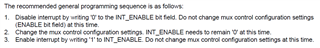
Hi,
My customer is testing dual core operation on AM6442.
A53 Core0 boots up with u-boot (Linux SDK) and A53 Core1 is loaded with RTOS image using JTAG ICE.
On Core1 side, below codes are loaded and executed.
Accessing GPIOMUX_INTRTR0_MUXCTRL0 register at 0x00A00004 causes the system crash.
unsigned int data;
data = *((unsigned int*)0x00A00004);
data ^= (1 << 16);
*(unsigned int*)(0x00A00004) = data; // 1. Disable interrupt
*(unsigned int*)(0x00A00004) = 0x70; // 2. Set GPIOMUX_INTRTR0_IN_112
*(unsigned int*)(0x00A00004) |= (1 << 16); // 3. Enable interrupt
Core0 side is also crashed and below is u-boot console log.
While above code is running on Core1, Core0 does not do anything.
ERROR: Unhandled External Abort received on 0x80000001 from S-EL1 ERROR: exception reason=0 syndrome=0xbf000002 Unhandled Exception from EL1 x0 = 0x0000000000000000 x1 = 0x0000000000a00004 x2 = 0x0000000000000008 x3 = 0x0000000000000008 x4 = 0x0000000000000001 x5 = 0x0000000000000000 x6 = 0x0000000000000000 x7 = 0xffffffffffffffff x8 = 0x0000000000000000 x9 = 0xffffffffffffffff x10 = 0x0000000000000004 x11 = 0x0000000000000002 x12 = 0x0000000000000000 x13 = 0x0000000000000000 x14 = 0x0000000000000000 x15 = 0x0000000000000000 x16 = 0x0000000000000000 x17 = 0x0000000000000000 x18 = 0x0000000000000000 x19 = 0x0000000000000000 x20 = 0x0000000000000000 x21 = 0x0000000000000000 x22 = 0x0000000000000000 x23 = 0x0000000000000000 x24 = 0x0000000000000000 x25 = 0x0000000000000000 x26 = 0x0000000000000000 x27 = 0x0000000000000000 x28 = 0x0000000000000000 x29 = 0x0000000000000000 x30 = 0x00000000a57b1d20 scr_el3 = 0x000000000000073d sctlr_el3 = 0x0000000030cd183f cptr_el3 = 0x0000000000000000 tcr_el3 = 0x0000000080803520 daif = 0x00000000000002c0 mair_el3 = 0x00000000004404ff spsr_el3 = 0x00000000600001c4 elr_el3 = 0x00000000a57b1ce8 ttbr0_el3 = 0x000000007000d740 esr_el3 = 0x00000000bf000002 far_el3 = 0xfddbbfff42462c62 spsr_el1 = 0x0000000000000000 elr_el1 = 0x0000000000000000 spsr_abt = 0x0000000000000000 spsr_und = 0x0000000000000000 spsr_irq = 0x0000000000000000 spsr_fiq = 0x0000000000000000 sctlr_el1 = 0x0000000000c0181d actlr_el1 = 0x0000000000000000 cpacr_el1 = 0x0000000000300000 csselr_el1 = 0x0000000000000002 sp_el1 = 0x00000000a6000000 esr_el1 = 0x0000000000000000 ttbr0_el1 = 0x00000000a5e00000 ttbr1_el1 = 0x00000000a5e08000 mair_el1 = 0x00ffbb440c080400 amair_el1 = 0x0000000000000000 tcr_el1 = 0x0000000535983598 tpidr_el1 = 0x0000000000000000 tpidr_el0 = 0x0000000000000000 tpidrro_el0 = 0x0000000000000000 par_el1 = 0x0000000000000000 mpidr_el1 = 0x0000000080000001 afsr0_el1 = 0x0000000000000000 afsr1_el1 = 0x0000000000000000 contextidr_el1 = 0x0000000000000000 vbar_el1 = 0x00000000a5400800 cntp_ctl_el0 = 0x0000000000000000 cntp_cval_el0 = 0x0000000000000000 cntv_ctl_el0 = 0x0000000000000000 cntv_cval_el0 = 0x0000000000000000 cntkctl_el1 = 0x0000000000000000 sp_el0 = 0x000000007000ac50 isr_el1 = 0x0000000000000000 dacr32_el2 = 0x0000000000000000 ifsr32_el2 = 0x0000000000000000 cpuectlr_el1 = 0x0000000000000040 cpumerrsr_el1 = 0x00000000121406d9 l2merrsr_el1 = 0x0000000010140758 cpuactlr_el1 = 0x00001000090ca000
If Core1 side code is executed step by step from debugger, it works fine. There is no system crash.
GPIOMUX_INTRTR0_MUXCTRL0 register is properly written with value 0x00010070.
What is happing?
Thanks and regards,
Koichiro Tashiro