Other Parts Discussed in Thread: AM5728
Tool/software:
Hi ,
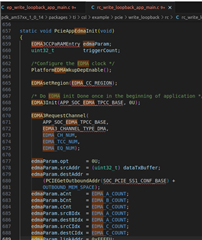
We are transferring data between in AM5748 (RC) and xilinx FPGA (EP) via PCIe port , so after the enumeration the address space is getting detected , Region 0: Memory at 20400000 (32-bit, non-prefetchable) [disabled] [size=4M] , so if I write data of 64 byte of uint32_t type buffer to this address space on the End point the on ILA we are seeing data as shown below.

Here the upper 32 bit is address and lower 32 bit is the data that we are sending and if we see the packet header we can see F4000001 the last digit is 1 so the DWORD length of the packet is 1 so , my question is how to increase the length of the DWORD , I was not able to find any register for this configuration on the ARM side so please provide us with some pointers regarding how to set the DWORD length on the TLP header to 2 from 1(default).
Thanks,
Phaneesh A Kashyap