Hello E2E-Experts,
I have a full-custom board with a DRA829JMT0BALFQ1 (HS-FS device).
I received the following information via WKUP_UART, decoded by the parse_uart_boot_socid.py script:
-----------------------SoC ID Header Info:-----------------------NumBlocks : 2-----------------------SoC ID Public ROM Info:-----------------------SubBlockId : 1SubBlockSize : 26DeviceName : j7esDeviceType : HSFSDMSC ROM Version : [0, 1, 1, 1]R5 ROM Version : [0, 1, 1, 1]-----------------------SoC ID Secure ROM Info:-----------------------Sec SubBlockId : 2Sec SubBlockSize : 166Sec Prime : 0Sec Key Revision : 0Sec Key Count : 0Sec TI MPK Hash : aa1f8e3095042e5c71ac40ede5b4e8c85fa87e03305ae0ea4f47933e89f4164aeb5a12ae13778f49de0622c1a578e6e747981d8c44a130f89a336a887a7955eeSec Cust MPK Hash : ad0bc40b000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000Sec Unique ID : 0fa0ca248c54e3c5f93331335d4d9b15bf7f6291433618f449ee03d4bc390de5
This is my working environment:
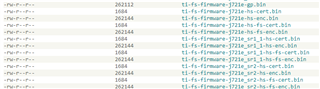
export SDK_DIR=/opt/ti-processor-sdk-linux-j7-evm-08_06_00_11export TI_SECURE_DEV_PKG=$SDK_DIR/board-support/core-secdev-k3
cd $SDK_DIR/board-support/k3-image-gen-2022.01
$ make SOC=j721e_sr2 SOC_TYPE=hs-fs SYSFW_DIR=../prebuilt-images
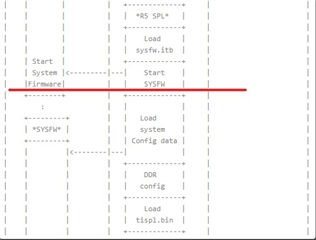
This is my current state of booting:
- R5 SPL (U-Boot/tiboot3.bin) loaded by R5 ROM and executed successully
- tested via USB DFU and UART
- tested via USB DFU and UART
- R5 SPL loads SYSFW (sysfw.itb)
- R5 SPL tries to start SYSFW on DMSC and hangs

By debugging, I could locate the issue a bit more specific:
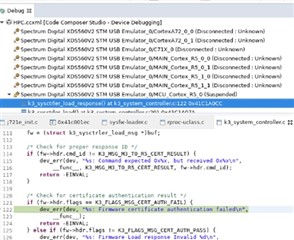
SYSFW takes the path via "Firmware certificate authentication failed".
I generated and signed SYSFW as described.
Hello? (Hello? Hello? Hello?)Is there anybody in there?...
I'll need some information first
Just the basic factsCan you show me where it hurts?
Do I need a dedicated SYSFW for DRA829JMT0BALFQ1 HS-FS? Any other requirements I my have missed?
Best regards
Wolfram Stumpf