Tool/software:
Hi TI experts,
we develop a product with the AM64x EVM as reference design. For firmware updated we use swupdate (recovery image method).
On boot u-boot must decide which image to boot (recovery / normal image), and therefore the u-boot environment has to be modified when an update is initiated / finished.
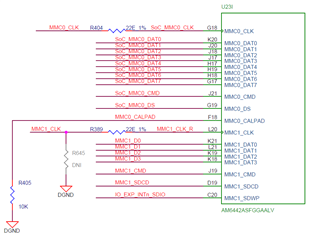
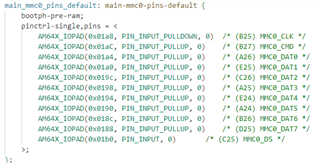
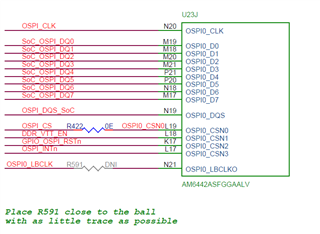
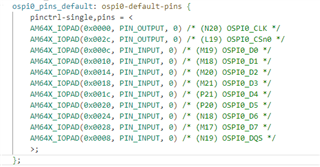
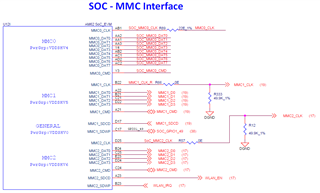
For increased robustness, we want to use the redundant environment, both stored in the boot partition of the eMMC (mmcblk0 boot0). Therefore I modified the files configs/am64x_evm_a53_defconfig and configs/am64x_evm_r5_defconfig
As a reference I used the information provided by TI: software-dl.ti.com/.../UG-Memory.html
After build and flash the image (tisdk-default-image), the R5-SPL (contained in tiboot3.bin) hangs after producing the following output:
------
U-Boot SPL 2024.04-ti-g50481472c910 (Dec 04 2024 - 10:01:28 +0000)
Resetting on cold boot to workaround ErrataID:i2331
Please resend tiboot3.bin in case of UART/DFU boot
resetting ...
U-Boot SPL 2024.04-ti-g50481472c910 (Dec 04 2024 - 10:01:28 +0000)
SYSFW ABI: 4.0 (firmware rev 0x000a '10.0.8--v10.00.08 (Fiery Fox)')
SPL initial stack usage: 13392 bytes
Trying to boot from MMC2
Authentication passed
Authentication passed
Loading Environment from MMC...
-------
After some debugging I realized that there exist different variants of the function static int env_mmc_load(void) env/mmc.c,
where the selection criterium is the define CONFIG_SYS_REDUNDAND_ENVIRONMENT.
Within the variant for redundant environment, the function mmc_initialize (NULL) (line 405) is called, and it seems that the loader crashes there.
This function is not called when compiling for single environment, which leads to the following output:
--------
U-Boot SPL 2024.04-ti-g50481472c910 (Dec 04 2024 - 10:01:28 +0000)
Resetting on cold boot to workaround ErrataID:i2331
Please resend tiboot3.bin in case of UART/DFU boot
resetting ...
U-Boot SPL 2024.04-ti-g50481472c910 (Dec 04 2024 - 10:01:28 +0000)
SYSFW ABI: 4.0 (firmware rev 0x000a '10.0.8--v10.00.08 (Fiery Fox)')
SPL initial stack usage: 13392 bytes
Trying to boot from MMC2
Authentication passed
Authentication passed
Loading Environment from MMC... *** Warning - No MMC card found, using default environment
--------
The environment could not be loaded either, but at least the boot process continues.
So my questions are:
1. Is my approach a valid one? Would you recommend using a second environment in my use case?
2. Can you tell why the mmc_initialize() function leads to a frozen system? I run a test with the line commented, and the system booted as if I had only a single environment.


diff --git a/configs/am64x_evm_a53_defconfig b/configs/am64x_evm_a53_defconfig index 7312d3ae242..fe7c19b377e 100644 --- a/configs/am64x_evm_a53_defconfig +++ b/configs/am64x_evm_a53_defconfig @@ -12,7 +12,15 @@ CONFIG_K3_ATF_LOAD_ADDR=0x701c0000 CONFIG_TARGET_AM642_A53_EVM=y CONFIG_HAS_CUSTOM_SYS_INIT_SP_ADDR=y CONFIG_CUSTOM_SYS_INIT_SP_ADDR=0x80480000 -CONFIG_ENV_SIZE=0x20000 +CONFIG_ENV_IS_IN_MMC=y +# CONFIG_ENV_IS_NOWHERE is not set +CONFIG_SYS_MMC_ENV_DEV=0 +CONFIG_SYS_MMC_ENV_PART=1 +CONFIG_SYS_REDUNDAND_ENVIRONMENT=y +# CONFIG_USE_ENV_MMC_PARTITION is not set +CONFIG_ENV_OFFSET=0x700000 +CONFIG_ENV_OFFSET_REDUND=0x704000 +CONFIG_ENV_SIZE=0x4000 CONFIG_SYS_SPI_U_BOOT_OFFS=0x300000 CONFIG_DM_GPIO=y CONFIG_SPL_DM_SPI=y diff --git a/configs/am64x_evm_r5_defconfig b/configs/am64x_evm_r5_defconfig index 7a20a0e67d9..b3293d4ef4c 100644 --- a/configs/am64x_evm_r5_defconfig +++ b/configs/am64x_evm_r5_defconfig @@ -10,8 +10,6 @@ CONFIG_SOC_K3_AM642=y CONFIG_TARGET_AM642_R5_EVM=y CONFIG_HAS_CUSTOM_SYS_INIT_SP_ADDR=y CONFIG_CUSTOM_SYS_INIT_SP_ADDR=0x7019b800 -CONFIG_ENV_SIZE=0x20000 -CONFIG_ENV_OFFSET=0x680000 CONFIG_DM_GPIO=y CONFIG_SPL_DM_SPI=y CONFIG_DEFAULT_DEVICE_TREE="k3-am642-r5-evm" @@ -90,7 +88,12 @@ CONFIG_SPL_OF_LIST="k3-am642-r5-evm k3-am642-r5-sk" CONFIG_SPL_MULTI_DTB_FIT_NO_COMPRESSION=y CONFIG_ENV_IS_IN_MMC=y CONFIG_SYS_RELOC_GD_ENV_ADDR=y +CONFIG_SYS_MMC_ENV_DEV=0 CONFIG_SYS_MMC_ENV_PART=1 +CONFIG_SYS_REDUNDAND_ENVIRONMENT=y +CONFIG_ENV_SIZE=0x4000 +CONFIG_ENV_OFFSET=0x700000 +CONFIG_ENV_OFFSET_REDUND=0x704000 CONFIG_SPL_DM=y CONFIG_SPL_DM_SEQ_ALIAS=y CONFIG_REGMAP=y