Tool/software:
Hello All,
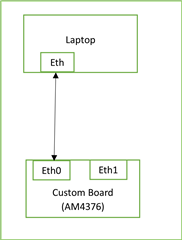
We are using AM4376 processor for one of our product development. We are using processor SDK 8.02 with RT Linux version . we have developed the application with out custom board and found issue of ping losses while pinging the device from the laptop.
Initially we thought that it is due to our application of Bridge STP which we are using currently in our application, Although testing is still going on. But When we simply load u-boot, MLO , kernel and file system and then after booting the system we got the command prompt.
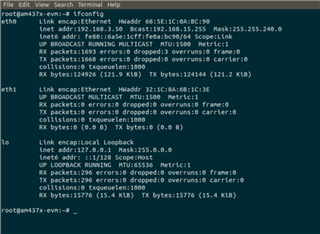
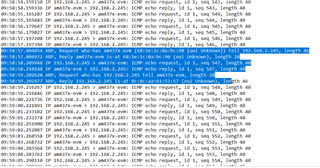
Then we assigned IP address to eth0 port. Not we are not running application, so there is no bridge right now. then while pinging we found ping timeout and ARP malformed packet . what could be the reason for the same?
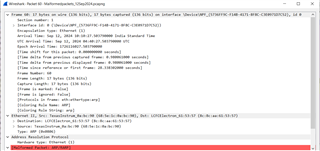
I have attached the logs for reference. due to this issue our production level testing is halted. So please consider this as a higher priority.
unzip the file and check for the Wireshark capture for the malformed packets. Also find the kernel configuration file used for our development.
. tisdk_am437x-evm-rt_defconfig.zip
this is on very high priority.. Please provide inputs regarding the same. This issue has stopped our final testing as well.
Thanks
Gaurav More