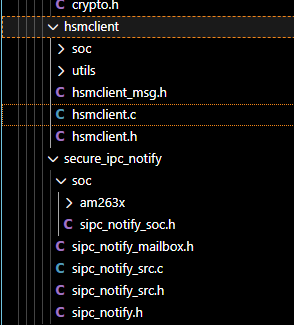
- We download the SDK "mcu_plus_sdk_am62px_11_02_00_23", but don't found any security driver or HSM (TIFS) APIs, compared with "mcu_plus_sdk_am263x_11_01_00_19" , it has HsmClient and SIPC package, why in am62px SDK, don't have it? I got info, in "3.4.1. Device Security — Processor SDK AM62Px Documentation" link, will have description, yes, it has, but where have the package? below image show the am263x SDK:
- Some document mentioned definition: TIFS, HSM, SYSFW... what is the different between them? As my understanding, TIFS is your TI special HSM, will running in M4F core 0. but also have 3rd part HSM (optional), it will running in M4F core 1.
- For TIFS, whether your TIFS firmware can be used for comercial?
- If we integrate 3rd part HSM firmware, also need the TIFS FW during boot sequence? or replace it with 3p HSM directly? TIFS is necessary for boot sequence?
- During secure boot, for auth each FW (R5F SBL, HSM, A53 u-boot...), whether will use same key set: SMEK/SMPK..., or will use different keys during each step?
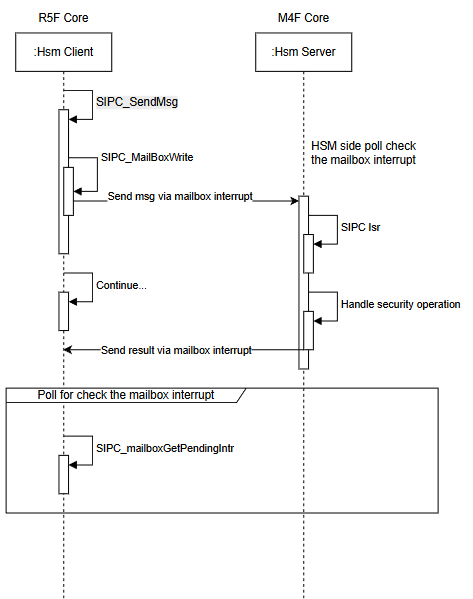
- As we know, in AM263x CPU, the Security operation will be handled by HSM core, the R5F or A53 cores will only request it to HSM core, is it same with AM62Px? if yes, does below sequence correct?
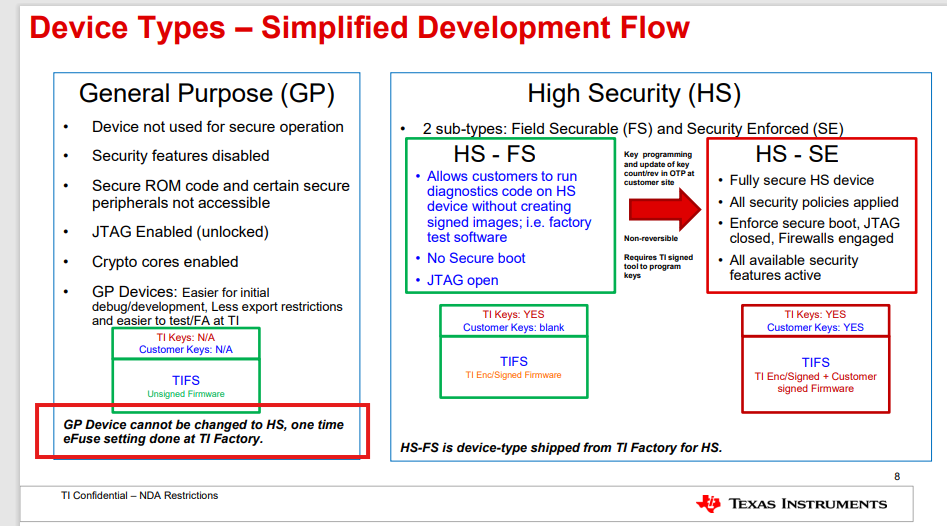
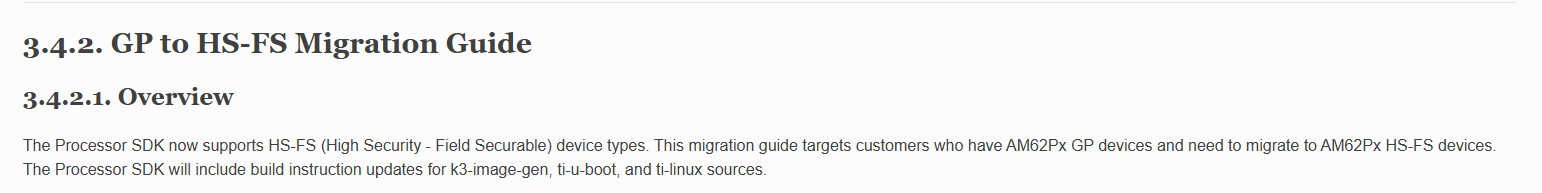
- For Device type, I got info: "GP device cannot switch to HS", but in link "3.4.1. Device Security — Processor SDK AM62Px Documentation ", it mentioned can mogration GP to HS-FS, please help to clarify:
Thanks in advance!