Dear Support,
According to SLAU610B, my customer is using BSL RX Password command to access BSL in our MSP430FR2033.
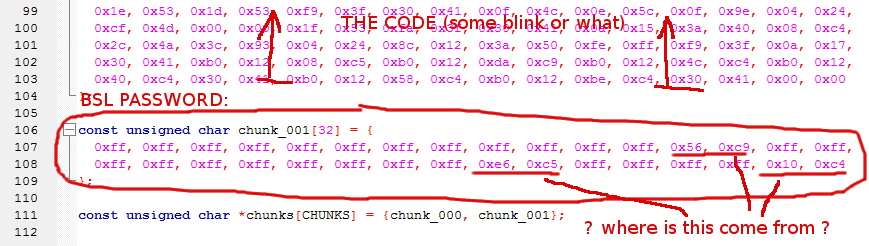
The password consists of 32 last bytes of FRAM memory (their code). Can they use those bytes to identify valid firmware? What is the content of those bytes and how is it generated?
They idea is to do like this: start every time into BSL with given password, and if it passes they know the firmware is correct. So they can cycle power and go on.
If it wont pass, start it with empty password and bootload firmware.
So they need this password to be unique for firmware version. They found out there are already some data in, but don't know what they mean and if these are modifiable for example filling in the timestamp.
I provide in attachment the sample hex file and it's C code form which they embed into upper system firmware (section).
Best regards,
Alberto