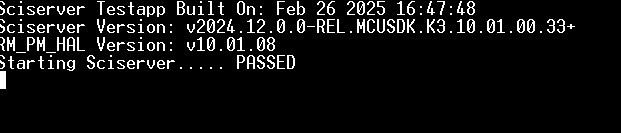
Tool/software:
Dear TI Experts,
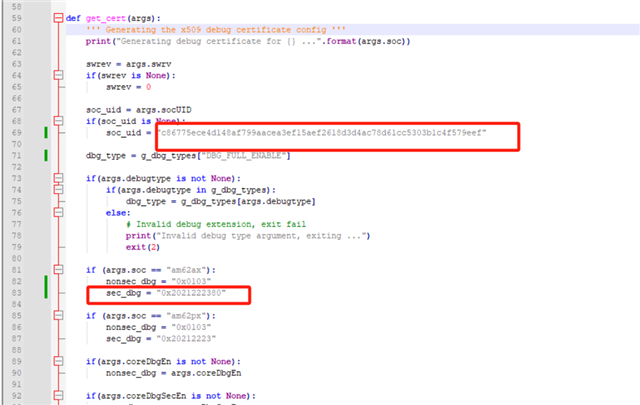
Throgh TISCI document I understand there are two methods for unlocking the debug port:
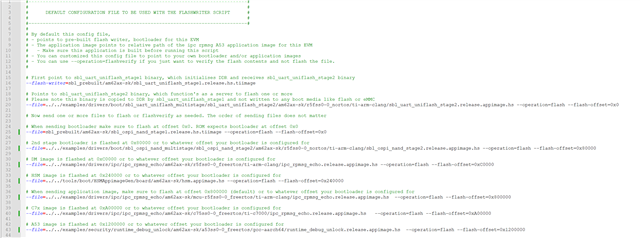
- Extending the SBL image with debug information.
- Using a certificate generated from the UID for unlocking the debug port.
However, I'm unsure of the exact steps required to implement them. Could you please provide guidance on how to generate the SBL image with the extended debug information, and how to generate the certificate for unlocking the debug port based on the UID?
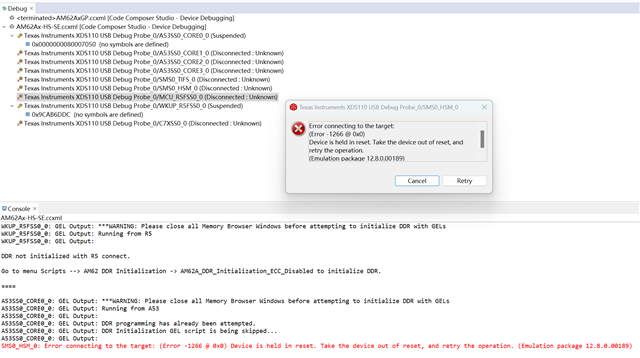
Additionally, I am aware that eFuse can be used to permanently lock the debug port, but I'm unclear on the exact process for this. Could you also provide details or reference material on how to do this as well?
Best regards,
Yang





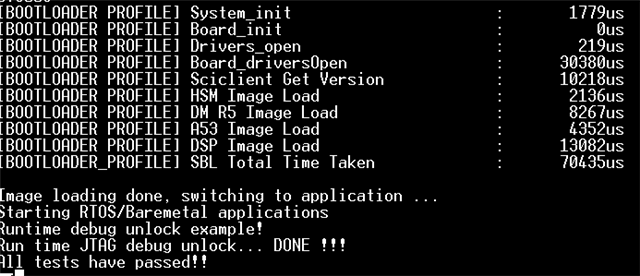
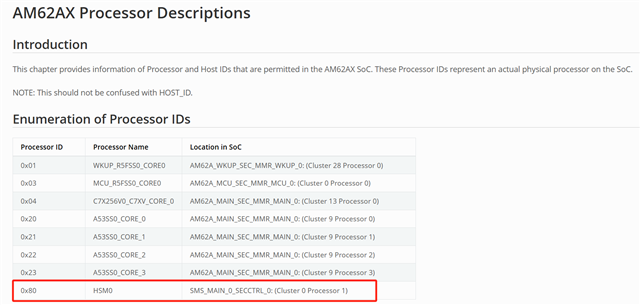
 .
.
 ;
; ;
; ;
;
 ;
;