After fighting 6 mounts ago the Tivaware Ethernet Boot Loader expecting it to be some what functional, it ended up actually being flashed in DOA order.
Revisiting software Boot Loader have now fixed a few fatal issues that were keeping it in DOA status at least with Rev 1 silicon. The DID0 register will reveal Rev1 silicon in your chip can be made to split hairs with EBL performing some magic tricks.
The SYSCLK was killed by a patch now (commented out) , Bamboozled CCS5 ICDI debug simulator. No Hexadecimal decode for instructions show in the disassembly window for the source listings.
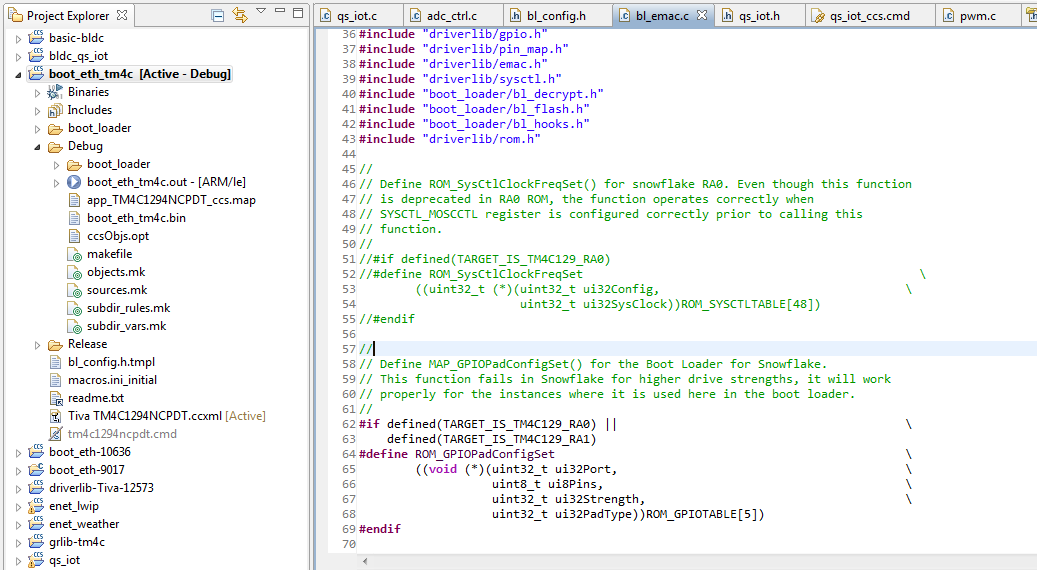
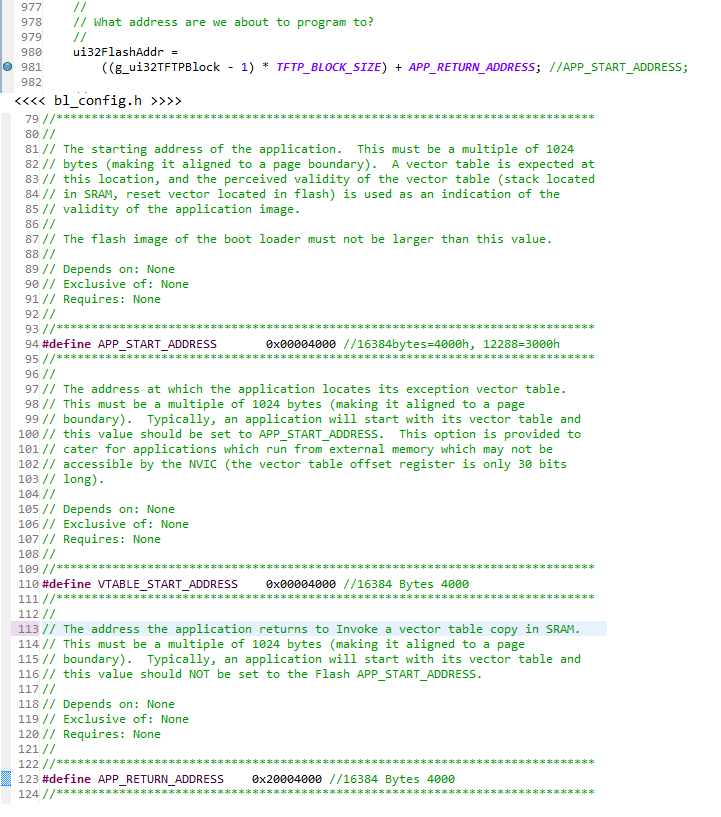
Debug: Shown top is (bl_emac.c) and the addition of an (Application Return Address). Found the TFTP data transfer & Flash loads into SRAM avoids writing flash memory corrupting the Application and Boot loader.
Packet Sniffer trace shows what appears to be a file name header sent from the TFTP client back to the server.
Sniffer fails to capture the flash image 512 byte blocks in packets being transferred.