Tool/software:
Hi, TI expert!
I have a development environment for am6234, with our own evaluation board.
The software SDK version is PROCESSOR-SDK-LINUX-RT-AM62X-08.06.00.42.
optee version is 3.20.0
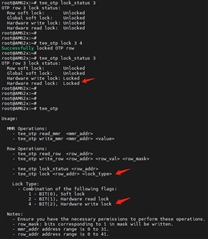
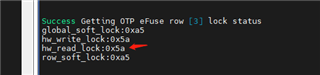
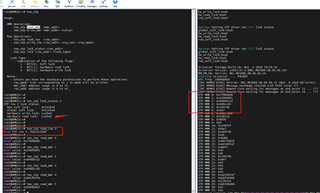
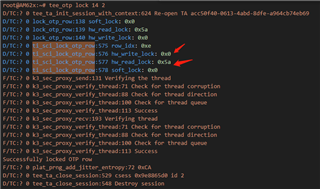
I only want to execute hw_read_lock on extend otp rows, but in actual testing, not only is the row read locked, but the row write is also locked, as shown below:
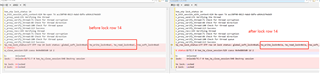
1.Log of locking external otp row
2.Locking status of external OTP rows:
The corresponding test code is as follows:
// ti-processor-sdk-linux-rt-am62xx-evm-08.06.00.42\board-support\optee_os-3.20.0\core\pta\k3\otp.c
static TEE_Result lock_otp_row(uint32_t param_types, TEE_Param params[4])
{
TEE_Result ret = TEE_SUCCESS;
uint8_t hw_write_lock = 0;
uint8_t hw_read_lock = 0;
uint8_t soft_lock = 0;
const uint32_t exp_param_types =
TEE_PARAM_TYPES(TEE_PARAM_TYPE_VALUE_INPUT, TEE_PARAM_TYPE_NONE,
TEE_PARAM_TYPE_NONE, TEE_PARAM_TYPE_NONE);
/*
* Safely get the invocation parameters
*/
if (param_types != exp_param_types)
return TEE_ERROR_BAD_PARAMETERS;
if (params[0].value.b & K3_OTP_KEYWRITING_SOFT_LOCK)
soft_lock = 0x5A;
if (params[0].value.b & K3_OTP_KEYWRITING_HW_READ_LOCK)
hw_read_lock = 0x5A;
if (params[0].value.b & K3_OTP_KEYWRITING_HW_WRITE_LOCK)
hw_write_lock = 0x5A;
DMSG("hw_write_lock: 0x%x", hw_write_lock);
DMSG("hw_read_lock: 0x%x", hw_read_lock);
DMSG("soft_lock: 0x%x", soft_lock);
ret = ti_sci_lock_otp_row(params[0].value.a, hw_write_lock,
hw_read_lock, soft_lock);
if (ret)
return ret;
DMSG("Locked the row: 0x%08"PRIx32, params[1].value.a);
return TEE_SUCCESS;
}
static TEE_Result get_otp_row_lock_status(uint32_t param_types, TEE_Param params[4])
{
TEE_Result ret = TEE_SUCCESS;
uint8_t global_soft_lock, hw_write_lock, hw_read_lock, row_soft_lock;
const uint32_t exp_param_types =
TEE_PARAM_TYPES(TEE_PARAM_TYPE_VALUE_INPUT, TEE_PARAM_TYPE_VALUE_OUTPUT,
TEE_PARAM_TYPE_VALUE_OUTPUT, TEE_PARAM_TYPE_VALUE_OUTPUT);
/*
* Safely get the invocation parameters
*/
if (param_types != exp_param_types)
return TEE_ERROR_BAD_PARAMETERS;
ret = ti_sci_get_otp_row_lock_status(params[0].value.a, &global_soft_lock,
&hw_write_lock, &hw_read_lock, &row_soft_lock);
if (ret)
return ret;
params[1].value.a = global_soft_lock;
params[2].value.a = hw_write_lock;
params[3].value.a = hw_read_lock;
params[3].value.b = row_soft_lock;
DMSG("OTP row %u lock status: global_soft_lock=0x%02x, hw_write_lock=0x%02x, hw_read_lock=0x%02x, row_soft_lock=0x%02x",
params[0].value.a, global_soft_lock, hw_write_lock, hw_read_lock, row_soft_lock);
return TEE_SUCCESS;
}
// ti-processor-sdk-linux-rt-am62xx-evm-08.06.00.42\board-support\optee_os-3.20.0\core\arch\arm\plat-k3\drivers\ti_sci.c
int ti_sci_lock_otp_row(uint8_t row_idx, uint8_t hw_write_lock,
uint8_t hw_read_lock, uint8_t row_soft_lock)
{
struct ti_sci_msg_req_lock_otp_row req = { };
struct ti_sci_msg_resp_lock_otp_row resp = { };
struct ti_sci_xfer xfer = { };
int ret = 0;
ret = ti_sci_setup_xfer(TI_SCI_MSG_LOCK_OTP_ROW, 0,
&req, sizeof(req), &resp, sizeof(resp), &xfer);
if (ret)
return ret;
req.row_idx = row_idx;
req.hw_write_lock = hw_write_lock;
req.hw_read_lock = hw_read_lock;
req.row_soft_lock = row_soft_lock;
DMSG("row_idx: 0x%x", req.row_idx);
DMSG("hw_write_lock: 0x%x", req.hw_write_lock);
DMSG("hw_read_lock: 0x%x", req.hw_read_lock);
DMSG("soft_lock: 0x%x", req.row_soft_lock);
ret = ti_sci_do_xfer(&xfer);
if (ret)
return ret;
return 0;
}
int ti_sci_get_otp_row_lock_status(uint8_t row_idx, uint8_t *global_soft_lock,
uint8_t *hw_write_lock, uint8_t *hw_read_lock,
uint8_t *row_soft_lock)
{
struct ti_sci_msg_req_get_otp_row_lock_status req = { };
struct ti_sci_msg_resp_get_otp_row_lock_status resp = { };
struct ti_sci_xfer xfer = { };
int ret = 0;
ret = ti_sci_setup_xfer(TI_SCI_MSG_GET_OTP_ROW_LOCK_STATUS, 0,
&req, sizeof(req), &resp, sizeof(resp), &xfer);
if (ret)
return ret;
req.row_idx = row_idx;
ret = ti_sci_do_xfer(&xfer);
if (ret)
return ret;
*global_soft_lock = resp.global_soft_lock;
*hw_write_lock = resp.hw_write_lock;
*hw_read_lock = resp.hw_read_lock;
*row_soft_lock = resp.row_soft_lock;
return 0;
}
Regards,
Li