Tool/software:
Hi Team
We are implementing secure boot on a AM64X based custom board. We want to use a HSM to keep our custom keys (SMPK, BMPK, SMEK, BMEK) secret.
We think we can accomplish this with respect to signing the bootloaders and the kernel. However, we found a fundamental flaw in the build process of the keywriter application.
In order to explain the flaw, we refer to the diagram here https://software-dl.ti.com/tisci/esd/10_00_08/6_topic_user_guides/key_writer.html?highlight=fek#procedure. This diagram suggests, that the SMEK and BMEK keys are AES encrypted with a temporary AES-256 key.
The SMEK and BMEK keys are used to AES encrypt the bootloaders and/or the kernel , see https://software-dl.ti.com/tisci/esd/10_00_08/6_topic_user_guides/secure_boot_signing.html#signing-an-encrypted-binary-for-secure-boot and must be therefore held secret.
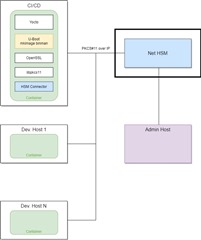
To accomplish this, we want to keep the SMEK and BMEK keys inside the HSM. However, if we do so, we are no more able to AES encrypt the keys. This is because encrypting the keys requires the keys to be extracted in plain from the HSM which is not (must no be) possible. Note that we want to use the PKCS#11 API to talk with the HSM. This API does not provide any means to AES encode data where the data is itself a key located in the HSM.
Any idea how to resolve this issue ?