Hi,
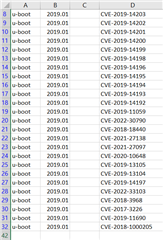
I scanned Uboot image built with below SDK
ti-processor-sdk-linux-am437x-hs-evm-06.03.00.106/board-support/u-boot-2019.01+gitAUTOINC+333c3e72d3-g333c3e72d3 and found below CVEs .-let me know if we can have call to define the mitigation plan
This thread has been locked.
If you have a related question, please click the "Ask a related question" button in the top right corner. The newly created question will be automatically linked to this question.
Hi,
I scanned Uboot image built with below SDK
ti-processor-sdk-linux-am437x-hs-evm-06.03.00.106/board-support/u-boot-2019.01+gitAUTOINC+333c3e72d3-g333c3e72d3 and found below CVEs .-let me know if we can have call to define the mitigation plan

we can have call on this Topic if you need to go through U-boot CVEs and ofcourse we must will have CVEs for Kernel as well.
I am surprised to see why TI still uses as Old version of U-boot and kernel as secure TI_SDK(latest)
The TI SDK release is always to migrate to latest LTS model . (As you might be aware there is a LTS version for kernel , not specifically for Uboot)
1. On TI Release cadence:
* The last released AM4 based SDK was based on 5.10 kernel and 2021.01 uboot
On "I am surprised to see why TI still uses as Old version of U-boot and kernel as secure TI_SDK(latest)" >> You are not looking at the last made release in 2022.
* We are currently in middle of migration to 6.1 LTS and 2023.04 Uboot
A Initial CICD snapshot is available here https://software-dl.ti.com/cicd-report/linux/index.html?section=snapshot&platform=am437x&snapshot=cicd.kirkstone.202309061800
2. On Choosing Uboot version for TI SDK
* Uboot in mainline gets tagged approx once in 3 months : https://u-boot.readthedocs.io/en/latest/develop/release_cycle.html
* TI chooses a version of uboot carefully around a x.0 timeframe that matches the LTS kernel release window.
* For the current year that is 6.1.y Kernel and 2023.04 Uboot
3. On CVE Handling:
Ref: https://u-boot.readthedocs.io/en/latest/develop/security.html# Is the guideline for Uboot community for handling CVEs.
Ref: https://www.kernel.org/doc/html/v6.1/admin-guide/security-bugs.html Is the guideline for Kernel community for handling CVEs
In Summary: CVEs are handles by respective mainline project and the mentioned CVE guideline above.
The mentioned latest TI-SDK ->
Ref: https://software-dl.ti.com/processor-sdk-linux/esd/AM437X/08_02_00_24/exports/docs/devices/AM437X/linux/Release_Specific_Release_Notes.html is this one part of Secure SDK as you have a separate secure TI-SDK -ti-processor-sdk-linux-am437x-hs-evm-06.03.00.106 had U-boot and Kernel are not on latest SDK, do you have any plan to move on Latest Version.
2- what are difference bw these two SDK?
Hello Raju,
1/. AM43xx GP (public access)
software-dl.ti.com/.../Release_Specific_Release_Notes.html
2/. AM43xx HS (controlled access)
software-dl.ti.com/.../index_FDS.html
a/. u-boot/kernel
b/. SecDev package: security package for secure boot enablement including secure PPA + reference IFT signing tool
It is feasible for customer to use u-boot/kernel SRC, i.e. from 1/ + the security package from 2b/.
There's active work to enable AM43xx SDK 9.x as noted by Praneeth.
"We are currently in middle of migration to 6.1 LTS and 2023.04 Uboot"
Best,
-Hong
I see there are lots of CVEs generated for this version of Kernel -4.14 as well except the U-boot(mentioned). again can you please share the SDK which have minimum CVEs-latest Version of Code base.
can you please share the SDK which have minimum CVEs-latest Version of Code base.
2. On Choosing Uboot version for TI SDK
* Uboot in mainline gets tagged approx once in 3 months : https://u-boot.readthedocs.io/en/latest/develop/release_cycle.html
* TI chooses a version of uboot carefully around a x.0 timeframe that matches the LTS kernel release window.
* For the current year that is 6.1.y Kernel and 2023.04 Uboot
3. On CVE Handling:
Ref: https://u-boot.readthedocs.io/en/latest/develop/security.html# Is the guideline for Uboot community for handling CVEs.
Ref: https://www.kernel.org/doc/html/v6.1/admin-guide/security-bugs.html Is the guideline for Kernel community for handling CVEs
In Summary: CVEs are handles by respective mainline project and the mentioned CVE guideline above.
Best,
-Hong