I'm trying to upgrade the MSPG2553 using the steps outlined in this support ticket: https://e2e.ti.com/support/microcontrollers/msp-low-power-microcontrollers-group/msp430/f/msp-low-power-microcontroller-forum/991977/msp430g2553-msp430g2553-uart-firmware-update-using-bsl-problem/3663997?tisearch=e2e-sitesearch&keymatch=BSLSKEY#3663997
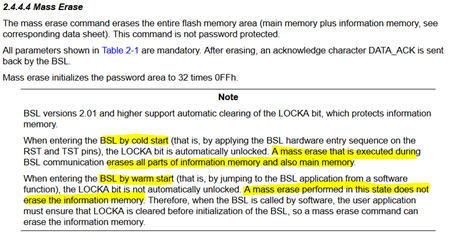
Essentially, hardware entry to BSL, then mass erase, then enter default password, then program.
Is there a way to protect the INFO-A segment from a mass erase in this case? We've confirmed in our testing that hardware entry to BSL disables the LOCKA bit with no apparent way to prevent this. We've also tried setting the BSLSKEY to 0x0000 as suggested by the linked ticket. Doing so prevents an erase on a bad password, but doesn't change the behavior of a mass erase.
Is there anything else we can do? Ideally we do not want to go to a backup plan of either software entry to BSL or having to enter a password before erasing the chip.