Part Number: DRA821U
Other Parts Discussed in Thread: DRA821,
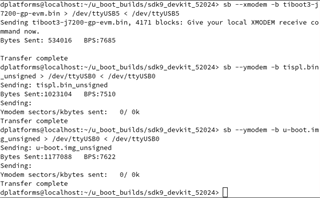
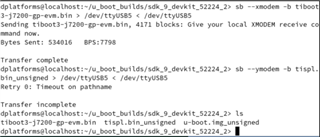
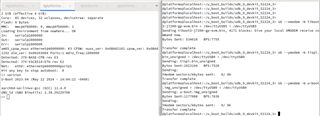
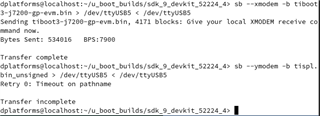
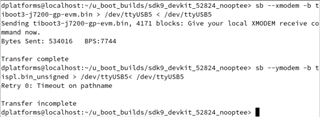
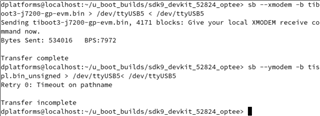
We have custom hardware using DRA821 which is currently pre-production DRA821. We modified SDK 9.02 k3-j7200* device tree files to account for our configuration did a build which completed normally. The files we are using are:
tiboot3-j7200-gp-evm.bin for tiboot3.bin
tispl.bin_unsigned for tispl.bin
u-boot.img_unsigned for u-boot.img
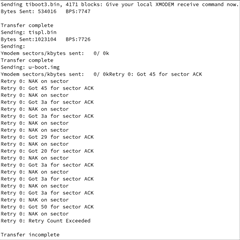
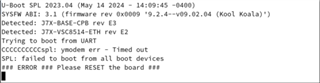
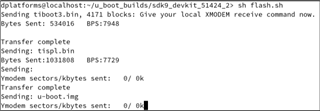
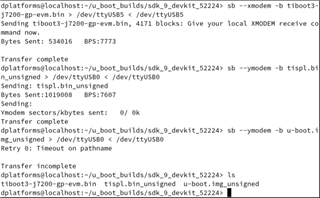
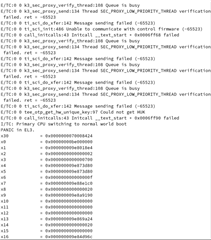
When we try to boot we get the attached screen capture. We are trying to boot the board via UART. Our custom board only has WKUP_UART. Not sure what this sec_proxy error is about. We only see this when trying to boot an unsigned image onto our custom hardware. There are no changes in how sec_proxy is defined in the device tree or the config files so could it be a driver difference or something with the new security code?

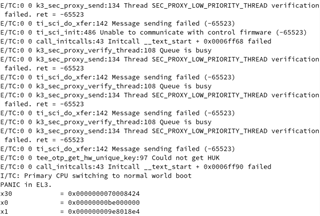
What is going wrong?