Part Number: TMDS64GPEVM
Hello,
I'm not able to communicate with the TI AM64x EVM Board via Micro Serial COM with my Laptop.
SD Card was loaded with Bootable Linux and other binaries already. Please help.
Thanks
Ajith K
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
Hi Ajith,
Have you followed the steps for Setting up the UART terminal as described here
More specifically, have you installed the UART to USB drivers?
Regards,
Prashant
Hi Prashant,
Thanks for the response!
I have tried the switch settings change to see the CC, which is getting printed on the UART Terminal in every 2-3 seconds as per the new switch(SW2, SW3) settings.
However, when I had changed back to the original settings, no communication was happening on my UART Terminal. Please note that I have not installed CCS on my Laptop nor Python. UART Communication was happening on my UART Terminal before without CCS/Python. Please let me know if you need further information.
Thanks
Ajith K.
Hi Ajith,
I am not getting what exactly the issue is. You are able to see the characters C getting printed on UART when using the new switch settings. I am not getting why you are trying different switch settings.
Regards,
Prashant
Hi Prashant,
After making those switch settings, change I was just experimenting whether anything is being displayed on the UART/Serial COM Screen.
When I had changed back to the original settings, no communication was happening. Hope that clears it up.
SD Card contains the following binaries:
|
/dev/sda1 |
tiboot3.bin' 'BCP_RTOS.bin' |
By the way, on the SD Card what all binaries needs to be there for booting it up? Please advise.
Thank you!
Ajith K.
Hi Ajith,
By original settings, do you mean to say you set the switch settings to SD card boot mode. But when you power on the board, no logs are coming on the UART?
By the way, on the SD Card what all binaries needs to be there for booting it up?
Yes, all images are required for successful boot. Though ROM only needs tiboot3.bin. After tiboot3.bin is booted, it will then boot other images.
Regards,
Prashant
Hi Prashant,
Sorry for the delay.
>>
By original settings, do you mean to say you set the switch settings to SD card boot mode. But when you power on the board, no logs are coming on the UART?
Ans: No logs are being displayed on the Board when I switch ON the Power of the Board. It looks like some other issue as it was working earlier. Please let me know any other troubleshooting steps.
Thanks
Ajith K
Hi Prashant,
I have made the SW2 and SW3 Board settings again back to SD Card Boot mode and now the following logs are being displayed:
▒
U-Boot SPL 2021.01 (Nov 09 2022 - 11:29:00 +0900)
SYSFW ABI: 3.1 (firmware rev 0x0015 '21.5.0--v2021.05 (Terrific Llam')
SPL initial stack usage: 13392 bytes
▒
U-Boot SPL 2021.01 (Nov 09 2022 - 11:29:00 +0900)
SYSFW ABI: 3.1 (firmware rev 0x0015 '21.5.0--v2021.05 (Terrific Llam')
SPL initial stack usage: 13392 bytes
▒
U-Boot SPL 2021.01 (Nov 09 2022 - 11:29:00 +0900)
SYSFW ABI: 3.1 (firmware rev 0x0015 '21.5.0--v2021.05 (Terrific Llam')
SPL initial stack usage: 13392 bytes
Does it mean that SD Card contents are corrupted? If it so, please let me know from where I can download the SD Card bootable binaries so that I can re-install it.
Thanks, Ajith K
Hi Ajith,
Can you please share the UART string that comes on the UART terminal when the board is booted in UART boot mode.
Not sure. I've not installed any SDK yet.
How did you get the binaries in SD card then? Did you use WIC image and a flashing tool to flash the SD card?
Regards,
Prashant
I've configured KiTTy which was displaying the UART string:
▒
U-Boot SPL 2021.01 (Nov 09 2022 - 11:29:00 +0900)
SYSFW ABI: 3.1 (firmware rev 0x0015 '21.5.0--v2021.05 (Terrific Llam')
SPL initial stack usage: 13392 bytes
Attached please find the port settings:
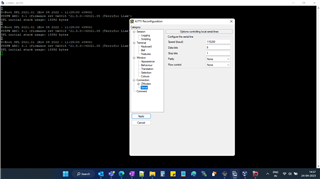
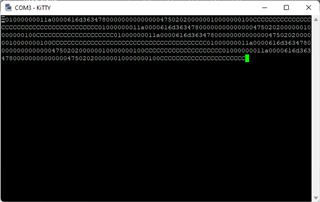
So far in the UART mode, the following hex data was displayed on the screen:
▒01000000011a0000616d36347800000000000000475020200000010000000100CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC01000000011a0000616d36347800000000000000475020200000010000000100CCCCCCCCCCCCCCCCCCCC01000000011a0000616d36347800000000000000475020200000010000000100CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC01000000011a0000616d36347800000000000000475020200000010000000100CCCCCCCCCCCCCCCCCCCC01000000011a0000616d36347800000000000000475020200000010000000100CCCCCCCCCCCCCCCCCCCC
Hope that helps in debugging!
--Ajith K
Hi Ajith,
Thanks! You are indeed working with GP device. Please have a look at the below guide
Since, you are working with GP (SR1.0), please make sure you follow the section "Boot SD card on AM64x SR1.0" in the above guide.
The prebuilt images from PSDK are available at
https://www.ti.com/tool/download/PROCESSOR-SDK-LINUX-AM64X
Regards,
Prashant
I had executed the following commad as well, though the tar commands were not successful.
Preparation foruboot partition
$ sudo mount /dev/sdc1 /mnt
$ sudo cp /BOOT/uEnv.txt /mnt
$ sudo cp /BOOT/tiboot3.bin /mnt
$ sudo cp /BOOT/tispl.bin /mnt
$ sudo cp /BOOT/u-boot.img /mnt/
$ sudo cp /BOOT/BCP_RTOS.bin /mnt
$ sudo umount /mnt
Preparation for uroot partition
$ sudo mount /dev/sdc2 /mnt
$ sudo tar xf /ROOT/skeliosv3_armhf_seriallogin_210413.tar.xz -C /mnt //file name varies with skelios's version
Copy kernel and devicetree to uroot partition
$ sudo cp /OS/Image /mnt/boot
$ sudo cp /OS/k3-am642-evm.dtb /mnt/boot
$ sudo tar xkf /ROOT/linux-5.4.91-g1af1264b70-arm64.tar.gz -C /mnt //file name varies."k"option is mandatory.
$ sudo umount /mnt
$ sync
Hi Ajith,
hope it is correct, pls confirm
Yes, the switch settings shown in the image are correct.
To prepare the SD card, you can download the prebuilt WIC image from the previously shared PSDK page link. Once the WIC image is flashed, please make sure you follow the section "Boot SD card on AM64x SR1.0" in the below link.
Regards,
Prashant
Hi Prasant,
We don't use WIC image flash on the Board. Could you please advise me the minimum binary that needs to be put in the SD CARD to display sometyhing on the COM Terminal with bash prompt on root partition? Should I change the settings of SW2 and SW3 Switches to boot in SD Card? Thanks, Ajith K
Currently, nothing is being displayed on the COM Terminal. As of now the following files are present in the sdc1 mounted partition:
sdc
|-sdc1 vfat boot 986C-76C1 /platform/mnt/sdc
`-sdc2 ext4 bd141890-dcc2-42fe-bf50-e1c0435734ee
mtdblock0
root@MFP13560775:/platform/mnt/sdc1> ls
ODB$ tiboot3.bin u-boot.img uboot.env
System Volume Information tispl.bin uEnv.txt wificfg
root@MFP13560775:/platform/mnt/sdc1>
It would be great if you could advise on how to mount sdc2 and do the following operations:
Preparation for uroot partition
$ sudo mount /dev/sdc2 /mnt
$ sudo tar xf /ROOT/skeliosv3_armhf_seriallogin_210413.tar.xz -C /mnt //file name varies with skelios's version
Copy kernel and devicetree to uroot partition
$ sudo cp /OS/Image /mnt/boot
$ sudo cp /OS/k3-am642-evm.dtb /mnt/boot
$ sudo tar xkf /ROOT/linux-5.4.91-g1af1264b70-arm64.tar.gz -C /mnt //file name varies."k"option is mandatory.
$ sudo umount /mnt
$ sync
Hi Ajith,
Should I change the settings of SW2 and SW3 Switches to boot in SD Card?
Since you are working with SD card then yes please keep the switch settings to SD card. Then if the boot partition on your SD card contains at least the following three binaries (tiboot3.bin, tispl.bin, u-boot.img) then you should be able to get to U-Boot prompt.
Once you are able to get to U-Boot prompt, we will move forward.
Regards,
Prashant
Hi Prashant,
I'm getting only the following output on the COM5 after mounting the BOOT partition on sdc1:
▒
U-Boot SPL 2021.01 (Nov 09 2022 - 11:29:00 +0900)
SYSFW ABI: 3.1 (firmware rev 0x0015 '21.5.0--v2021.05 (Terrific Llam')
SPL initial stack usage: 13392 bytes
Commands used are:
root@MFP13560775:/platform/mnt> sudo mount /dev/sdc1 /mnt
root@MFP13560775:/platform/mnt> sudo cp /BOOT/uEnv.txt /mnt
root@MFP13560775:/platform/mnt> sudo cp /BOOT/tiboot3.bin /mnt
root@MFP13560775:/platform/mnt> sudo cp /BOOT/tispl.bin /mnt
root@MFP13560775:/platform/mnt> sudo cp /BOOT/u-boot.img /mnt
root@MFP13560775:/platform/mnt> sudo cp /BOOT/BCP_RTOS.bin /mnt
root@MFP13560775:/platform/mnt> sudo umount /mnt
root@MFP13560775:/platform/mnt> cd /mnt
root@MFP13560775:/mnt> ls
hdd sdc1
root@MFP13560775:/mnt> cd sdc1/
root@MFP13560775:/mnt/sdc1> ls
BCP_RTOS.bin System Volume Information tispl.bin uEnv.txt wificfg
ODB$ tiboot3.bin u-boot.img uboot.env
root@MFP13560775:/mnt/sdc1> cd /
root@MFP13560775:/> sudo mount /dev/sdc2 /mnt
sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:33:19 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:33:19 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:33:19 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:33:19 MFP13560775 sdc: Retry Count 2 (Max 5)
sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:34:21 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:34:21 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:34:21 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:34:21 MFP13560775 sdc: Retry Count 4 (Max 5)
sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:36:25 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:36:25 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:36:25 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 25 19:36:25 MFP13560775 sdc: Retry Count 2 (Max 5)
sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:37:27 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:37:27 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:37:27 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 25 19:37:27 MFP13560775 sdc: Retry Count 4 (Max 5)
mount: /dev/sdc2: can't read superblock
root@MFP13560775:/> sudo mount /dev/sdc2 /platform/mnt
mount: /dev/sdc2: can't read superblock
root@MFP13560775:/>
I can't mount ROOT partition on /dev/sdc2 as per the error above.
Any help would be appreciated.
-Thanks, Ajith K.
Hi Prasant,
Could you pls share the latest TI Binaries so that I can replace the existing binaries in the BOOT partition /dev/sdc1 of SD Card.
Today, I'm able to mount ROOT partition /dev/sdc2 , however the tar xf extraction commad was unsuccessful.
......
tar: etc/ssl/certs/D-TRUST_Root_Class_3_CA_2_2009.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GlobalSign_ECC_Root_CA_-_R5.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/AffirmTrust_Premium_ECC.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/VeriSign_Universal_Root_Certification_Authority.pem: Cannot unlink: Read-
tar: etc/ssl/certs/toshiba.cer.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GeoTrust_Primary_Certification_Authority_-_G2.pem: Cannot unlink: Read-on
tar: etc/ssl/certs/QuoVadis_Root_CA_3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Hellenic_Academic_and_Research_Institutions_ECC_RootCA_2015.pem: Cannot u
tar: etc/ssl/certs/emSign_ECC_Root_CA_-_G3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Trustwave_Global_Certification_Authority.pem: Cannot unlink: Read-only fi
tar: etc/ssl/certs/Cybertrust_Global_Root.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GlobalSign_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/TeliaSonera_Root_CA_v1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/SecureSign_RootCA11.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/DigiCert_High_Assurance_EV_Root_CA.pem: Cannot unlink: Read-only file sys
tar: etc/ssl/certs/GlobalSign_Root_CA_-_R6.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/DigiCert_Assured_ID_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/SZAFIR_ROOT_CA2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Go_Daddy_Class_2_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Amazon_Root_CA_3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/emSign_Root_CA_-_C1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/EC-ACC.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/AffirmTrust_Premium.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Entrust_Root_Certification_Authority_-_G4.pem: Cannot unlink: Read-only f
tar: etc/ssl/certs/DigiCert_Global_Root_G2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GlobalSign_Root_CA_-_R3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Izenpe.com.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/USERTrust_RSA_Certification_Authority.pem: Cannot unlink: Read-only file
tar: etc/ssl/certs/GTS_Root_R4.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Amazon_Root_CA_2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/COMODO_Certification_Authority.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/SSL.com_EV_Root_Certification_Authority_ECC.pem: Cannot unlink: Read-only
tar: etc/ssl/certs/COMODO_ECC_Certification_Authority.pem: Cannot unlink: Read-only file sys
tar: etc/ssl/certs/TWCA_Global_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Actalis_Authentication_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Amazon_Root_CA_1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GTS_Root_R2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/e-Szigno_Root_CA_2017.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/QuoVadis_Root_CA_2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/UCA_Global_G2_Root.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Hongkong_Post_Root_CA_3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/OISTE_WISeKey_Global_Root_GC_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/certSIGN_Root_CA_G2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/ePKI_Root_Certification_Authority.pem: Cannot unlink: Read-only file syst
tar: etc/ssl/certs/TrustCor_RootCert_CA-1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Go_Daddy_Root_Certificate_Authority_-_G2.pem: Cannot unlink: Read-only fi
tar: etc/ssl/certs/IdenTrust_Public_Sector_Root_CA_1.pem: Cannot unlink: Read-only file syst
tar: etc/ssl/certs/SSL.com_Root_Certification_Authority_ECC.pem: Cannot unlink: Read-only fi
tar: etc/ssl/certs/Certum_Trusted_Network_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/NAVER_Global_Root_Certification_Authority.pem: Cannot unlink: Read-only f
tar: etc/ssl/certs/Entrust_Root_Certification_Authority_-_EC1.pem: Cannot unlink: Read-only
tar: etc/ssl/certs/Entrust.net_Premium_2048_Secure_Server_CA.pem: Cannot unlink: Read-only f
tar: etc/ssl/certs/Security_Communication_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Entrust_Root_Certification_Authority_-_G2.pem: Cannot unlink: Read-only f
tar: etc/ssl/certs/D-TRUST_Root_Class_3_CA_2_EV_2009.pem: Cannot unlink: Read-only file syst
tar: etc/ssl/certs/Certigna.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Secure_Global_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/NetLock_Arany_=Class_Gold=_F\305\221tan\303\272s\303\255tv\303\241ny.pem:
tar: etc/ssl/certs/SwissSign_Silver_CA_-_G2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/DigiCert_Assured_ID_Root_G2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/certSIGN_ROOT_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Trustwave_Global_ECC_P256_Certification_Authority.pem: Cannot unlink: Rea
tar: etc/ssl/certs/Global_Chambersign_Root_-_2008.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/ACCVRAIZ1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Comodo_AAA_Services_root.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/TrustCor_ECA-1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/T-TeleSec_GlobalRoot_Class_3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/UCA_Extended_Validation_Root.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Autoridad_de_Certificacion_Firmaprofesional_CIF_A62634068.pem: Cannot unl
tar: etc/ssl/certs/Microsoft_ECC_Root_Certificate_Authority_2017.pem: Cannot unlink: Read-on
tar: etc/ssl/certs/DigiCert_Global_Root_G3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/QuoVadis_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/E-Tugra_Certification_Authority.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Staat_der_Nederlanden_EV_Root_CA.pem: Cannot unlink: Read-only file syste
tar: etc/ssl/certs/Atos_TrustedRoot_2011.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/SecureTrust_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/DigiCert_Trusted_Root_G4.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/DST_Root_CA_X3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/AC_RAIZ_FNMT-RCM.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/AffirmTrust_Commercial.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/emSign_ECC_Root_CA_-_C3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/TWCA_Root_Certification_Authority.pem: Cannot unlink: Read-only file syst
tar: etc/ssl/certs/SSL.com_Root_Certification_Authority_RSA.pem: Cannot unlink: Read-only fi
tar: etc/ssl/certs/COMODO_RSA_Certification_Authority.pem: Cannot unlink: Read-only file sys
tar: etc/ssl/certs/DigiCert_Assured_ID_Root_G3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Chambers_of_Commerce_Root_-_2008.pem: Cannot unlink: Read-only file syste
tar: etc/ssl/certs/OISTE_WISeKey_Global_Root_GB_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Security_Communication_RootCA2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GlobalSign_ECC_Root_CA_-_R4.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/SSL.com_EV_Root_Certification_Authority_RSA_R2.pem: Cannot unlink: Read-o
tar: etc/ssl/certs/GDCA_TrustAUTH_R5_ROOT.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Certigna_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Microsec_e-Szigno_Root_CA_2009.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/ISRG_Root_X1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Hellenic_Academic_and_Research_Institutions_RootCA_2015.pem: Cannot unlin
tar: etc/ssl/certs/GTS_Root_R1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/IdenTrust_Commercial_Root_CA_1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/TUBITAK_Kamu_SM_SSL_Kok_Sertifikasi_-_Surum_1.pem: Cannot unlink: Read-on
tar: etc/ssl/certs/toshibaca.cer.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Buypass_Class_3_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/emSign_Root_CA_-_G1.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Buypass_Class_2_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Amazon_Root_CA_4.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Staat_der_Nederlanden_Root_CA_-_G3.pem: Cannot unlink: Read-only file sys
tar: etc/ssl/certs/Certum_Trusted_Network_CA_2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Microsoft_RSA_Root_Certificate_Authority_2017.pem: Cannot unlink: Read-on
tar: etc/ssl/certs/CFCA_EV_ROOT.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Hellenic_Academic_and_Research_Institutions_RootCA_2011.pem: Cannot unlin
tar: etc/ssl/certs/DigiCert_Global_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Entrust_Root_Certification_Authority.pem: Cannot unlink: Read-only file s
tar: etc/ssl/certs/GlobalSign_Root_CA_-_R2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/TrustCor_RootCert_CA-2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/USERTrust_ECC_Certification_Authority.pem: Cannot unlink: Read-only file
tar: etc/ssl/certs/Trustwave_Global_ECC_P384_Certification_Authority.pem: Cannot unlink: Rea
tar: etc/ssl/certs/Network_Solutions_Certificate_Authority.pem: Cannot unlink: Read-only fil
tar: etc/ssl/certs/AffirmTrust_Networking.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/GTS_Root_R3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/QuoVadis_Root_CA_2_G3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/SwissSign_Gold_CA_-_G2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/XRamp_Global_CA_Root.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/T-TeleSec_GlobalRoot_Class_2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Baltimore_CyberTrust_Root.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/QuoVadis_Root_CA_1_G3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Trustis_FPS_Root_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/QuoVadis_Root_CA_3_G3.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Starfield_Root_Certificate_Authority_-_G2.pem: Cannot unlink: Read-only f
tar: etc/ssl/certs/Starfield_Services_Root_Certificate_Authority_-_G2.pem: Cannot unlink: Re
tar: etc/ssl/certs/CA_Disig_Root_R2.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Starfield_Class_2_CA.pem: Cannot unlink: Read-only file system
tar: etc/ssl/certs/Hongkong_Post_Root_CA_1.pem: Cannot unlink: Read-only file system
tar: etc/localtime: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01dbus: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01avahi-daemon: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01console-setup.sh: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01ssh: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01cron: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01haveged: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01sudo: Cannot unlink: Read-only file system
tar: etc/rc5.d/S01rsyslog: Cannot unlink: Read-only file system
tar: etc/alternatives/view.it.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/mpif90: Cannot unlink: Read-only file system
tar: etc/alternatives/cpp: Cannot unlink: Read-only file system
tar: etc/alternatives/rvim: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.fr.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/open: Cannot unlink: Read-only file system
tar: etc/alternatives/view.da.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/pico.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/vimdiff: Cannot unlink: Read-only file system
tar: etc/alternatives/cc: Cannot unlink: Read-only file system
tar: etc/alternatives/mpiCC: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.ru.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/lzgrep: Cannot unlink: Read-only file system
tar: etc/alternatives/builtins.7.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/view.fr.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.it.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/view.ru.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/editor.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/rmt: Cannot unlink: Read-only file system
tar: etc/alternatives/mpirun: Cannot unlink: Read-only file system
tar: etc/alternatives/lzegrep: Cannot unlink: Read-only file system
tar: etc/alternatives/rlogin: Cannot unlink: Read-only file system
tar: etc/alternatives/pager.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/editor: Cannot unlink: Read-only file system
tar: etc/alternatives/mt: Cannot unlink: Read-only file system
tar: etc/alternatives/pico: Cannot unlink: Read-only file system
tar: etc/alternatives/view.pl.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/lzdiff: Cannot unlink: Read-only file system
tar: etc/alternatives/mt.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/nawk.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/mpiexec: Cannot unlink: Read-only file system
tar: etc/alternatives/mpicxx: Cannot unlink: Read-only file system
tar: etc/alternatives/f77: Cannot unlink: Read-only file system
tar: etc/alternatives/nawk: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.de.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/awk: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.de.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/lzfgrep: Cannot unlink: Read-only file system
tar: etc/alternatives/lzless: Cannot unlink: Read-only file system
tar: etc/alternatives/ex: Cannot unlink: Read-only file system
tar: etc/alternatives/vim: Cannot unlink: Read-only file system
tar: etc/alternatives/lzcat: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/rmt.8.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/c89: Cannot unlink: Read-only file system
tar: etc/alternatives/c99: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.pl.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/view.ja.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/lzmore: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.da.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/lzcmp: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.ja.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/awk.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.ru.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/mpic++: Cannot unlink: Read-only file system
tar: etc/alternatives/vi.it.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/lzma: Cannot unlink: Read-only file system
tar: etc/alternatives/view: Cannot unlink: Read-only file system
tar: etc/alternatives/fonts-japanese-gothic.ttf: Cannot unlink: Read-only file system
tar: etc/alternatives/mpifort: Cannot unlink: Read-only file system
tar: etc/alternatives/rcp: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.fr.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/pager: Cannot unlink: Read-only file system
tar: etc/alternatives/mpif77: Cannot unlink: Read-only file system
tar: etc/alternatives/rview: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.da.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.pl.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/unlzma: Cannot unlink: Read-only file system
tar: etc/alternatives/view.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/f95: Cannot unlink: Read-only file system
tar: etc/alternatives/mpi: Cannot unlink: Read-only file system
tar: etc/alternatives/vi: Cannot unlink: Read-only file system
tar: etc/alternatives/view.de.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/ex.ja.1.gz: Cannot unlink: Read-only file system
tar: etc/alternatives/rsh: Cannot unlink: Read-only file system
tar: etc/xdg/systemd/user: Cannot unlink: Read-only file system
tar: dev/stdin: Cannot unlink: Read-only file system
tar: dev/stderr: Cannot unlink: Read-only file system
tar: dev/fd: Cannot unlink: Read-only file system
tar: dev/stdout: Cannot unlink: Read-only file system
tar: usr/bin: Cannot utime: Read-only file system
tar: usr/bin: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: usr/bin: Cannot change mode to rwxr-xr-x: Read-only file system
tar: usr: Cannot utime: Read-only file system
tar: usr: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: usr: Cannot change mode to rwxr-xr-x: Read-only file system
tar: root/temp/lib/modules/5.10.41: Cannot utime: Read-only file system
tar: root/temp/lib/modules/5.10.41: Cannot change ownership to uid 0, gid 0: Read-only file
tar: root/temp/lib/modules/5.10.41: Cannot change mode to rwxr-xr-x: Read-only file system
tar: root/temp/lib/modules: Cannot utime: Read-only file system
tar: root/temp/lib/modules: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: root/temp/lib/modules: Cannot change mode to rwxr-xr-x: Read-only file system
tar: root/temp/lib: Cannot utime: Read-only file system
tar: root/temp/lib: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: root/temp/lib: Cannot change mode to rwxr-xr-x: Read-only file system
tar: root/temp: Cannot utime: Read-only file system
tar: root/temp: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: root/temp: Cannot change mode to rwxr-xr-x: Read-only file system
tar: root: Cannot utime: Read-only file system
tar: root: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc2.d: Cannot utime: Read-only file system
tar: etc/rc2.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc2.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/runit/runsvdir/default: Cannot utime: Read-only file system
tar: etc/runit/runsvdir/default: Cannot change ownership to uid 0, gid 0: Read-only file sys
tar: etc/runit/runsvdir/default: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/runit/runsvdir: Cannot utime: Read-only file system
tar: etc/runit/runsvdir: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/runit/runsvdir: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/runit: Cannot utime: Read-only file system
tar: etc/runit: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/runit: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rc1.d: Cannot utime: Read-only file system
tar: etc/rc1.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc1.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/sysctl.d: Cannot utime: Read-only file system
tar: etc/sysctl.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/sysctl.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/sv/ssh/log: Cannot utime: Read-only file system
tar: etc/sv/ssh/log: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/sv/ssh/log: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/sv/ssh: Cannot utime: Read-only file system
tar: etc/sv/ssh: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/sv/ssh: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/sv: Cannot utime: Read-only file system
tar: etc/sv: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/sv: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rcS.d: Cannot utime: Read-only file system
tar: etc/rcS.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rcS.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rc3.d: Cannot utime: Read-only file system
tar: etc/rc3.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc3.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/dhcp/dhclient-enter-hooks.d: Cannot utime: Read-only file system
tar: etc/dhcp/dhclient-enter-hooks.d: Cannot change ownership to uid 0, gid 0: Read-only fil
tar: etc/dhcp/dhclient-enter-hooks.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/dhcp/dhclient-exit-hooks.d: Cannot utime: Read-only file system
tar: etc/dhcp/dhclient-exit-hooks.d: Cannot change ownership to uid 0, gid 0: Read-only file
tar: etc/dhcp/dhclient-exit-hooks.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/dhcp: Cannot utime: Read-only file system
tar: etc/dhcp: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/dhcp: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rc6.d: Cannot utime: Read-only file system
tar: etc/rc6.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc6.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rc4.d: Cannot utime: Read-only file system
tar: etc/rc4.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc4.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/systemd/system/getty.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/getty.target.wants: Cannot change ownership to uid 0, gid 0: Read-on
tar: etc/systemd/system/getty.target.wants: Cannot change mode to rwxr-xr-x: Read-only file
tar: etc/systemd/system/sysinit.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/sysinit.target.wants: Cannot change ownership to uid 0, gid 0: Read-
tar: etc/systemd/system/sysinit.target.wants: Cannot change mode to rwxr-xr-x: Read-only fil
tar: etc/systemd/system/sockets.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/sockets.target.wants: Cannot change ownership to uid 0, gid 0: Read-
tar: etc/systemd/system/sockets.target.wants: Cannot change mode to rwxr-xr-x: Read-only fil
tar: etc/systemd/system/timers.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/timers.target.wants: Cannot change ownership to uid 0, gid 0: Read-o
tar: etc/systemd/system/timers.target.wants: Cannot change mode to rwxr-xr-x: Read-only file
tar: etc/systemd/system/multi-user.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/multi-user.target.wants: Cannot change ownership to uid 0, gid 0: Re
tar: etc/systemd/system/multi-user.target.wants: Cannot change mode to rwxr-xr-x: Read-only
tar: etc/systemd/system/network-online.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/network-online.target.wants: Cannot change ownership to uid 0, gid 0
tar: etc/systemd/system/network-online.target.wants: Cannot change mode to rwxr-xr-x: Read-o
tar: etc/systemd/system/default.target.wants: Cannot utime: Read-only file system
tar: etc/systemd/system/default.target.wants: Cannot change ownership to uid 0, gid 0: Read-
tar: etc/systemd/system/default.target.wants: Cannot change mode to rwxr-xr-x: Read-only fil
tar: etc/systemd/system: Cannot utime: Read-only file system
tar: etc/systemd/system: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/systemd/system: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/systemd: Cannot utime: Read-only file system
tar: etc/systemd: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/systemd: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rc0.d: Cannot utime: Read-only file system
tar: etc/rc0.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc0.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/modules-load.d: Cannot utime: Read-only file system
tar: etc/modules-load.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/modules-load.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/fonts/conf.d: Cannot utime: Read-only file system
tar: etc/fonts/conf.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/fonts/conf.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/fonts: Cannot utime: Read-only file system
tar: etc/fonts: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/fonts: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/ssl/certs: Cannot utime: Read-only file system
tar: etc/ssl/certs: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/ssl/certs: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/ssl: Cannot utime: Read-only file system
tar: etc/ssl: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/ssl: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/rc5.d: Cannot utime: Read-only file system
tar: etc/rc5.d: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/rc5.d: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/alternatives: Cannot utime: Read-only file system
tar: etc/alternatives: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/alternatives: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/xdg/systemd: Cannot utime: Read-only file system
tar: etc/xdg/systemd: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/xdg/systemd: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc/xdg: Cannot utime: Read-only file system
tar: etc/xdg: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc/xdg: Cannot change mode to rwxr-xr-x: Read-only file system
tar: etc: Cannot utime: Read-only file system
tar: etc: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: etc: Cannot change mode to rwxr-xr-x: Read-only file system
tar: dev: Cannot utime: Read-only file system
tar: dev: Cannot change ownership to uid 0, gid 0: Read-only file system
tar: dev: Cannot change models
bin opt
boot proc
dev root
etc run
home sbin
initrd.img skeliosv4_arm64_bcs_openamp_uc3sample_addpkg_221025.tar.gz
initrd.img.old srv
lib sys
media tmp
mnt usr
.....
root@MFP13560775:/mnt/sdc2> mount
/dev/ram1 on /old_root type ext4 (rw,relatime)
/dev/sda2 on / type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
/dev/sda13 on /platform type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
devtmpfs on /dev type devtmpfs (rw,relatime,size=1906228k,nr_inodes=476557,mode=755)
tmpfs on /run type tmpfs (rw,relatime)
sysfs on /sys type sysfs (rw,relatime)
tmpfs on /sys/fs/cgroup type tmpfs (ro,nosuid,nodev,noexec,mode=755)
cgroup on /sys/fs/cgroup/memsys type cgroup (rw,relatime,cpu,cpuacct,memory)
proc on /proc type proc (rw,nosuid,nodev,noexec,relatime)
securityfs on /sys/kernel/security type securityfs (rw,nosuid,nodev,noexec,relatime)
tmpfs on /dev/shm type tmpfs (rw,nosuid,nodev)
devpts on /dev/pts type devpts (rw,nosuid,noexec,relatime,gid=5,mode=620,ptmxmode=000)
tmpfs on /run/lock type tmpfs (rw,nosuid,nodev,noexec,relatime,size=5120k)
cgroup on /sys/fs/cgroup/systemd type cgroup (rw,nosuid,nodev,noexec,relatime,xattr,release_
cgroup on /sys/fs/cgroup/cpuset type cgroup (rw,nosuid,nodev,noexec,relatime,cpuset)
cgroup on /sys/fs/cgroup/blkio type cgroup (rw,nosuid,nodev,noexec,relatime,blkio)
cgroup on /sys/fs/cgroup/devices type cgroup (rw,nosuid,nodev,noexec,relatime,devices)
cgroup on /sys/fs/cgroup/freezer type cgroup (rw,nosuid,nodev,noexec,relatime,freezer)
cgroup on /sys/fs/cgroup/perf_event type cgroup (rw,nosuid,nodev,noexec,relatime,perf_event)
cgroup on /sys/fs/cgroup/pids type cgroup (rw,nosuid,nodev,noexec,relatime,pids)
mqueue on /dev/mqueue type mqueue (rw,relatime)
debugfs on /sys/kernel/debug type debugfs (rw,relatime)
fusectl on /sys/fs/fuse/connections type fusectl (rw,relatime)
/dev/sda3 on /rollback type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
ramfs on /ramdisk type ramfs (rw,relatime,size=100m)
/dev/sda5 on /work type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
/dev/sda6 on /registration type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
/dev/sda7 on /backup type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
/dev/sda8 on /imagedata type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
/dev/sdb9 on /application type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
/dev/mapper/enc_encryption on /encryption type ext4 (rw,relatime,nodelalloc,nobarrier,data=o
/dev/sdb12 on /storage type ext4 (rw,relatime,nodelalloc,nobarrier,data=ordered)
tmpfs on /run/user/0 type tmpfs (rw,nosuid,nodev,relatime,size=381936k,mode=700)
configfs on /sys/kernel/config type configfs (rw,relatime)
/dev/sdc1 on /platform/mnt/sdc1 type vfat (rw,relatime,gid=2000,fmask=0000,dmask=0000,allow_unt-ro)
/dev/sdc2 on /platform/mnt/sdc2 type ext4 (ro,relatime,data=ordered)
root@MFP13560775:/mnt> df -hT
Filesystem Type Size Used Avail Use% Mounted on
/dev/root ext4 46M 34M 11M 77% /old_root
/dev/sda2 ext4 6.2G 4.8G 1.1G 83% /
/dev/sda13 ext4 4.7G 82M 4.4G 2% /platform
devtmpfs devtmpfs 1.9G 4.0K 1.9G 1% /dev
tmpfs tmpfs 1.9G 17M 1.9G 1% /run
tmpfs tmpfs 1.9G 0 1.9G 0% /sys/fs/cgroup
tmpfs tmpfs 1.9G 29M 1.8G 2% /dev/shm
tmpfs tmpfs 5.0M 0 5.0M 0% /run/lock
/dev/sda3 ext4 6.2G 1.6G 4.3G 27% /rollback
/dev/sda5 ext4 14G 1.1G 13G 8% /work
/dev/sda6 ext4 2.8G 852M 1.8G 32% /registration
/dev/sda7 ext4 949M 1.3M 883M 1% /backup
/dev/sda8 ext4 19G 59M 18G 1% /imagedata
/dev/sdb9 ext4 94G 75M 89G 1% /application
/dev/mapper/enc_encryption ext4 964M 2.8M 935M 1% /encryption
/dev/sdb12 ext4 295G 64M 280G 1% /storage
tmpfs tmpfs 373M 0 373M 0% /run/user/0
/dev/sdc1 vfat 133M 3.4M 130M 3% /platform/mnt/sdc1
/dev/sdc2 ext4 2.1G 517M 1.5G 27% /platform/mnt/sdc2
root@MFP13560775:/mnt> lsblk -f
NAME FSTYPE LABEL UUID MOUNTPOINT
sda
|-sda1
|-sda2 ext4 0d1fb479-c0fe-47fe-b41d-1733c81e3a10 /
|-sda3 ext4 f93b466f-10b7-49ac-9649-111275fac2ee /rollback
|-sda4
|-sda5 ext4 bff71b85-a054-4404-b2ad-0e3c0314b0ec /work
|-sda6 ext4 446a6fc3-7947-4186-b78a-e97477a15861 /registration
|-sda7 ext4 43b850bb-80e4-4b71-b84a-d01856f10ca2 /backup
|-sda8 ext4 ae960403-ad80-4e50-b7a2-a4fedc3bceb5 /imagedata
|-sda9 ext4 9b9428c1-6537-4e9b-8ebd-e2e2d6d83eaf
|-sda10 crypto_LU 1f39264b-e4c7-4c0f-85dd-126df3669a35
| `-enc_encryption
ext4 9adfdf32-ba21-4132-9eda-559546b6acca /encryption
|-sda11 swap 6ecd166b-a5aa-43d2-b027-3ca2beb62d78 [SWAP]
|-sda12 ext4 20f918f8-618b-4c4b-9c27-33ea3672a339
`-sda13 ext4 dbbefca6-c893-4cc7-9d78-396bcb8e79cd /platform
sdb
|-sdb1
|-sdb2 ext4 da6ee4a8-bb4f-40bf-8b39-49be82f0b70e
|-sdb3 ext4 325fadf7-e2eb-4547-b9a5-8815803493c2
|-sdb4
|-sdb5 ext4 100a5a81-6ee3-4ecb-bbbc-f59e2bce96cd
|-sdb6 ext4 3d456b2f-c884-4cb3-8c55-80066a8363d6
|-sdb7 ext4 c1b19099-0e08-43d8-80bd-00e0c3d56bb8
|-sdb8 ext4 adfdd347-f7d8-4ced-850a-d81607d9a607
|-sdb9 ext4 68da55a3-8cd3-4ef3-9525-80670674fe4e /application
|-sdb10 ext4 5da8627f-e6d4-4d4a-8aa2-d508fb6780ab
|-sdb11 swap 789b5724-f2f9-447f-a5aa-363ae4de13c8
|-sdb12 ext4 8b1b3400-0a27-4ae1-8a50-03f9e192577e /storage
`-sdb13 ext4 a1e23551-7cdd-4f8c-8dff-b3b77ab4a876
sdc
|-sdc1 /platform/mnt/sdc
`-sdc2 /platform/mnt/sdc
root@MFP13560775:/mnt> ls -lrt
total 24
drwxrwxrwx 4 root trusted 16384 Dec 31 1969 sdc1
drwxrwxrwx 3 root trusted 4096 Apr 25 18:45 hdd
drwxr-xr-x 16 root root 4096 Apr 26 12:09 sdc2
root@MFP13560775:/mnt>
----Thanks, Ajith K.
Hi Ajith,
I have attached below the boot partition binaries. Hope it helps!
Regards,
Prashant
Here is the Logs on the COM(COM5) window of the Board:
U-Boot SPL 2021.01-g3983bffabc (Dec 14 2022 - 11:55:03 +0000)
Resetting on cold boot to workaround ErrataID:i2331
resetting ...
U-Boot SPL 2021.01-g3983bffabc (Dec 14 2022 - 11:55:03 +0000)
SYSFW ABI: 3.1 (firmware rev 0x0008 '8.5.3--v08.05.03 (Chill Capybar')
SPL initial stack usage: 13424 bytes
Trying to boot from MMC2
Warning: Detected image signing certificate on GP device. Skipping certificate to prevent boot failure. This will fail if the image was also encrypted
Warning: Detected image signing certificate on GP device. Skipping certificate to prevent boot failure. This will fail if the image was also encrypted
Warning: Detected image signing certificate on GP device. Skipping certificate to prevent boot failure. This will fail if the image was also encrypted
Warning: Detected image signing certificate on GP device. Skipping certificate to prevent boot failure. This will fail if the image was also encrypted
Starting ATF on ARM64 core...
NOTICE: BL31: v2.7(release):v2.7.0-359-g1309c6c805-dirty
NOTICE: BL31: Built : 11:49:05, Dec 14 2022
I/TC:
I/TC: OP-TEE version: 3.19.0-15-gd6c5d0037 (gcc version 9.2.1 20191025 (GNU Toolchain for the A-profile Architecture 9.2-2019.12 (arm-9.10))) #1 Wed Dec 14 11:53:26 UTC 2022 aarch64
I/TC: WARNING: This OP-TEE configuration might be insecure!
I/TC: WARNING: Please check optee.readthedocs.io/.../porting_guidelines.html
I/TC: Primary CPU initializing
I/TC: SYSFW ABI: 3.1 (firmware rev 0x0008 '8.5.3--v08.05.03 (Chill Capybar')
I/TC: HUK Initialized
I/TC: Activated SA2UL device
I/TC: Fixing SA2UL firewall owner for GP device
I/TC: Enabled firewalls for SA2UL TRNG device
I/TC: SA2UL TRNG initialized
I/TC: SA2UL Drivers initialized
I/TC: Primary CPU switching to normal world boot
U-Boot SPL 2021.01-g3983bffabc (Dec 14 2022 - 11:53:57 +0000)
SYSFW ABI: 3.1 (firmware rev 0x0008 '8.5.3--v08.05.03 (Chill Capybar')
Trying to boot from MMC2
Warning: Detected image signing certificate on GP device. Skipping certificate to prevent boot failure. This will fail if the image was also encrypted
Warning: Detected image signing certificate on GP device. Skipping certificate to prevent boot failure. This will fail if the image was also encrypted
U-Boot 2021.01-g3983bffabc (Dec 14 2022 - 11:53:57 +0000)
SoC: AM64X SR1.0 GP
Model: Texas Instruments AM642 EVM
Board: AM64-GPEVM rev B
DRAM: 2 GiB
NAND: 0 MiB
MMC: mmc@fa10000: 0, mmc@fa00000: 1
Loading Environment from FAT... *** Warning - bad CRC, using default environment
In: serial@2800000
Out: serial@2800000
Err: serial@2800000
Net: eth0: ethernet@8000000port@1
Hit any key to stop autoboot: 0
switch to partitions #0, OK
mmc1 is current device
SD/MMC found on device 1
Failed to load 'boot.scr'
1490 bytes read in 2 ms (727.5 KiB/s)
Loaded env from uEnv.txt
Importing environment from mmc1 ...
Running uenvcmd ...
1 bytes read in 3 ms (0 Bytes/s)
Already setup.
Failed to load '/boot/Image'
Failed to load '/boot/k3-am642-evm.dtb'
libfdt fdt_check_header(): FDT_ERR_BADMAGIC
No FDT memory address configured. Please configure
the FDT address via "fdt addr <address>" command.
Aborting!
Bad Linux ARM64 Image magic!
=>
Hi Ajith,
Glad to know the shared images are working. Next, I see from the logs you already are getting the U-Boot prompt. I believe what you want is the Linux shell prompt. If so, this shell prompt you will get when the root partition of the SD card contains a valid filesystem.
Regarding this, do you have your own custom filesystem that you want to boot? I see you are trying to extract some tar file named skeliosv3_armhf_seriallogin_210413.tar.xz. Is this your custom filesystem?
Regards,
Prashant
Hi Prashant,
Yes, we do have our own custom file system: skeliosv4_arm64_bcs_openamp_uc3sample_addpkg_221025.tar.gz.
However, while mounting the root partition we are experiencing some error; at times mount error or tar extraction fails. When I had checked the size of the disk, it has got enough memory space to hold the extracted Linux file system.
Please find the last error logs again below:
root@MFP13560775:/> sudo cp BOOT/uEnv.txt /mnt
root@MFP13560775:/> sudo cp BOOT/tiboot3.bin /mnt
root@MFP13560775:/> sudo cp BOOT/tispl.bin /mnt
root@MFP13560775:/> sudo cp BOOT/u-boot.img /mnt
root@MFP13560775:/> sudo cp BOOT/BCP_RTOS.bin /mnt
root@MFP13560775:/> sudo umount /mnt
root@MFP13560775:/>
root@MFP13560775:/>
root@MFP13560775:/> sudo mousdc: Retry Count 2 (Max 5)
2023 Apr 27 14:26:30 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:26:30 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:26:30 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:26:30 MFP13560775 sdc: Retry Count 2 (Max 5)
nt /dev/sdc2 /mnt
sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:27:32 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:27:32 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:27:32 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:27:32 MFP13560775 sdc: Retry Count 4 (Max 5)
sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:29:36 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:29:36 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:29:36 MFP13560775 sdc: Retry Count 2 (Max 5)
2023 Apr 27 14:29:36 MFP13560775 sdc: Retry Count 2 (Max 5)
sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:30:38 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:30:38 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:30:38 MFP13560775 sdc: Retry Count 4 (Max 5)
2023 Apr 27 14:30:38 MFP13560775 sdc: Retry Count 4 (Max 5)
mount: /dev/sdc2: can't read superblock
root@MFP13560775:/>
Kindly share your thoughts what could be causing this?
--Thanks, Ajith K