Other Parts Discussed in Thread: TDA4VM, MATHLIB
Tool/software:
I’m encountering a problem where the Keywriter hangs.
It does not seem to be related to any function in the keywriter main.c, since it hangs after a seemingly constant amount of time even if I just do a loop with printf().
My suspicion is that a watchdog is interfering with it, but I cannot find any explicit activation of the TDA4VM RTI watchdog, and the PMIC watchdog has a default 13 minute timeout.
I’ve measured the power supplies and reset signals, all seem to stay in nominal operating state when the board hangs.
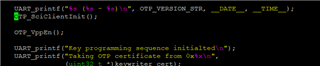
UART output:
OTP Keywriter Version: 02.00.00.00 (Oct 30 2024 - 09:13:39)
SW ver:
Linux 8.1.0.7
RTOS 8.1.0.13
PDK 8.1.0.36
OTP_KEYWRITER_ADD_ON_j721e_sr1_1_v2021.05b