Hello,
I'm using the j784s4-evm-09_01_00_06 rtos sdk for development.
It is my understanding that the x509CertificateGen.sh script in this sdk is used for signing.
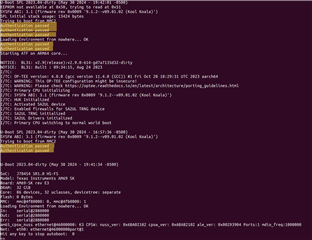
My current goal is to sign tispl.bin, tiboot3.bin & u-boot.img with TI provided keys and then see 'Authentication Passed' messages when booting the board.
I would like to repeat this process with my own generated keys.
I have used the script to generate these signed binaries with both sets of keys but they do not pass authentication.
Requesting detailed steps for generating these signed binaries using the Certificate gen script.
If this is not the correct method for signing, please let me know.