Tool/software:
Hi TI,
we have currently an issue with PCIE2_DAT0 on TDA4. We are using ti-uboot-2023.04 to bring the TDA4 until u-boot stage, which then loads and starts the firmware for mcu2-0.
The pcie module index 2 is configured to access memory of another board with TDA4 via PCIE2_DAT0 region.
The issue is, that I can not access PCIE2_DAT0 region from mcu2-0. Following summarizes what I have tried so far:
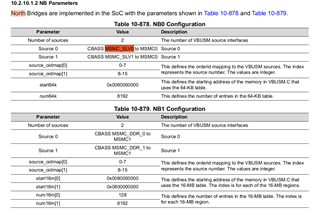
1. PCIE2_DAT0 memory is located within 48-bit address space. (0x4400000000)
The RAT unit of mcu2-0 is configured to map this memory region (0x4400000000) into ARMSS_RAT_REGION2 address range (0x10000000)
I connect CCS to mcu2-0, and use the memory browser to read from the mapped memory region (0x10000000).
Result: I get "?" in Memory Browser view and it looks that the TDA4 has crashed.
CCS Output: MAIN_Cortex_R5_0_0: Error: (Error -1170 @ 0x0) Unable to access the DAP. Reset the device, and retry the operation. If error persists, confirm configuration, power-cycle the board, and/or try more reliable JTAG settings (e.g. lower TCLK). (Emulation package 20.0.0.3178)
MAIN_Cortex_R5_0_0: Unable to determine target status after 20 attempts
MAIN_Cortex_R5_0_0: Failed to remove the debug state from the target before disconnecting. There may still be breakpoint op-codes embedded in program memory. It is recommended that you reset the emulator before you connect and reload your program before you continue debugging
2. Try to avoid any RAT configuration issues and using the A72 core to peek into PCIE2_DAT0 region:
I connect CCS to a72 and use memory browser to read from memory region 0x4400000000.
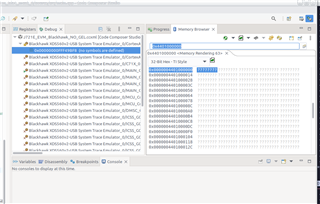
It just shows "?" (cannot read from that address) but this time, the TDA4 is not crashing like from R5.
Note: The "Memory View" is set to "CPU Memory View".
3. Same as 2, but this time I set Memory View of Memory Browser to "Physical Memory View".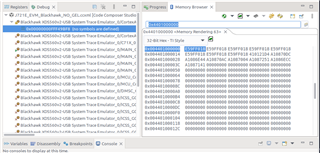
Now I can see the data from the other board. (It works!)
The conclusion for me is, that the PCI configuration/access in general is working. But there is an general issue of accessing PCIE2_DAT0.
Can you please help me here? Our final goal is to access it from mcu2-0.
Thank you and best regards,
Thomas