Other Parts Discussed in Thread: DRA829
Hello experts,
We have recently received variants of our custom board equipped with HS SoC:s.
Can you please point me in the right direction on how to proceed with OTP programming
(public key, vid:pid, serial number etc), and how to build the correct files needed for
a secure boot.
This is mainly for factory, but we want to try it out on a key-pair of our own, before we
send away files to be signed.
What we want to achieve:
- Burn public key, vid:pid and serial# to OTP
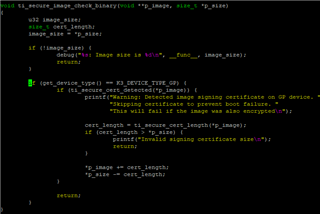
- On boot, validate the boot files (tiboot3.bin, sysfw, tispl.bin, u-boot.img) that have been
signed with the private key - From U-Boot and onwards we will use another key-pair to secure kernel and dtb:s.
We are using yocto to build. Current versions are U-Boot 2023.04, Linux 6.1.69.
In my deploy-folder, I have the following binaries:
-rw-r--r-- 2 bomellberg bomellberg 268978 Jan 31 14:45 sysfw-j721e-gp-evm.itb-rw-r--r-- 2 bomellberg bomellberg 278254 Jan 31 14:45 sysfw-j721e_sr1_1-hs-evm.itb-rw-r--r-- 2 bomellberg bomellberg 269718 Jan 31 14:45 sysfw-j721e_sr2-hs-fs-evm.itb
-rw-r--r-- 2 bomellberg bomellberg 273257 Jan 31 14:45 tiboot3-j721e-gp-evm.bin-rw-r--r-- 2 bomellberg bomellberg 274031 Jan 31 14:45 tiboot3-j721e_sr1_1-hs-evm.bin-rw-r--r-- 2 bomellberg bomellberg 274032 Jan 31 14:45 tiboot3-j721e_sr2-hs-fs-evm.bin
-rw-r--r-- 2 bomellberg bomellberg 1021907 Jan 31 14:46 tispl.bin-asp3-2023.04+git999-r0
-rw-r--r-- 2 bomellberg bomellberg 1328683 Jan 31 14:46 u-boot-asp3-2023.04+git999-r0.img
My binman-file has these relevant file references:
keyfile = "custMpk.pem"filename = "ti-sysfw/ti-fs-firmware-j721e_sr1_1-hs-cert.bin"filename = "ti-sysfw/ti-fs-firmware-j721e_sr1_1-hs-enc.bin"filename = "ti-sysfw/ti-fs-firmware-j721e_sr2-hs-fs-cert.bin"filename = "ti-sysfw/ti-fs-firmware-j721e_sr2-hs-fs-enc.bin"
difficult to understand how to get it all working.