Other Parts Discussed in Thread: UNIFLASH, C2000WARE
Tool/software:
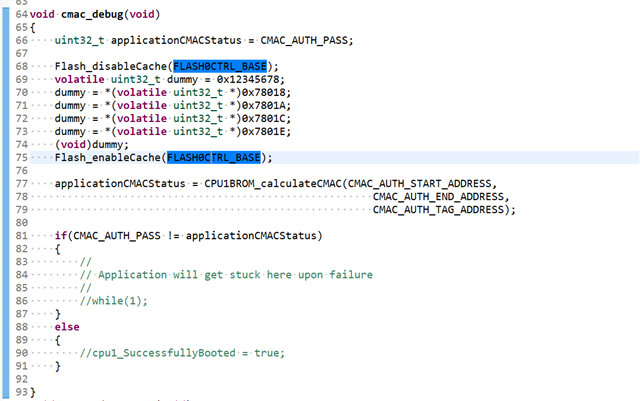
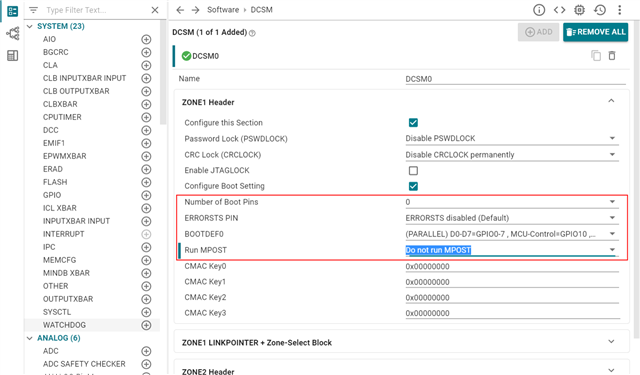
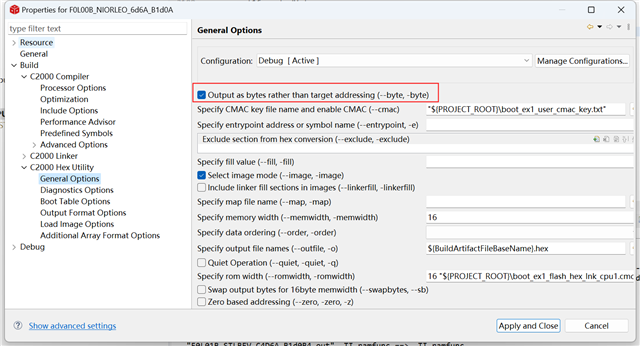
I call the API function CPU1BROM_calculateCMAC() as follow in customer bootloader as debug software to check application, and I donot enable the secure boot.
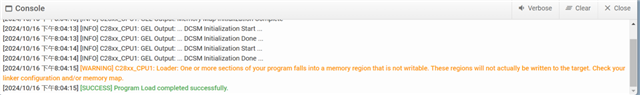
But the customer bootloader cannot run normally.
When I only comment out the function CPU1BROM_calculateCMAC(), the customer bootloader can run normally.
So is there anything else I need pay attention to?