There are default ID values for the ID registers of USB, PCIe, MAC as listed in the TRM:
- PCIe
CTRLMMR_PCI_DEVICE_ID0, CTRLMMR_PCI_DEVICE_ID1
- USB
CTRLMMR_USB_DEVICE_ID0, CTRLMMR_USB_DEVICE_ID1
- MAC
CTRLMMR_MAC_ID0, CTRLMMR_MAC_ID1
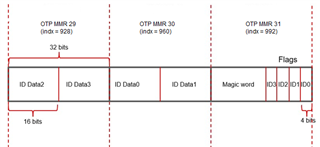
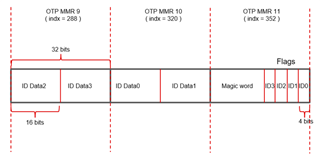
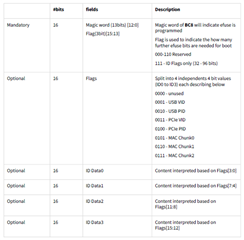
The default ID values can be optionally updated by programming the extended OTP efuse. If the ID update magic word is programmed by user and found from the extended OTP area by ROM then ROM process and update the ID register values with the programed ID values from the extended OTP area.
The FAQ describes how to update the default IDs (USB & PCIe PID/VID, MAC ID) by programming extended OTP efuse.The ID value update by programming the extended OTP area is supported by either OTP keywriter or SYSFW. The test in the FAQ is using SYSFW on AM62A SoC HS-FS, and this would work on HS-SE. The same feature is also supported on AM64x, AM62x.
It is recommended to read this related FAQ first on "How to program the extended OTP efuse on AM6x SoC"
https://e2e.ti.com/support/processors-group/processors/f/processors-forum/1235859/faq-how-to-program-the-extended-otp-efuse-on-am6x-soc